Monitor high-profile victims while remaining in the shadows. This is the principle of the two malicious components InvisiMole. They turn an infected computer into an attacker video camera, which allows you to see and hear everything that happens in the office or in any other place where the device is located. InvisiMole operators can easily connect to the system, monitor the victim’s actions and steal her secrets.
According to the ESET telemetry, the attackers behind this
spivary have been active since at least 2013. However, this
cyber espionage tool was not only not studied, but was not detected until ESET products were detected on infected computers in Russia and Ukraine.
The campaign is highly targeted, which explains the low infection rate - just a few dozen computers.
InvisiMole has a modular architecture, begins its path with a DLL wrapper (wrapper DLL), then there are two modules embedded in its resources. Both modules are multifunctional backdoors, allowing Malvari to collect as much information as possible about the target.
To divert the user's attention from the infected machine, additional measures are taken. This allows the malicious program to remain in the system for a long time. We have yet to establish the vector of infection - currently all options are possible, including manual installation if you have physical access to the machine.
Installation and Persistence
The first part of the Malvari under study is a DLL wrapper compiled with the
Free Pascal Compiler. According to our telemetry data, the DLL is placed in the Windows folder and disguised as a legitimate
mpr.dll file with fake version information.
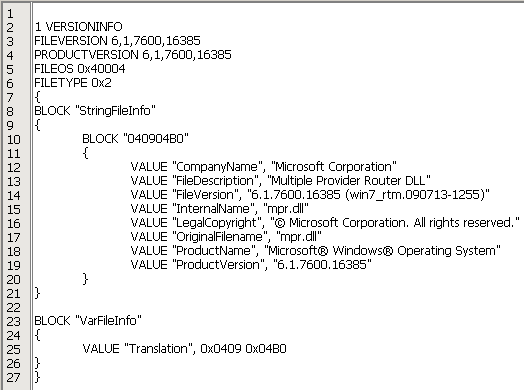 Figure 1. The DLL wrapper is disguised as a legitimate mpr.dll file, copying the name and version information
Figure 1. The DLL wrapper is disguised as a legitimate mpr.dll file, copying the name and version informationWe have not seen samples with other wrapper names, although the DLL code indicates that the file may also be called
fxsst.dll or
winmm.dll .
The first way to start Malvari is DLL substitution technique (DLL hijacking). The DLL wrapper is placed in the same folder as
explorer.exe , and is loaded when Windows starts along with the Windows Explorer process instead of the legitimate library located in the
%windir%\system32 .
We found 32-bit and 64-bit versions of Malvari, which ensures persistence in both architectures.
As an alternative to replacing the DLL, other methods of loading and ensuring persistence are possible. The DLL wrapper exports the
GetDataLength function. When this function is called, the DLL checks whether it was loaded by the
rundll32.exe process using
explorer.exe or
svchost.exe as the parent process, and only after that it starts the payload. This suggests other possible methods of ensuring persistence - submitting tasks to the scheduler (parent process -
svchost.exe ) or writing to the registry autorun key (parent process -
explorer.exe ).
Regardless of the method of ensuring persistence, the behavior of the malicious program and the payload itself are the same in all cases. The DLL wrapper loads the module stored in resources under the names
RC2FM and
RC2CL , and (if a DLL substitution is used) the legitimate library in the
explorer.exe process, so as not to disrupt the normal operation of the application and go unnoticed.
 Figure 2. Exported DLL wrapper functions
Figure 2. Exported DLL wrapper functionsTechnical analysis
The exact date of the malware compilation is unknown - the latest samples of the DLL wrapper are changed by the authors, the PE timestamps are manually reset. However, during the study, we found an earlier version, dated October 13, 2013, so the new versions are clearly compiled later.
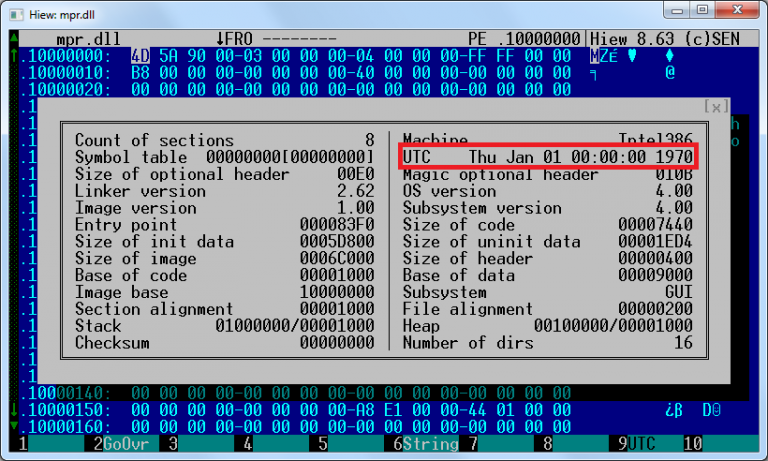 Figure 3. In all later samples, time stamps are set to zero.
