
We continue our series of lessons on Check Point. This time we will discuss one of my favorite topics, namely,
IPS (Intrusion Prevention System). In Russian - an intrusion prevention system. And the emphasis is on Prevention (i.e. prevention)! One of the main credos of Check Point is: “
We Prevent, not detect! ". Personally, I agree with this position. What is the use of detective if you were attacked by a coder for example? The encrypted computer will tell you that there was an attack. In the current reality, you need to take care of Prevent. And IPS can help very well here.
However, in recent times there has been a certain neglect of this class of protection, saying “
IPS is no longer relevant and it makes no sense to use it ”. In my opinion this opinion is an unforgivable mistake. Actually in this lesson I will try to describe the main current misconceptions about the IPS. Then, as part of the laboratory work, I will show how IPS will help strengthen the protection of your network. And of course I will try to tell you how to get the most out of this useful tool, what settings to pay attention to and what you need to remember, including IPS.
The lesson was very long, so I broke it into two parts. The first part will be purely theoretical, and the second is already fully devoted to the practice in the form of laboratory work. Hope it will be interesting.
Spoiler - At the end of the article video lesson, if someone is more comfortable to watch, not read. Brief history of the development of IPS
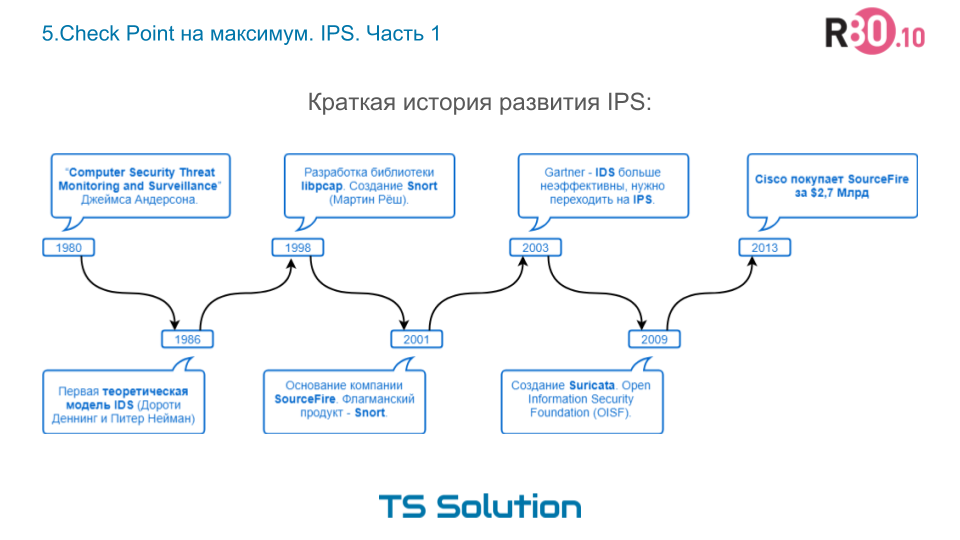
I would like to start with some historical features. In fact, IPS is a special case of
IDS (
Intrusion Detection System -
Intrusion Detection System or
IDS , as it is briefly called in Russia).
The idea of creating IDS appeared after the release of the article “
Computer Security Threat Monitoring and Surveillance ” by James Anderson, already in
1980 ! Quite an interesting article and most importantly relevant to this day.
6 years later, in
1986 , Dorothy Denning and Peter Neumann published the first
theoretical model IDS , which probably still is the basis for modern systems. Further, there were quite a lot of different developments, but they all mostly boiled down to using three intrusion detection methods:
- Signature analysis;
- Heuristic analysis;
- Anomaly detection.
Perhaps one of the key moments in the development of IDS was the emergence of the
libpcap library in
1998 . Developed her guys from the National Laboratory. Lawrence in Berkeley. In the same year, an
APE packet sniffer using the libpcap package was developed. A month later, APE was renamed the well-known
Snort . Snort's author is
Martin Resch .
