This year, the Positive Hack Days forum was visited by more than 5,000 people, most of whom are information security specialists. A distinctive feature of the forum visitors is a non-standard mindset and super-intuition on many technical issues. All these qualities could be shown in hacker contests prepared by the organizers, one of which was a contest for hacking CAMBreaker IP cameras. Has anyone managed to cope with all the challenges set - in our article.
Each participant could try on the role of a hacker of video surveillance cameras and try to gain unauthorized access to various IoT devices and disassemble the source code of the firmware in search of various vulnerabilities. The reward for all the efforts were interesting and useful prizes from the organizers.
Preparation for the competition began two months before the event, and frankly, it was not easy. It consisted of several stages:
- Selection of cameras for the competition.
- Revision of cameras for firmware version, software offered for working with them, as well as their performance.
- Receiving firmware (firmware) of each camera. It was carried out by several methods:
- Interception of firmware during the update of the camera through the Android application.
- Download from the official website of the manufacturer.
- Connect to the device using telnet.
- Through the connection to the device using the UART interface. For reference: the UART protocol (universal asynchronous receiver transmitter), or UART (Universal Asynchronous Transceiver) is the oldest and most common physical data transfer protocol today. The most famous protocol of the UART family is RS-232 (popularly the COM port).
- Connection of programmers to Flash-chips installed inside the camera, using clip-pegs without evaporation of electronic components of the device.
- And, perhaps, the most time-consuming process of extracting dumps is soldering and subtracting chips using a programmer.
- Configure static IP addresses and authentication data on the devices themselves.
- Designing, building a local network for the stand of the competition.
- Setup and configuration of the stand in the demo-environment.
Here are some photos taken during the preparation process:

The process of extracting data from the chip using the programmer CH341A

Fee one of the cameras

Programmer and his friends :)
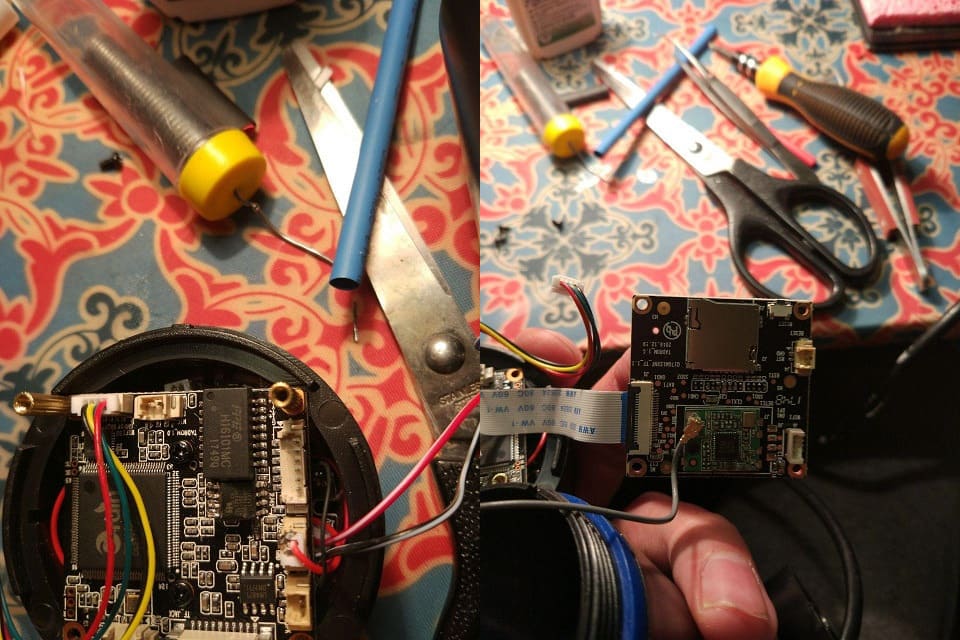
Some chips still had to be soldered due to the nature of the switching circuit.
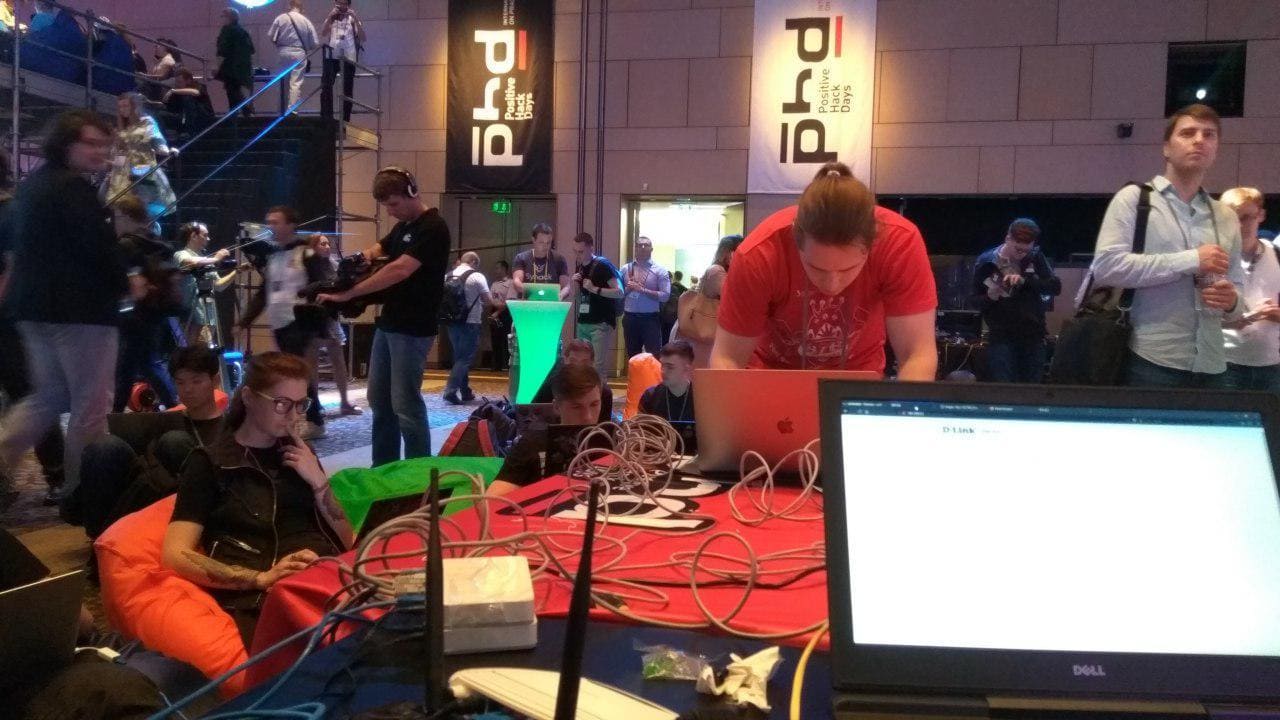
The stand consisted of a rigid frame, on which 11 cameras and several switches were installed. A wireless network was deployed for the participants, and one free switch with patch cords was provided for connecting to the network.