Figure 3. In all later samples, time stamps are set to zero.Encryption and decryption
To conceal from virus analysts and system administrators, the authors of the malware use encryption of strings, internal files, configuration data and network communications. While the
RC2FM module uses custom ciphers, the DLL wrapper and the
RC2CL module use one specific procedure for all purposes, including decrypting other malicious modules embedded in the DLL wrapper.
The script, with which you can select the built-in
RC2FM and
RC2CL from the DLL wrapper, is available in
the ESET repository on GitHub .
 Figure 4. Decryption procedure in different samples (decompiled and disassembled)
Figure 4. Decryption procedure in different samples (decompiled and disassembled)RC2FM module
The first, smaller
RC2FM module contains a backdoor that supports 15 commands. They are performed on the infected computer as directed by the attacker. The module can make various changes in the system, and also includes tools for cyber espionage.
The option of logging is implemented in the files, but the syslog name is not specified in the studied sample. This suggests that the function was used only at the development stage.
Network communication
This module communicates with C & C servers that are either hard-coded in the pattern, or later added by the attackers.
In addition, the module is able to access the C & C server, even if the proxy is configured on the infected machine. If a direct connection could not be established, the module tries to connect to any of its C & C servers using locally configured proxies or proxies configured for different browsers (Firefox, Pale Moon and Opera).
RC2FM can even check the list of recently used applications and try to find portable executable files of browsers:
FirefoxPortable.exe
OperaPortable.exe
Run waterfox.exe
OperaAC.exe
Palemoon-Portable.exe
If the victim uses one of these portable browsers
with a configured proxy server , the malware can detect it in user settings and use it to communicate with its C & C servers.
Communication with the C & C server is a series of HTTP GET and POST requests, as shown in Figure 5. The encrypted request contains a PC identifier and a timestamp, as well as some other information (optional). It is important to note that the
RC2FM module uses several encryption methods (simple XOR encryption options), unlike other InvisiMole components.
 Figure 5. Sample request sent to the C & C server by the RC2FM module
Figure 5. Sample request sent to the C & C server by the RC2FM moduleAfter successful registration of the victim on the C & C server, additional information is loaded into the system, which will be interpreted by the backdoor command.
Functionality
RC2FM supports commands for listing basic system information and making simple changes to the system, as well as several spyware features. At the request of an attacker, the module can remotely turn on a microphone on a compromised computer and record audio. The entry is encoded in MP3 format using the legitimate library
lame.dll , which is downloaded and used by malware.
Another data theft tool is screenshots. One of the backdoor commands is to create screenshots.
The malware monitors all internal and external drives displayed on the local system. When you connect a new disk, it creates a list with all the files and stores it in encrypted form.
The collected information will be transmitted to the attacker after sending the corresponding command.
Backdoor Commands
Below are the IDs and descriptions of supported commands. The visualization of the backdoor function in the interpreter is shown in Figure 6.
0 - Make lists of displayed drives, files in a folder, network shares
2 - Create, move, rename, execute or delete a file, delete a directory using the specified path
4 - Open the file, set the pointer to the beginning of the file.
5 - Close previously opened file
6 - Write data to previously opened file
7 - Change file time attributes / delete file
8 - Open the file, set the pointer to the end of the file.
10 - Change file time attributes / delete file
12 - Find files by specified file mask in the specified directory
13 - Take a screenshot
14 - Upload or edit files using internal data
15 - Record sound using connected audio devices, compile a list of available devices, send a recording, change the configuration
16 - Check for open files in the module.
17 - Update the list of C & C servers
19 - Create, install, copy, list or delete specified registry keys or values
 Figure 6. Backdoor interpreter function (original and after our analysis, modified using the Group Nodes function in IDA Pro for readability)
Figure 6. Backdoor interpreter function (original and after our analysis, modified using the Group Nodes function in IDA Pro for readability)RC2CL module
The
RC2CL module is also a backdoor with a wide list of espionage tools. It is launched by a DLL wrapper at the same time as the
RC2FM module. This is a more complex module, its functions, rather, are aimed at maximizing the collection of information than on making changes to the system.
Interestingly, the
RC2CL module provides the option to disable the backdoor functionality and work as a proxy. In this case, the malware disables the Windows firewall and creates a server that supports communication between the client and the C & C server or two clients.
Network communication
Malware communicates with C & C servers via a TCP socket. Messages sent by the client are disguised as HTTP, but you should pay attention to the invalid HTTP method "HIDE" in the example in Figure 7.
Requests include the identifier of the compromised software, the type of request and the encrypted information that is to be sent by the attacker, that is, the result of executing backdoor commands or a request for new instructions.
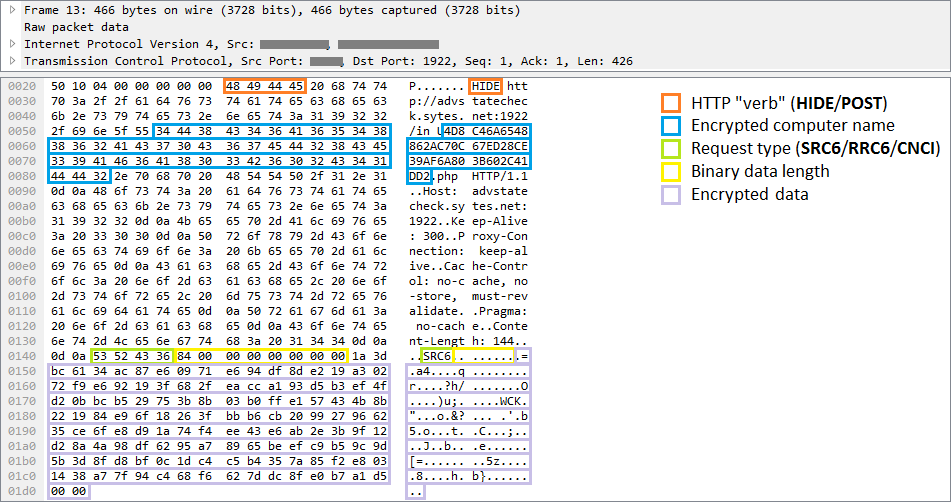 Figure 7. Sample request sent to the command server by RC2CL module
Figure 7. Sample request sent to the command server by RC2CL moduleFunctionality
Depending on the command received, the backdoor can perform various operations on the infected system. Regular backdoors perform file system and registry key manipulations, support file execution and remote shell activation. This spyware supports all these teams and even more - 84 teams allow attackers to gather comprehensive information about the victim.
The malware scans the infected computer and sends various data to the attacker: system information (list of active processes, running services, loaded drivers or available drives), network information (table of IP addresses, Internet connection speed).
InvisiMole can scan wireless networks available on a compromised system. Spyware records information such as the SSID and MAC addresses of detected Wi-Fi access points. This data can then be checked against public bases, which allows the attacker to track the geolocation of the victim.
Other commands allow you to get information about the users of the compromised machine, their accounts and previous sessions.
Of particular interest is the software installed on the compromised machine. What programs are installed in the system? Which of them automatically start when the system starts or when a user logs in? What programs does a particular user use? If the attackers are interested in something, just enter one command to get the necessary data.
Malware can receive a command to search for recently opened documents and other interesting files. It can view specific directories and external devices, report changes and extract files selected by the attackers.
Malware can enable or disable the account management system (UAC), or bypass it and work with files in secure directories without administrator rights (for more information,
click here ). If the malware is running under the
explorer.exe process, which automatically gains elevated rights, it can create a COM object and use it to delete and move files in areas that require administrative rights.
Moreover, InvisiMole can remotely turn on the webcam and microphone of the victim, spy by photographing or recording. Attackers can monitor the activity on the device by taking screenshots. What is particularly interesting, InvisiMole allows you to take screenshots of not only the whole screen, but also of each open window. This allows attackers to collect information, even when the windows close each other.
One of the backdoor commands allows you to replace the contents of the drivers with the following names:
blbdrive.sys
compbatt.sys
secdrv.sysWe did not observe the use of this command by attackers, but we can assume that it is used to provide additional persistence on 32-bit systems.
The backdoor is capable of interfering with the system (for example, logging off for the user, terminating the process, or shutting down the system), but mainly ensures the execution of passive operations. The program, if possible, tries to hide its activity.
So, spyvary explores interesting places in the system, examines recently opened documents or modifies some files. These actions leave traces and may cause the suspicion of the victim, since after each such operation the time of the last modification of the file and / or access to it changes. To prevent detection, the malware restores the date of the previous modification or opening of the file in order to hide its manipulations from the user.
Another example of how spiwari authors try to avoid detection is working with traces left on the disk. The malware collects a large amount of confidential data, which is stored for some time in files and deleted after successful uploading to C & C servers. The problem is that an experienced system administrator can recover deleted files, which will help in the investigation of the attack after the victim finds out about the compromise. This is possible because some information remains on the disk even after the file is deleted. To prevent this, InvisiMole has the function of safely deleting all files. This means that data is first overwritten by zero or random bytes, and only after that is the deletion of the file.
Internal memory
The backdoor configuration and the collected data are stored at two addresses - this is the working directory and registry keys. A significant part of the backdoor commands is designed to manipulate these storage locations and their contents.
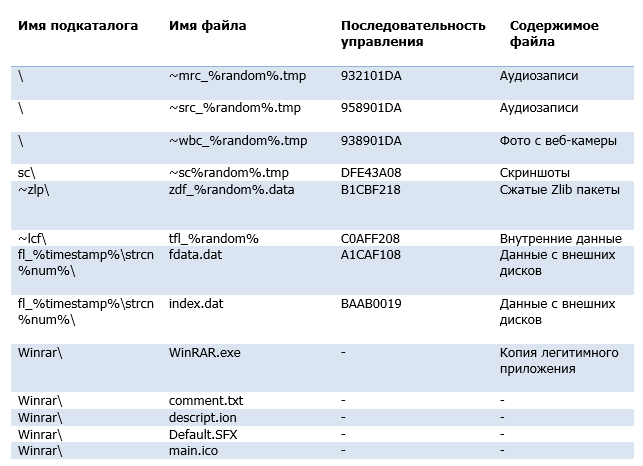
The location of the working directory is determined by commands from a remote server. The directory is used as a temporary storage of files containing information collected from a compromised computer. These files have a common naming convention, encryption algorithm, and structure. They are encrypted by a simple version of the XOR cipher, which is used in the components of Malvari. The file type can be obtained from the 4-byte check sequence located at the beginning of the file.
In addition to storing the collected data, the directory is used as a home for a copy of the legitimate WinRAR.exe application. Malware copies it and uses it to archive stolen data.
The registry stores configuration data, as well as a list of files in the working directory. The data is packed using the Zlib procedure implemented in the binary file of Malvari and encrypted using the same cipher as the internal files.
Backdoor Commands
More than eighty backdoor commands use the working directory and registry keys to store intermediate results and configuration data. The graph with the backdoor display in the interpreter is shown in Figure 8.
About a third of all commands relate to reading and updating configuration data stored in the registry. IDs and descriptions of the remaining commands are listed below.
4 - Make a list of information about files in a directory
6 - Download file
20 - Make a list of active processes
22 - End the process by ID
24 - Execute file
26 - Delete file
28 - Retrieve IP Forwarding Table
30 - Write data to file
31 - Inaction
38 - Make a list of accounts
40 - Create a list of services in the system
42 - Make a list of loaded drivers
43 - Collect basic system information (computer name, OS version, memory status, local time, disk information, configured proxy information, current data execution prevention policy for the system and processes, etc.)
44 - Make a list of installed software
46 - Create a list of local users and session information
48 - Make a list of applications used by users
52 - Create directory structure
78 - Create a remote shell
81 - Execute command via remote shell
91 - Enable / Disable User Account Control
93 - End User Session / Shut Down / Restart System
101 - Track and record changes in specified directories
103 - Delete directory
109 - Turn on / off the monitor / on standby
120 - Make a screenshot of the display / active window
126 - Take a screenshot of the display / active windows and update the configuration data
130 - List of information about resources on unpartitioned disks
132 - Rename / move a file, change the time of file creation / opening / writing to the specified
134 - Make a list of recently opened files
152 - Disconnect (previously connected) removable drives
155 - Create / delete registry key, set / delete registry key values, or list registry values / keys / data
159, 161 - Disable routing / firewall, create a proxy server on a specific port
172 - Repeat a dialog box asking you to restart your computer.
175 - Bypass user account control for file manipulation
177 - Create and write file, set data on creation / opening / changing time
181 - Remove all system restore points
183 - Reset (legitimate) component of WinRAR application
185 - Add files to the password-protected archive (password = "12KsNh92Dwd")
187 - Decrypt, unpack and load DLL, load exe files from resources RC2CL, RC2FM
189 - Create a system restore point
191 - Extract password-protected archive (12KsNh92Dwd)
193 - Change the encrypted file
195 - Restart after completion of the main process
197 - Send 198 bytes of hard coded data in the pattern
199 - Rename / Move File
206 - Decrypt, unpack and load a DLL, load exe files from RC2CL, RC2FM resources
211 - Download the collected information (screenshots, audio recordings, etc.)
213 - Make a list of active windows
218 - API for recording audio from device input
220 - API for taking photos from a webcam
224 - Make a list of files that are executed every time the system starts
226 - Make a list of enabled wireless networks (MAC address, SSID, signaling interval)
228 - Reset compressed Zlib package
 Figure 8. Backdoor interpreter function (original and modified using Group Nodes in IDA Pro for readability)
Figure 8. Backdoor interpreter function (original and modified using Group Nodes in IDA Pro for readability)Conclusion
InvisiMole is a full-featured spyware software that allows you to compete with other well-known cyber espionage tools.
One can only guess why the authors use two modules with duplicate functions. One would assume that the smaller module,
RC2FM , is used in the first phase of intelligence, and the larger,
RC2CL , is run only on the machines that interest the operators.
But this is not so - two modules are launched simultaneously. The second possible explanation: the modules are assembled by different authors, and then combined to provide operators with a maximum of tools.InvisiMole uses only a few techniques to avoid detection and analysis. However, since the spike was used in attacks on a small number of high-ranking objects, it managed to avoid detection for at least five years.Compromise Indicators (IoCs)
Detection by ESET products
Win32/InvisiMole.A trojan
Win32/InvisiMole.B trojan
Win32/InvisiMole.C trojan
Win32/InvisiMole.D trojan
Win64/InvisiMole.B trojan
Win64/InvisiMole.C trojan
Win64/InvisiMole.D trojanHashi SHA-1
5EE6E0410052029EAFA10D1669AE3AA04B508BF9
2FCC87AB226F4A1CC713B13A12421468C82CD586
B6BA65A48FFEB800C29822265190B8EAEA3935B1
C8C4B6BCB4B583BA69663EC3AED8E1E01F310F9F
A5A20BC333F22FD89C34A532680173CBCD287FF8Domain Names of C & C Servers
activationstate.sytes[.]net
advstatecheck.sytes[.]net
akamai.sytes[.]net
statbfnl.sytes[.]net
updchecking.sytes[.]netIP addresses of C & C servers and activity period
2013-2014 - 46.165.231.85
2013-2014 - 213.239.220.41
2014-2017 - 46.165.241.129
2014-2016 - 46.165.241.153
2014-2018 - 78.46.35.74
2016-2016 - 95.215.111.109
2016-2018 - 185.118.66.163
2017-2017 - 185.118.67.233
2017-2018 - 185.156.173.92
2018-2018 - 46.165.230.241
2018-2018 - 194.187.249.157Registry keys and values
RC2FM
[HKEY_CURRENT_USER\Software\Microsoft\IE\Cache]
"Index"RC2CL
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Console]
or [HKEY_CURRENT_USER\Software\Microsoft\Direct3D]
"Settings"
"Type"
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OLE]
or [HKEY_CURRENT_USER\Software\Microsoft\Direct3D]
"Common"
"Current"
"ENC"
"FFLT"
"Flag1"
"FlagLF"
"FlagLF2"
"IfData"
"INFO"
"InstallA"
"InstallB"
"LegacyImpersonationNumber"
"LM"
"MachineAccessStateData"
"MachineState 0"
"RPT"
"SP2"
"SP3"
"SettingsMC"
"SettingsSR1"
"SettingsSR2"Files and folders
RC2FM
%APPDATA%\Microsoft\Internet Explorer\Cache\AMB6HER8\
%volumeSerialNumber%.dat
content.dat
cache.dat
index.dat
%APPDATA%\Microsoft\Internet Explorer\Cache\MX0ROSB1\
content.dat
index.dat
%random%.%ext%
%APPDATA%\Microsoft\Internet Explorer\Cache\index0.datRC2CL
Winrar\
comment.txt
descript.ion
Default.SFX
WinRAR.exe
main.ico
fl_%timestamp%\strcn%num%\
fdata.dat
index.dat
~mrc_%random%.tmp
~src_%random%.tmp
~wbc_%random%.tmp
sc\~sc%random%.tmp
~zlp\zdf_%random%.data
~lcf\tfl_%random%