Later,
Sourcefire was founded (in 2001) and the Snort project continued its rapid development within the framework of Sourcefire and became in fact the standard among IDS solutions. Snort is open source, and this is what most modern vendors of information security solutions use (especially domestic companies).
In
2003 , Gartner noted the ineffectiveness of IDS and the need to switch to IPS systems (i.e., change detector to preventive). After that, IDS developers began to equip their solutions with the IPS mode. Snort can naturally work in both IDS and IPS mode (i.e., prevention).
Of course, it is also worth noting the rapid growth of another open source project -
Suricata . The project was founded by immigrants from Snort. The first beta release was in
2009 . Responsible for the development of the company Open Information Security Foundation (OISF). At the moment, Suricata is a very popular solution (although it is still inferior to Snort in popularity). In fact, they are quite often shared.
In
2013 , Sourcefire was taken over by
Cisco . At the same time, Snort continues to remain an open source project, and its commercial version is sold under the Cisco FirePower brand. With your permission, we will not talk about the differences between the free and proprietary versions. An interesting moment. Back in 2005, Check Point tried to buy SourceFire for $ 225 million, but the US government did not approve this deal. And as I said earlier, Cisco bought SourceFire in 2013 for as much as $ 2.7 billion. A good price increase for 8 years) more than 12 times.
Naturally, I listed only a small part of the solutions. At the same time, a huge number of commercial proprietary solutions developed (Check Point is one of them). Most often, IPS was part of a UTM or NGFW solution, less often as a stand-alone piece of hardware (Cisco IPS is a prime example).
IPS in corporate networks
Now, if we touch on the history of the spread of IPS solutions in corporate networks, we get something like the following picture:
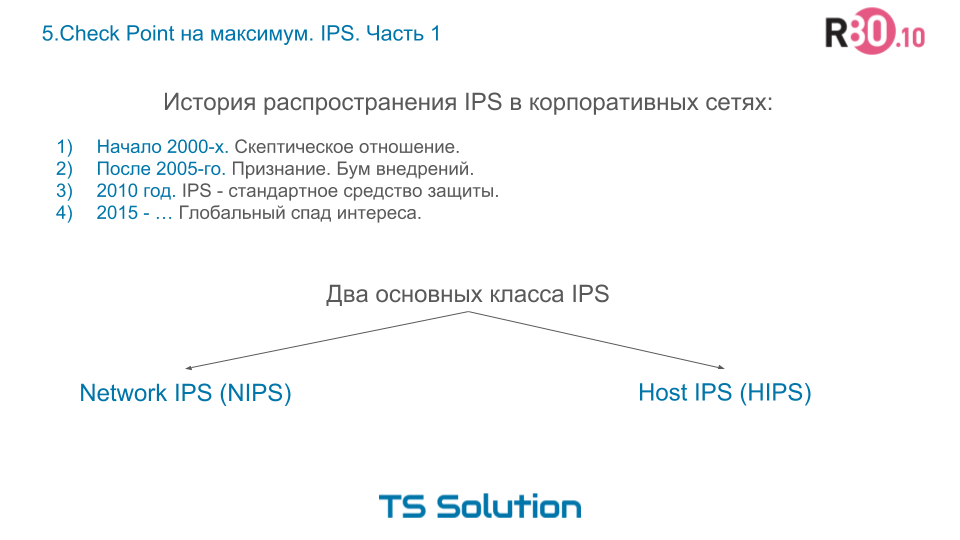
In the early 2000s, companies were very skeptical of this new class of security solutions. The majority considered IPS to be some kind of exotic thing, which is not really needed.
After 2005, the majority realized the benefits and necessity of IPS. Began the boom of deployments around the world.
By 2010, IPS has become an indispensable standard security tool for corporate networks.
