In the epoch of uncontrollable ballistic shells, a saying emerged that “a bomb does not fall twice into a single funnel”. Since then, ammunition has appeared, with a corrected flight trajectory, and the saying has become to symbolize the hope that people can learn from the mistakes of others, and twice the
epic fail cannot happen by the same scenario. However, as they say, “never was this, and here again” ...
We still didn’t have time to properly forget the story from January 2017, when Strava fitness service
revealed the locations of US secret objects, as there was an even more epic failure of another similar service. The sports
application Polar Flow showed where the employees of secret military bases and other sensitive objects of particular importance live.
Surprisingly, the Polar Flow service gave even more data than was the case with Strava. Unfortunately, life has not taught anything to the employees responsible for protecting information in Polar. Now it was possible not only to limit the search for people involved in sports at secret sites. But, more importantly, to find out the full names of such people, and how often and where they trained before.

After the scandal with Strava, the Bellingcat research group, together with the Dutch publication De Correspondent, analyzed the work of other fitness services and found that the scale of the parasitic leakage of secret data from the Polar Flow service is even greater.
Polar Flow is an application that allows you to track and analyze daily physical activity, calories consumed, the duration of your workouts and the distance covered. In this case, the developers filed it as a social platform through which users can, including, share the routes of their running and walking workouts.
In particular, all activity is displayed on a map called
Explore . Displaying all the workouts on one map, Polar not only reveals some medical indicators, routes, dates, time and duration of users' exercises, but also coordinates of their place of residence and work - users usually turn on their fitness trackers when they leave home, most revealing their place of residence on the map in clear text.

It was quite easy to track the information even to an unqualified lover of other people's secrets right on the site: you need to find a property with a special status (already known to you or carefully
hidden by a black square on the online maps at the request of the state), select one of the tracks “athletes” by proximity, determine the profile associated with the jogging track and see where else this user is training.

So you can find other
interesting places by applying minimal deductive abilities. The more athletes you analyze, the more confidential information you will be able to end up collecting. In their profiles, users often specify real names, photos, even if they have not connected their profiles from other social networks to the Polar entry.
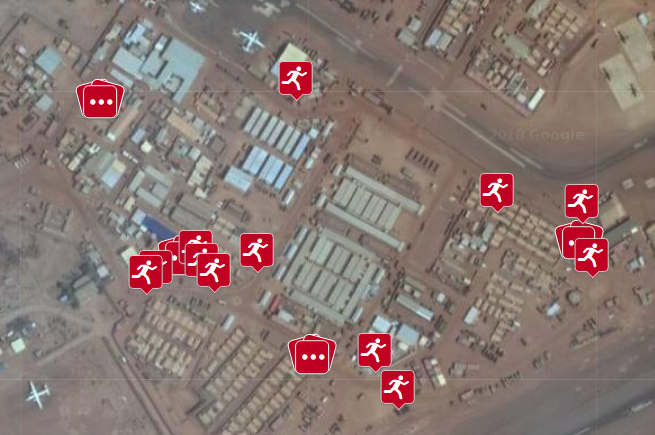
Analysts Bellingcat went much further and took up the API for developers. It turned out that through it a potential intruder could view user data with even greater convenience, even those that are hidden by privacy settings. The API had no restrictions on the number of hits, so almost anyone could collect information about millions of Polar Flow users and subject it to data mining.
 Track man from the building of the British agency MI6, image De Correspondent
Track man from the building of the British agency MI6, image De CorrespondentAfter the journalists contacted Polar, the company made a formal apology and reported that it had disabled the tracking functionality and was already dealing with the problem.
However, by analogy with the
“leakage” of “Google accounts” through Yandex.Search , Polar stated that it does not consider the leakage really serious:
It is important to understand that there were no data leaks, including personal ones. At the moment, most users of Polar have private privacy settings, so the problem does not apply to them. Whether to share training and location data is the choice of each user, but we are notified that the information about potentially secret places was public, so we decided to temporarily close the Explore API
.
In turn, the Bellingcat researchers expressed their concerns:
In some countries, soldiers were forbidden to wear a uniform on the street so that potential adversaries could not calculate them - and now anyone with access to the Internet and sharpness can learn their addresses and habits how to use the Polar website correctly. It is easy to find out the time of deployment [of the military unit], place of residence, photograph and the role of the soldier in the conflict zone. You don't need a lot of imagination to realize how this information can be used by extremists or government intelligence services.