This year, the Positive Hack Days competition program has been replenished with the
MeterH3cker smart grid
hacking contest. The participants had a layout of two houses, according to the organizers' idea, the solar panels provided the houses with electricity, and the resulting surplus energy could be sold to the general electricity grid at a special rate. The task of the attackers was to disrupt the normal electricity metering process in any way possible and affect the cash balance in the billing system.
Stand
 Stand MeterH3cker
Stand MeterH3ckerModern homes equipped with solar panels, can both consume electricity, and give the excess generation back to the network. This model formed the basis of the stand MeterH3cker.
The stand was a model of two modern residential buildings with real equipment, which implemented elements of smart grid technology. Solar controllers, smart electricity meters and energy consumers were installed in each house. Both houses were connected to a model of an electrical substation on which a data collection and transmission device (DRC) was installed; it interrogated the counters and the substation counter.
In addition, each house was equipped with a heating and air-conditioning system, which was under the general control of a controller available in the common stand network. Also, a smart charging station for electric vehicles was installed near smart houses, which transmitted readings of its electric power consumption for a connected electric vehicle to the Data Administration Device.
We laid the day and night scenarios. In the "day" mode, the solar panels in the houses produced electricity, and their meters turned in the opposite direction and took into account the "consumed" and "given" energy. Each house had its own personal account, the balance of which increased with the generation of energy and decreased with consumption, and the tariffs set up in the meters also affected the values.
The main task of the contest participants was to increase the balance of the personal account of the houses, attacking the equipment of the stand, and thus get a direct financial benefit from their hacker actions.
To visualize the results, we wrote our own billing server, which collected data from the DRC. The DRC itself, in turn, interrogated the counters in several ways:
- the meter in house No. 1 - according to the open vendor Modbus-like protocol;
- the counter in house No. 2 was interrogated by the VR-007.3 device using an open vendor Modbus-like protocol, and then the DRCD received data from the VR-007.3 web server via HTTP;
- substation counter - via Modbus TCP protocol.
In order to obtain real energy consumption values, the same current and voltage circuits as the counters that were attacked were connected to reference meters that were not accessible to the attacker. The billing server directly polled them via the RS-485 interface.
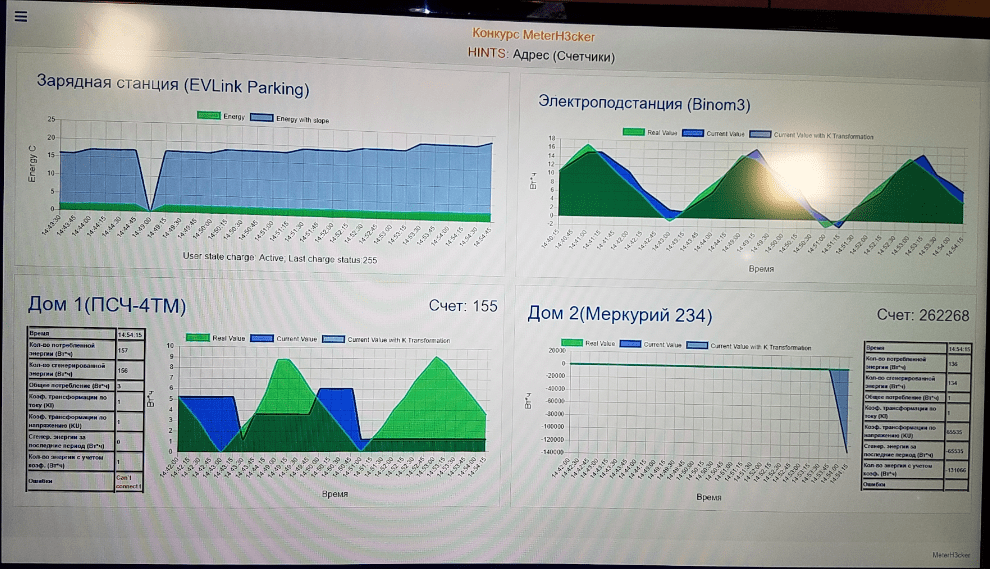
In order for the forum visitors to observe what was happening, a large monitor was installed next to the booth, in which electricity consumption graphs were displayed in real time. The graph of blue color marked readings with USPD. They varied depending on the actions of the attackers. The graph of green color showed real readings of generation and consumption of electricity collected from reference meters.
 Display of current values for each house: personal account balance, energy consumed and given to the network, tariff
Display of current values for each house: personal account balance, energy consumed and given to the network, tariffAn internal portal for the participants of the competition was also available on the stand network. It displayed the current values of the graphs, a section describing each element of the stand; there were published the rules of the competition and from time to time hints appeared.