Towards 2015, the IPS market is relatively cold. IPS under the standard was in almost all UTM / NGFW solutions. All switched to SIEM, protection against targeted attacks, sandboxes, sandpits, etc. At the same time completely forgetting about the importance of IPS. But we will discuss this a little further.
Now, when we have a little refreshed knowledge about the history of the emergence of IPS, I want to discuss another point. Namely IPS classes. In a rough approximation, all IPS solutions can be divided into two classes:
- NIPS operates at the network level, i.e. scans passing / transit traffic.
- HIPS operates at the user's computer level, i.e. with the traffic that is intended directly for this computer, well, either the host itself generates.
Today we will discuss the first option.
Two options for using NIPS
Let's look at the architectural use of IPS. Here, too, everything is quite simple, there are two options for using network IPS:
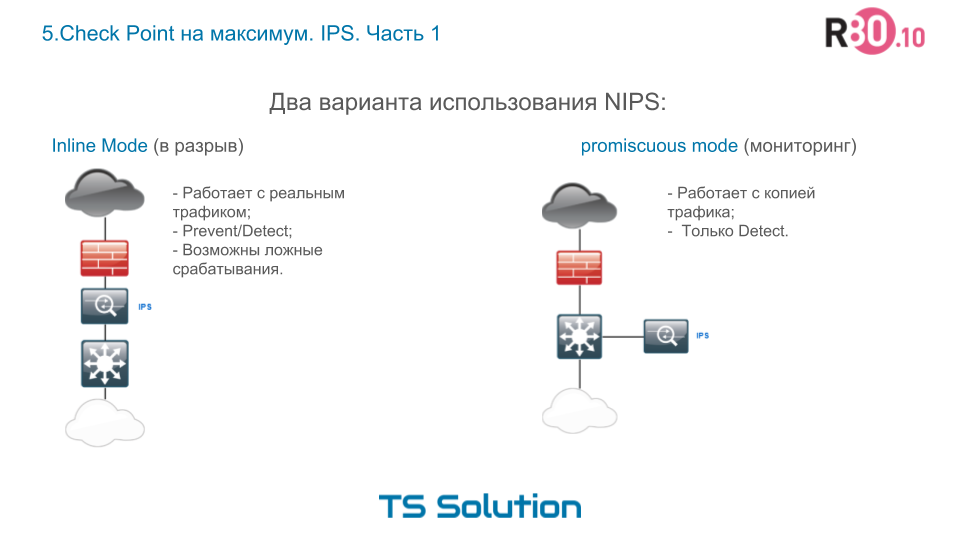
- Inline mode . In Russian, we call this a "break". Those. real network traffic goes through IPS. IPS in this case works as a normal bridge (that is, at the second level of the OSI model). This mode is the most optimal in terms of protection. If an attack is detected, the IPS can immediately block the session and the attacker's computer. There are, of course, negative aspects in the form of false-positive operations, i.e. false positives when IPS blocks normal traffic. But this is a separate topic, we will discuss it a little later.
- Promiscuous mode . Again, in Russian - the monitoring mode. As a rule, in this mode, IPS is “hung” on the SPAN port, which “mirrors” the COPY on the device! traffic. In this embodiment, the IPS automatically turns into IDS, because it no longer works with real traffic and it does not have the ability to block attacks quickly. Those. This is a bad option when maximum security is required.
We will not consider in detail the features of the application of a particular regime. This is a fairly extensive topic that goes beyond our lesson. Let's focus on the inline mode, because it is it that is used in most cases in Check Point.
IPS in UTM devices. Packet flow

From the point of view of processing traffic, packets are first checked by the firewall and if they are allowed by the appropriate accessory lists, then only the IPS is enabled and begins to check the passing traffic. Actually, this traffic processing algorithm reveals the conceptual difference between the Firewall and the Intrusion Prevention System.
