
Last week was marked by a couple of interesting news from the unsafe world of Internet things, and the main event, of course, was the study of smart lock Tapplock (
news ,
original report ). Andrew Tierney, a Pen Test Partners researcher, did not just bypass the electronic lock protection, but rather discovered the complete absence of any security system in the “digital” part of the device.
Tapplock castle was first shown as a concept in 2016, at the same time the creators of the device launched a campaign on
Indiegogo , planning to collect 40 thousand dollars for bringing finished prototypes to mind and release the first batch of devices. "The world's first smart lock with a fingerprint scanner" promised an incredible ease of being in the absence of heavy keychains in your pockets, connectivity to a smartphone and the ability to share access with friends, Bluetooth controllability and remote unlocking. At the same time: incredible security, including “military-grade” AES-128 encryption. And this lock must be charged.
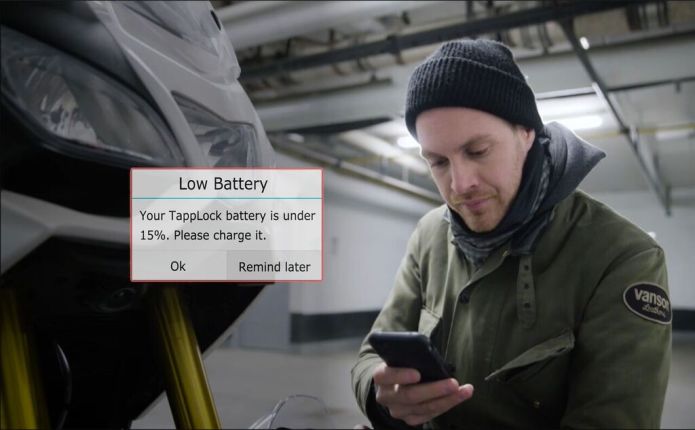
We, of course, know that proving the reliability by specifying an encryption standard is rather pointless, but let's not discuss the computer part right away, we have a means of ensuring physical security here. The history of this failure actually began with a clip on YouTube, on the popular JerryRigEverything channel, which is not about the Internet and security, but about the analysis of devices that came to hand. The author of the video clearly demonstrates how to bypass the encryption approved by the army with a screwdriver.
Andrew Tirney became interested in this video, bought a lock ($ 84 on the
official website ) and first discovered that youtube screwdriver star seems to be wrong. Andrew didn’t work out to disassemble the lock in the same way as the previous burglar did, despite the application of a tightly glued lever from the holder for GoPro and other improvised means to the inside lid. Apparently, there was a defective sample, and Tapplock's reputation was fully restored. Yes?

Not! A pity, so many good jokes were wasted. Well, the initial assertion of the developers of the castle about the highest level of security is generally doubtful: it's the usual small lock, albeit with a battery. No need to crack AES, medium-sized bolt cutter and so cope. The researcher Andrew Tierney decided to look at the digital part and first discovered that the lock communicates with the smartphone via bluetooth via HTTP, without using encryption (although the same AES-128 was originally announced for the bluetooth part!). The traffic analysis allowed us to identify the line that identified the device as trusted, and it remained unchanged in all cases. Using the very function of “sharing with a friend,” you, in fact, give him a fixed “password”, which then, it turns out, cannot be revoked. Moreover, it became clear further that even the complete unlinking of the lock from the owner’s phone (for resale, for example) did not change the authorization code.
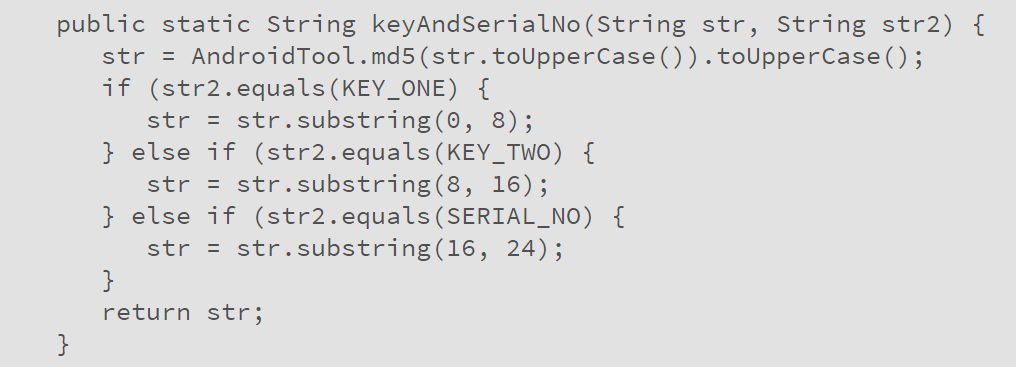
How? That's how. Finally, the way of generating this very code helped break the illusion of protection. As it turned out, all you need is the MAC address of the integrated Bluetooth Low Energy module. The same MAC address that the module broadcasts to everyone. As a result, it is possible to hack any Tapplock nearby (within the bluetooth range), in seconds, remotely and easily. The researcher notified the manufacturer, and there they answered something like: “Thank you,
and we are in the know .” Considering that this is not even a vulnerability and the method of circumventing the protection lies on the surface, Andrew set an unusual deadline before the disclosure of information in seven days, after which the study was published. Tapplock responded with a vague promise to release an
update . Later, full processing of the software was promised, and there seems to be even a theoretical possibility to rectify the situation - the matter is not hardware. Can you fix the reputation? We'll see for now that Tapplock devices are still on sale, despite the rather wide coverage of the problem in the media.
By the way, about bankruptcies due to vulnerabilities. Last year, we wrote about the
vulnerabilities of toys with Internet connection, produced under the brand Cloudpets. In that story, there was zero protection already familiar to the IoT world, and even with the leakage of very private data, well, and exotic comments of the management in the style of “this is normal, everyone does that”.
So, since then, the toy manufacturing company has closed, but the security problems of the devices already sold have not gone away. Moreover, researchers have found a couple of new holes in them (
news ), toys continue to knock on the domain for synchronization, which is put up for sale and may be intercepted in the future. If you think about the millions of already sold IoT-devices with incomprehensible or missing protection, it becomes quite sad. The only “reason for optimism” is that so far not locks are attacking, and not bears with Wi-Fi, but routers, where everything is also very bad, but not so much. That's how we live.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.