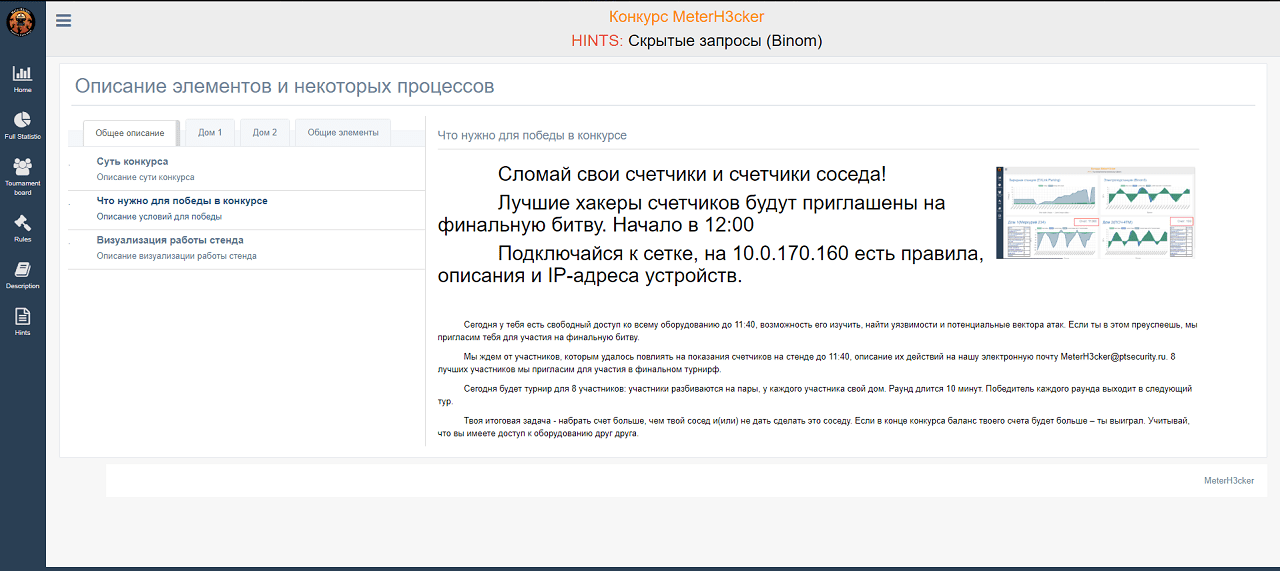 Internal portal
Internal portalThe terms of participation
The contest took two days. On the first day there were qualifying competitions. Each participant, when connected to the network of the stand, got access to all the equipment of the two houses, the substation and the charging station. Participants had the opportunity to explore equipment, find vulnerabilities and potential attack vectors. During the day, new prompts were periodically added to the internal portal of the competition, allowing participants to discover the weaknesses of the stand equipment. Participants who achieved success at the booth on the first day were invited to participate in the final tournament on the second day.
The final was a kind of duel. Two participants were invited to the stand, each of them had their own house. Their task is to fool the counters by any means during a ten-minute round and generate more energy than the enemy — the conditional neighbor. The one who had a greater personal account balance at the end of the competition won. At the same time, the task was complicated by the fact that the participants had access to each other's equipment, which means that they could harm their neighbors and underestimate their results.
Day One: qualifying round
There were a lot of people willing to try their hand at hacking equipment. We note that some of them were seriously prepared for the competition and had the necessary software with them. Among them were participants from Japan, who from the first hours of the competition carefully studied the stand, which allowed them to achieve significant results on the second day.
A big surprise for us was the participation of a 12-year-old hacking amateur: despite his age, he was able to navigate the equipment presented and demonstrated several attacks.
 Competitors
CompetitorsWe got the first results by the middle of the day: Japanese researchers joined forces to seize control of the charging station for electric vehicles and stop charging the electric vehicle by sending control commands via the web interface. A little later, they were able to pick up the administrator password of the solar battery controller and turn off power generation.
The young hacker did not lag behind adults either: he learned how to cause a continuous reloading of the RTU, thereby realizing the denial of service attack and breaking the meter survey.
Towards evening, one of the participants in the Japanese group achieved serious deviations between the values of the energies on the reference and attacked counters, greatly increasing the value of the counting. And his colleague discovered a vulnerability in the substation counter web interface that allows reading the contents of the device’s flash card files, one of which contained the administrator password hash. Thus, after successfully selecting a password, he gained access to the counter parameters.
An hour before the end of the qualifying round, a participant named Oleg joined the stand. Despite the fact that he had little time left, he managed to carry out a successful attack and get into the tournament, which was held the next day.
As a result, by the end of the day, all participants could change the energy readings on all available electricity meters and control the various elements of the stand - the controllers, the charging station.