“The
firewall seeks to prevent traffic from passing through. IPS works with already passed traffic . ”
This is logical not only in terms of security, but also in terms of performance. Why investigate traffic that can be quickly dropped by a firewall with minimal resource costs. This is the question of whether to put IPS in front of the firewall. Definitely not! Just imagine how much “left” traffic will pour on it from different bots that scan everything on the Internet.
Well, on this we end our protracted lyrical digression. Let's get down to the typical misconceptions about the IPS account. I will try to debunk them with the example of Check Point.
Typical misconceptions about IPS
1. IPS protects only against network level attacks.
Perhaps this is the most common myth. Historically, of course, IPS primarily protected against network attacks, such as port scanning, brute force, some types of ddos, and of course the fight against anomalies. But! Many still do not know that IPS can check and download files! And if the file contains exploit, then IPS will block its downloading faster than Anti-Virus, because IPS works in the traffic flow, and Anti-Virus has to wait until the entire file is downloaded to the buffer. Those. IPS scans files like pdf, doc, xls and more. I will definitely show this in the lab. Therefore, the included IPS will significantly enhance the protection of your users who download various files from the Internet. Do not neglect this additional level of protection!
2. IPS is no longer relevant and does not protect from anything.
Another popular myth. Of course, recently professional hackers have been trying not to use classic attack tools, such as port scanning, brute force, etc. And all because such attacks are immediately noticeable and generate a huge number of alerts on the classic means of protection. But! This is the place to be only with very complex and targeted attacks, when a true professional takes on the case. 99% of all successful attacks are automated bots that scan the network for known vulnerabilities, which they then exploit. IPS sees it all! Moreover, again remembering wannacry, after the discovery of this vulnerability, Check Point released an IPS-signature in just a couple of days. Microsoft released a patch much later (a couple of weeks as I recall). The included IPS with actual signatures perfectly reflects such automated attacks that still prevail (and it is unlikely that something will change in the near future).
3. IPS do not need to be updated frequently.
Actually in the previous paragraph, I stated that the included IPS with ACTUAL signatures provides protection against automated attacks. For some reason, many people think that only anti-virus databases need to be regularly updated, while completely forgetting about IPS. But the signatures for IPS appear or are updated literally every day. For example, you can use the
Check Point resource. As you can see, in the last couple of days, several new signatures have been released. Either the previously created ones have been updated.
IPS with current databases is very important. As I said earlier, IPS signatures come out faster than patches from vendors. If you have old signatures, then your IPS just threshes the traffic and uses up system resources aimlessly. And do not believe the domestic producers of OWs, who say that updating once a month is normal (as a rule, they put up such a period and most likely this is due to the fact that they use the snort database, which for the free version is updated with a delay of 30 days) .
4. IPS significantly reduces device performance
What can I say about this myth. Yes and no. Of course, the inclusion of IPS increases the load on both the processor and RAM. But all is not as dramatic as is commonly believed. A huge increase in load when IPS is turned on is usually manifested in two cases:
- You (or you) picked the wrong decision. Be it a hardware upgrade or a virtual solution. This is the question that everything needs to be tested before purchase. Again, much depends on who chooses the solution. Pay special attention to this. Use datasheets on devices carefully. There must be indicated the bandwidth of the device when the IPS is enabled. Well, again, Check Point has a sizing tool that gives very realistic recommendations for a suitable model. Be sure to use sizing! If you do not have access to this tool, ask your partners.
- The second and most common reason for increased load due to IPS is that too many signatures are included. This is one of the extremes of using IPS, when absolutely all available signatures are included, due to the fact that it is not initially clear which ones are needed. This is a very gross mistake that leads to simply wild loading of the device and a large number of false positives. Having tried this, many administrators decide to disable IPS, since with him, the border gateway simply “bends”. How to be? Well, first you need to determine what exactly you are going to protect. It is logical to assume that if you have a mail server on Linux in the DMZ, then you probably should not include for this segment the signatures associated with vulnerabilities of Microsoft, MacOS, Android, Wordpress, etc. I think the general meaning is clear. Thrashing traffic with all signatures indiscriminately is very expensive . In order for IPS to use resources efficiently, you need to turn on only the required signatures and turn off unnecessary ones. It sounds easy. But the implementation is very difficult. From here grows the next myth.
5. IPS hard to configure
In part, this is a fair opinion, which was the place to be. In fact, many IPS solutions are still very difficult to master. But this is not about Check Point. Let's take it in order. What does a signature usually look like? Typically, this is something like:
IGSS SCADA ListAll Function Buffer Overflow
WebGate Multiple Products WESPMonitor Stack Buffer OverflowAnd try to figure out what the signature is, why does it, will the gateway load the power on it, how critical is it? Fortunately, Check Point has a detailed description of each signature. The description can be seen directly in the SmartConsole and you do not have to google each name. Moreover, for convenience, Check Point assigned several tags to each signature:
- Severity (i.e. the level of danger this signature can close);
- Confidence level (confidence level of the signature, that is, what is the probability of the adequacy of the response of this signature. This is a very important characteristic especially for behavioral analysis)
- Performance Impact (this tag shows how strongly the included signature will load the device)
- Vendor - you can filter signatures by Vendor (for example, vulnerabilities associated with all Adobe or Microsoft products)
- Product - it is possible to filter by product (for example, Microsoft Office or WordPress).
Tags vendor and product sometimes overlap, because quite often the company has only one product.
Using these tags, you can quickly create a list of signatures that you want to include. And for this you do not need to have seven spans in the forehead. And of course, before this, you need to do a small network audit and understand what kind of software your employees use.
We will discuss the work with these tags in more detail in the laboratory work.
6. Work with IPS is tedious and routine work.
I have already said many times that information security is not a result, but a continuous process. You can not configure the system once and forget about it. Need continuous, systematic refinement. The same goes for IPS. And then there are usually difficulties. Practically any less adequate IPS system generates a huge number of logs. As a rule, they look like this:
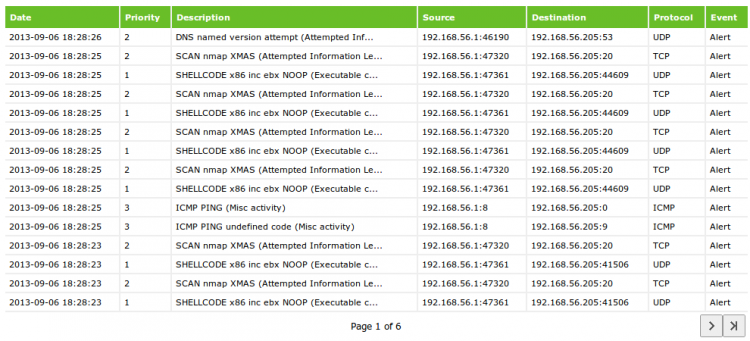
Now imagine that these logs accumulated several thousand a week. How do you analyze them? How to understand what events occur most often? What signatures might need to be turned off or what hosts might be blocked at the firewall level?
Of course, checkpoint logs look more attractive and clear:
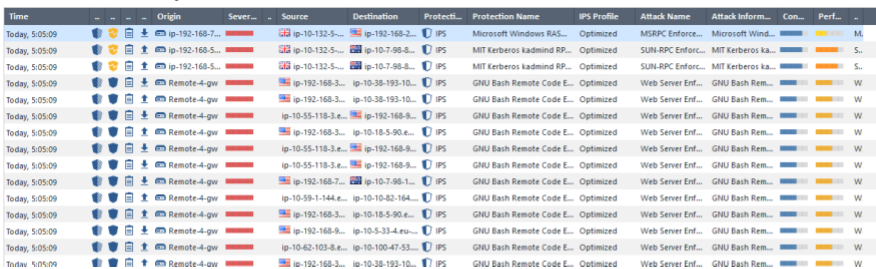
You can see both
Severity and
Performance Impact and
Confidence Level . However, this does not solve the problem of analyzing such a large number of events. As a rule, it is here that people remember about the SIEM systems, which are designed to aggregate, correlate and perform the primary analysis of events. Fortunately, Check Point has a built-in SIEM system -
Smart Event . This blade allows you to see IPS logs already in a processed and aggregated form:
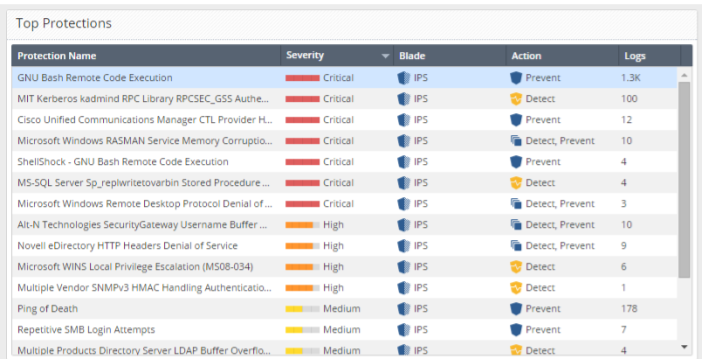
As you understand, it is already much easier to work with. The main value of SIEM is that this system allows you to “see” your security in quantitative terms. In any work you need to see the result and here it is much easier to focus on numbers. In our example, we see that there is a fairly large number of logs with
Severity level Critical . It is with them and you need to start work. Moreover, we see that the largest number of events is associated with the
GNU Bash Remote Code Execution signature. Analysis should start with these events. If we fail further, we can determine:
- What hosts are attacking?
- What host are attacking?
- What country is the attack from?
It may happen that the signature is triggered by the traffic that our internal node generates. This is a reason for the proceedings. Either it is really infected, or it is a false positive. Next, we either treat the host or turn off this signature specifically for this host.
If the attack comes from the external network, then maybe all these logs are created by just one attacking node (most likely it’s some kind of bot), and from some Singapore. In this case, we can add this host (or the entire Singapore network in general) to the block list so that it is blocked at the firewall level and does not reach the IPS traffic processing.
We can also notice that the signature catches attacks for linux distributions, while a windows host is probably attacked. In this case, it will also be logical to disable linux signatures specifically for this host.
As you can see, the process reminds some kind of investigation. After this constant optimization, the load on the gateway will be significantly reduced, because:
- Some of the attacking hosts will be blocked at the firewall level;
- Unnecessary signatures that consume resources will be disabled.
At the same time, SmartEvent allows you to immediately see the result in the form of a decreasing number of logs. This is exactly the quantitative characteristic that shows the effectiveness of our work. Ideally, we should get rid of the so-called “noise” and see only really important IPS events (i.e. real attacks) in the logs.
Moreover, this whole procedure of investigating and adding hosts to the block list can be automated! In R80.10, a full-fledged API appeared that allows you to integrate with third-party solutions. I already wrote an article on Habré about the API itself -
Check Point R80.10 API. Management through CLI, scripts and more.Also, my colleague Gleb Ryaskin published detailed instructions on the integration of Check Point and Splunk -
Check Point API + Splunk. Automation of protection against network attacks .
There is not only a theoretical part, but also a practical one, with an example of an attack and automatic addition of a host to the block list. Do not be lazy, look.
At this point, I propose to finish our theoretical part. In the next lesson we will have a big laboratory work.
The theoretical part of the video format
If you are interested in other Check Point materials, here you will find a large selection (
Check Point. A selection of useful materials from TS Solution ). You can also subscribe to our channels (
YouTube ,
VK ,
Telegram ), so as not to miss new articles, courses and seminars.
PS In the near future two interesting events will take place. Register:
More details about Extreme switch models can be
found here .