Stand

Big Brother is watching for ... smaller brothers
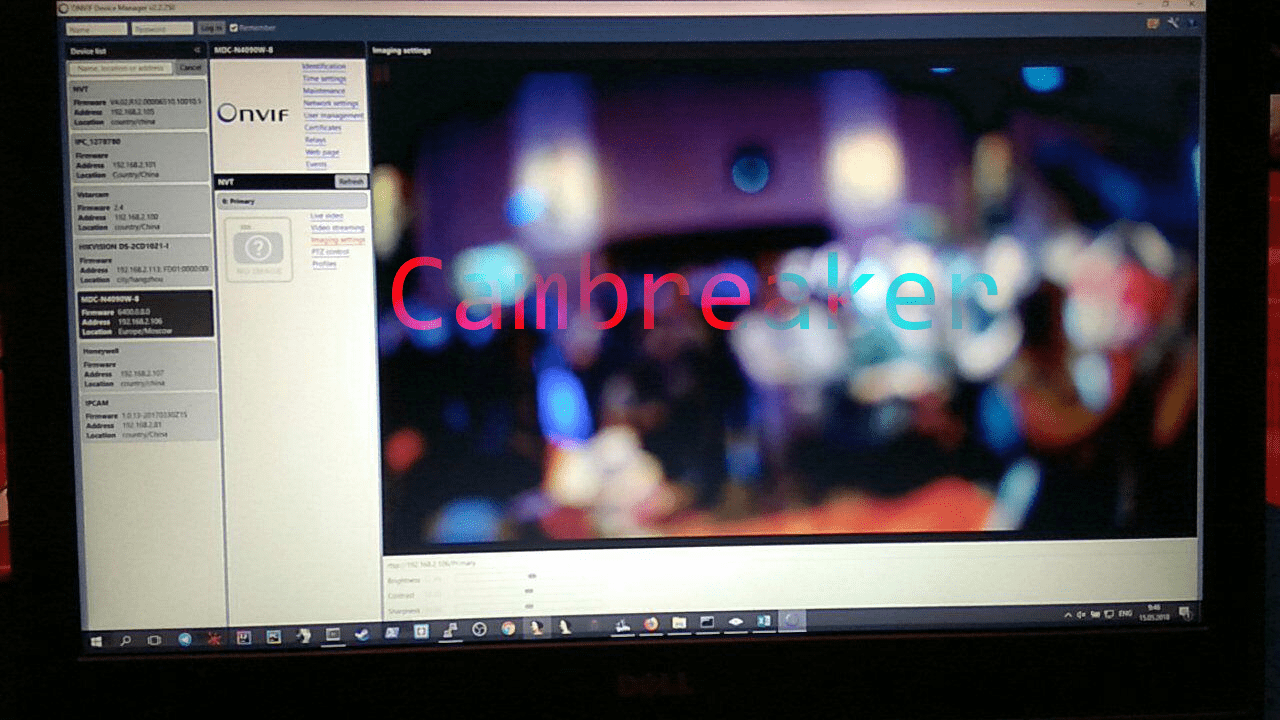
The FTP server worked on a router that held the entire network, from which participants could get camera firmware. Addresses, credentials, serial numbers and other data of the cameras were in the public domain — it was possible to enter any of them.
Hackers @ work
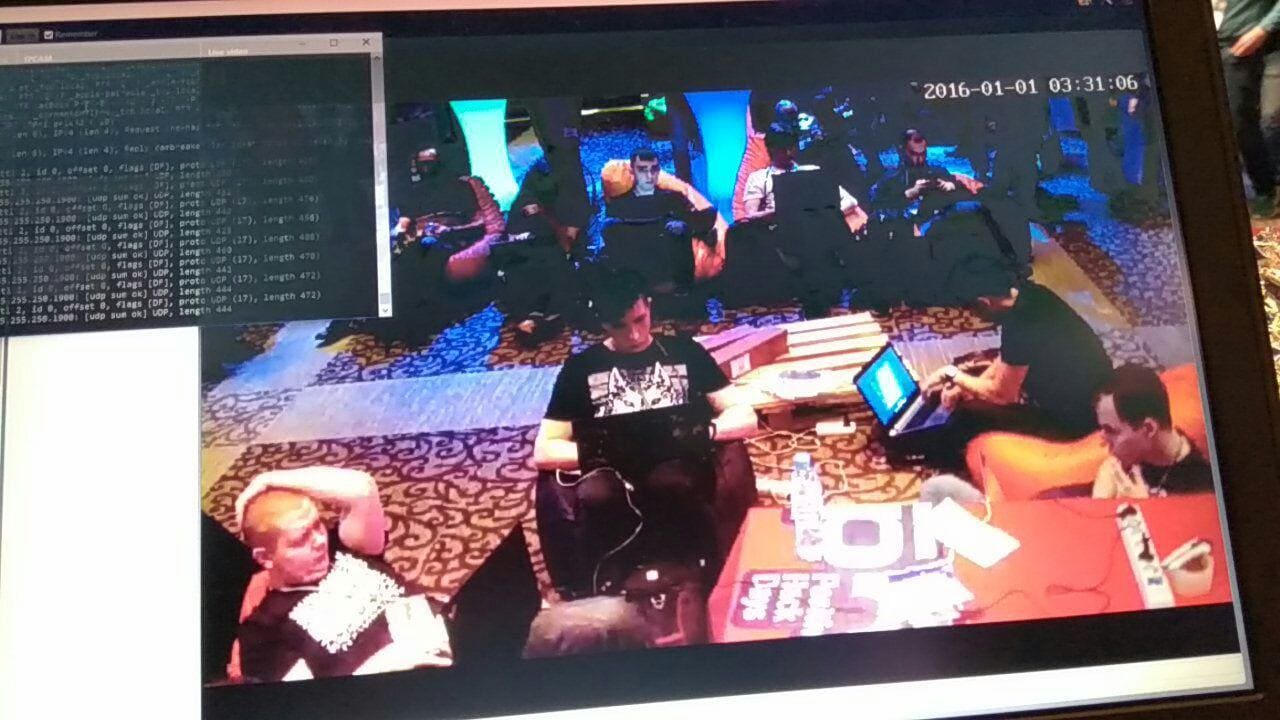
Once in the network and receiving the firmware, the participants immediately begin the study.
On the first day of the competition, we offered the competitors to solve a difficult task: to find a vulnerability in the chamber, to write an advisory for its operation or a working PoC-exploit. Unfortunately, an impressive part of the participants dropped out as soon as she learned about such high demands. But JTAGulator just won’t win!
More resistant hours studied firmware, sitting on comfortable ottomans. The firmware files were previously uploaded to an FTP server accessible from the competition's local network. A variety of tools were used to research firmware for vulnerabilities: IDA Pro, Binwalk, Radare2, Strings, Wireshark, Tcpdump, Sqlmap, Burp Suite. “It’s not worthwhile to bend the network under a changeable world, let it be better bend under us,” the participants of the competition probably decided so, generating hundreds of gigabytes of traffic in the process of research.
At 13:37 - the most suitable " hacker " time - brought a couple of kegs of cold beer.

Cool during the competition could be a beer
After such refueling, the hacking process did not slow down at all. Several forum participants, initially lured by beer, ultimately chose to remain in the company of outdoor and indoor video surveillance devices. However, at the end of the first day we did not receive a single report.


Competitors
But on the second day, two reports about the found vulnerabilities came at once. The first of them in the vstarcam-c16s camera was found by an information security specialist from Novosibirsk Pavel Cherepanov. The second vulnerability was revealed by another specialist, Ivan Aniseny. In the MDC-N4090W-8 camera authentication form, he found a blind SQLi, which allows you to embed SQL commands into the id parameter and, using blind operation, extract all logins and passwords (including the root user) from the database.
The camera manufacturers are notified of all the vulnerabilities found, and all the exploits developed by the participants remain 0-day.
Pavel and Ivan received their well-deserved prizes.

Award: Pavel Cherepanov

Rewarding: Georgy Zaitsev was awarded the prize for Ivan Anissen