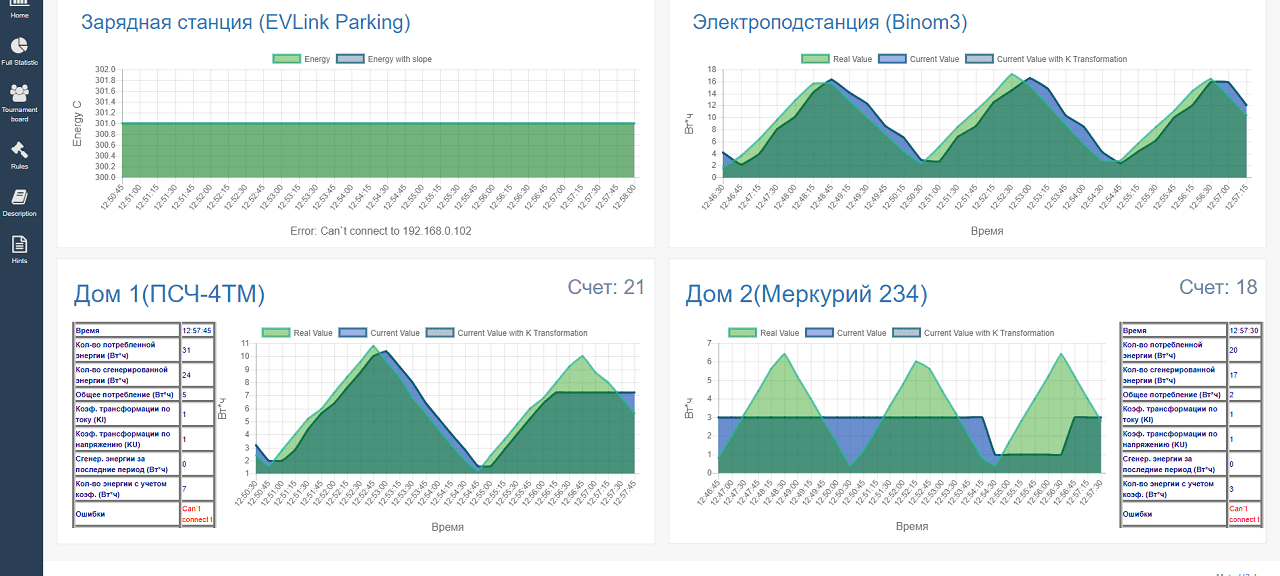
 The results of the attacks of participants on the counters. On the lower right graph, it is clear that the transformation ratio of the counter was changed, on the lower left - that a successful “denial of service” attack was made on the PSCh-4TM counter
The results of the attacks of participants on the counters. On the lower right graph, it is clear that the transformation ratio of the counter was changed, on the lower left - that a successful “denial of service” attack was made on the PSCh-4TM counterDay Two: Tournament and Final
According to the results of the reports sent by the participants at the end of the first day, we selected seven participants who could find and exploit vulnerabilities in the equipment of the stand.
Since on the second day, during the rounds, the participants could influence the readings not only of their meters, but also on the counterpart of their rival neighbors, any negligence could have serious consequences. Thus, the participant Oleg, conducting an attack on the equipment of his neighbor, mistakenly increased the account of his neighbor, because he carried out the attack at the time of generation, and then did not have time to “twist” it in the other direction during the remaining round. In subsequent fights, the participants took into account this sad experience and acted correctly, for example, set the maximum values of the coefficients of their counter during the generation period (“day” mode) and minimum values during the consumption period (“night mode”).
 Standings
StandingsIn the final of the competition a serious battle unfolded. At the beginning of the round, the advantage was for Satoru Takekoshi, who already in the first minutes was able to successfully carry out the attack and greatly increase the balance of his account. The second participant, Alexey Kuznetsov, was also able to launch an attack at the beginning of the round and increase the balance of his account, but to a much smaller extent. The gap in the readings of the generated energy was 25 GW · h against 5 GW · h. For most of the round, the score has not changed. Probably, in order not to repeat the sad experience of the first participants who attacked at the wrong time, Alexey behaved cautiously and tracked the change of regimes. In the second half of the round, he managed to carry out a successful attack on the meter of the electrical substation and make the minimum distance from his neighbor, but the total score still did not allow him to win. In the last seconds, Alexey again attacked his counter and successfully increased his readings, which allowed him to snatch the victory from the leader. Thus, Alexey won, increasing his balance to 92 billion y. e., and in view of his successful attack on the meter of an electrical substation, his total score allowed him to unconditionally win.
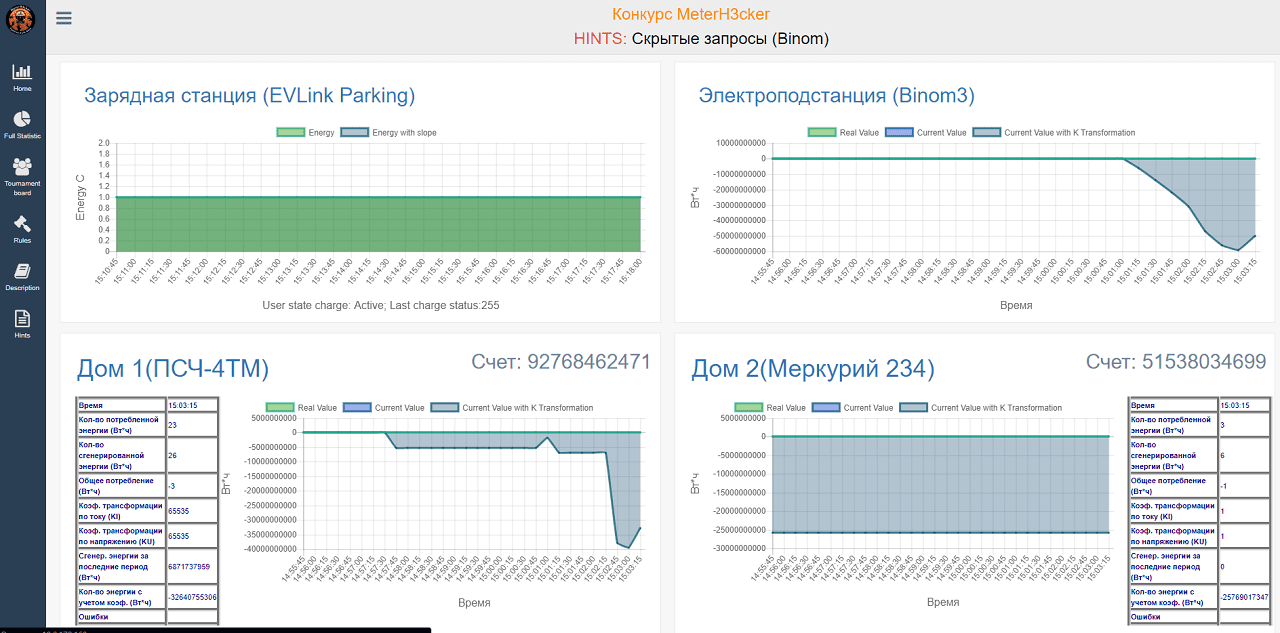 The state of personal accounts in the last seconds after the final attack
The state of personal accounts in the last seconds after the final attackResults
So, the winners: 1st place was taken by Alexey Kuznetsov, 2nd place went to Satoru Takekoshi, closed the top three Nikita Stupin. Special prize, for the 4th place, received a young hacker Yuri Grishin.
During the competition (especially in the final tournament) completely different attacks were demonstrated. Most of the participants tried to carry out attacks on the energy readings taken from the meters, to increase the energy production at the time of generation and to reduce at the time of consumption. Also in some rounds, competitors successfully attacked a charging station for an electric vehicle and a solar battery controller.
However, none of the participants was able to conduct successful attacks on the USPD and replace the collected data directly on it. Potentially, these attacks could lead to complete control of the data transmitted to the billing center and an increase in their accounts by an arbitrary value. For all two days, we recorded only one such attempt to attack, which, apparently, ended in failure.
Also, no one attacked the controller that controls the heating and air conditioning system. It was assumed that the attacker would connect to the device and be able to control the equipment using existing control signals. The main difficulty for attackers was to map open ports and equipment name, for example, to request information using the FOX protocol. To attack this equipment it was not necessary to use specialized software. The hint didn’t help either, because the attackers didn’t use it, but all they needed was to change the User-Agent header in their browser for a successful connection.
From other observations. During the competition, the contestants asked many clarifying questions on the structure and operation of the stand, as well as on the available devices. This can be explained by the fact that, in addition to the task of “breaking down” devices, it was necessary to understand what each of them does and how to exploit its vulnerabilities in order to obtain benefits.
 The height of the first day
The height of the first dayWe were pleased that although our competition was new to the forum, many viewers came who were not going to participate, but were interested in the work of the stand, the successes of the contestants. Free ottomans in front of the stand quickly ended!
Another interesting fact is related to participants from Japan. The internal portal of the competition and the documentation of devices of domestic manufacturers were in Russian, nevertheless it did not become an obstacle for the Japanese team - practical skills were enough to demonstrate a series of successful attacks. However, after the competition, they admitted that it still gave them some inconvenience.
In general, the competition showed that in less than two days it is quite possible to understand modern electricity metering systems and execute successful attacks on them.
Analysis of other competitions Positive Hack Days 8: