Threats to privacy and security on the Internet are becoming more serious. We at Mozilla are tracking them carefully. We consider it our duty to do everything possible to protect Firefox users and their data.
We are concerned about companies and organizations that secretly collect and sell user data. Therefore, we added
tracking protection and created a
Facebook container extension . In the coming months there will be even more protective measures.
Now we are adding two more technologies to the list:
- HTTPS DNS is the new IETF standard in the development of which we participated
- Trusted Recursive Resolver - a new secure way to rezolvit DNS, provided in conjunction with Cloudflare
These two initiatives eliminate data leaks that have been part of the domain name system since its inception 35 years ago. And we need your help in testing. Let's see how DNS over HTTPS and Trusted Recursive Resolver protect our users.
But first, let's see how web pages are transmitted over the Internet.
If you already know how the DNS and HTTPS protocols work, you can go to the section on how
DNS over HTTPS helps .
HTTP Short Course
When people explain how the browser loads a web page, they usually explain it this way:
- Your browser makes a GET request to the server.
- The server sends a response, which is a file containing HTML.

This system is called HTTP.
But this scheme is too simplified. Your browser does not talk directly to the server. Probably because they are not close to each other.
Server can be thousands of kilometers away. And there is probably no direct connection between your computer and the server.

Thus, before the request gets from the browser to the server, it will pass through several hands. The same is true for the answer.
I think of this as schoolchildren passing notes to each other in the classroom. Outside the note says to whom it is intended. The child who wrote the note will give it to her neighbor. Then that next child sends it to one of the neighbors — probably not to the final recipient, but to the one who is in the right direction.
 - Psst ... pass it on to Sandy
- Psst ... pass it on to SandyThe problem is that anyone along the way can open a note and read it. And there is no way to know in advance what path the note will take, so it is not known what kind of people will get access to it.
It may be in the hands of people who will do harmful things ...
For example, share the contents of the note with all.
 - Oh, this is piquant .... Hey people! Danny fell in love with Sandy!
- Oh, this is piquant .... Hey people! Danny fell in love with Sandy!Or change the answer.
 - Do you like me too?
- Do you like me too?
“Hehe, prank him and write“ No ”...To resolve these problems, a new secure version of HTTP has been created. It's called HTTPS: it's like a lock on every message.

Only the browser and server know the combination to unlock. Even if messages pass through several routers, only you and the website can actually read the content.
This solves many security issues. But there are still unencrypted messages between your browser and the server. So people on the way can still interfere in your business.
For example, data is still open during connection setup. When sending the original message to the server, you also send the server name in the “Server Name Indication” field. This allows server operators to run multiple sites on the same computer and at the same time understand who you want to contact. This initial request is part of the encryption setup, but the initial request itself is not encrypted.
Another place where data is open is DNS. But what is DNS?
DNS: Domain Name System
In the metaphor of passing notes in class, I said that the recipient's name must be written outside the note. This is also true for HTTP requests ... they have to announce where they are going.
But you can not use the usual site name. None of the routers understand who you are talking about. Instead, you must use an IP address. Here's how routers along the way understand which server you want to send a request to.
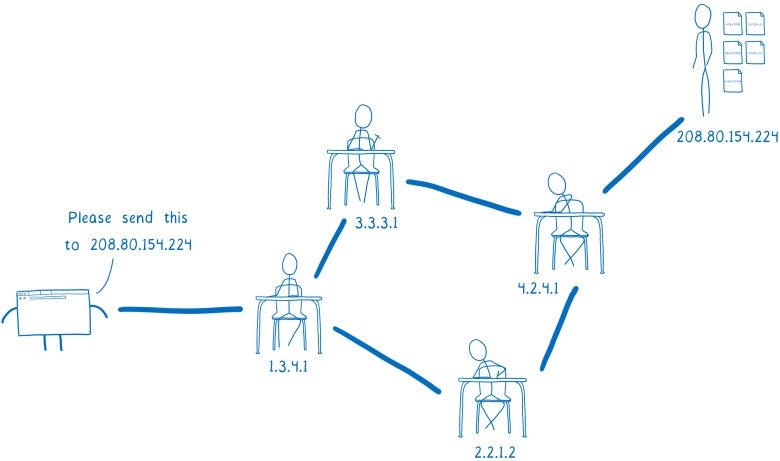 - Please send it to 208.80.154.224
- Please send it to 208.80.154.224This causes problems. It is inconvenient for users to remember the digits of the IP address. I want to give the site a memorable name ... which will be stored in people's memory.
That's why we have a domain name system (DNS). Your browser uses DNS to resolve the site name to an IP address. This process — converting a domain name to an IP address — is called resolving a domain name or resolving it.

How does the browser solve the problem?
One option is to have a large list like a telephone directory in the browser. But as new websites appear or move to new servers, it will be difficult to keep this list up to date.
Thus, instead of a single list for all domain names, there are many small lists related to each other. This allows them to be controlled independently.
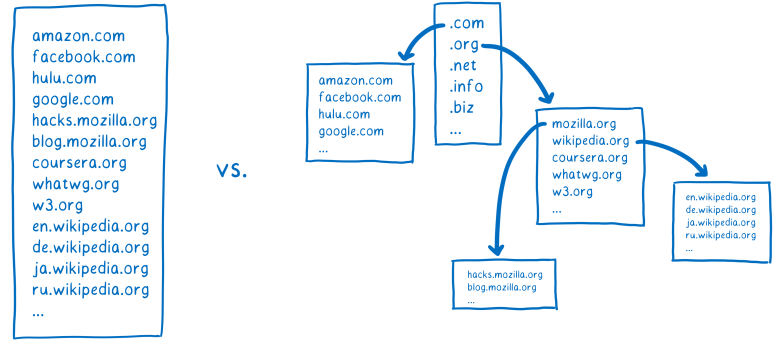
To obtain the IP address corresponding to the domain name, you need to find a specific list that contains the desired domain name. It looks like treasure hunting.
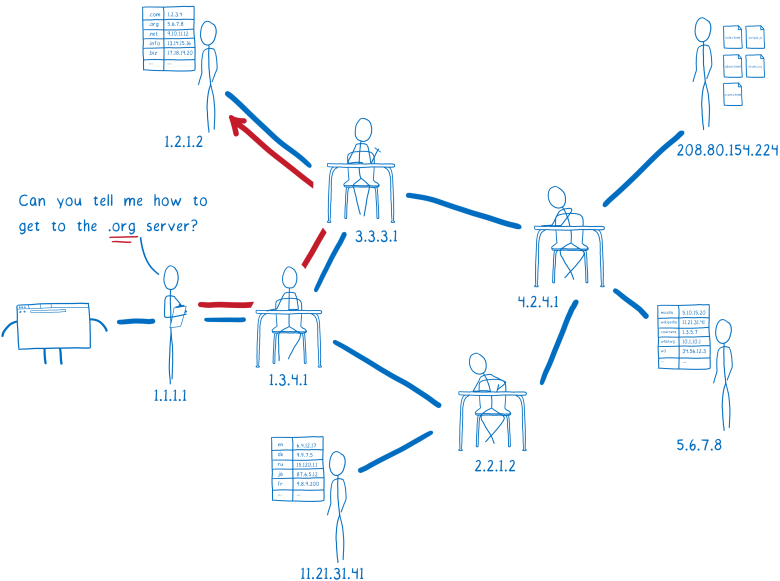
What does such a search for treasure look like for a site like the English-language Wikipedia,
en.wikipedia.org ?
Domain can be divided into parts.
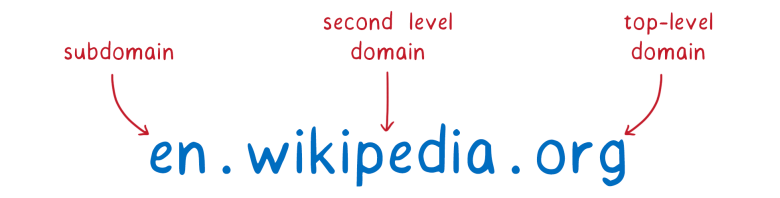
With such parts, you can start the hunt for a list containing the IP address of the site. But we need help finding. The tool that performs this hunt instead of us and finds the IP address is called a resolver.
First, the resolver accesses the so-called root DNS server. He knows several different root DNS servers, so he sends a request to one of them. Resolver asks the root DNS where to find additional information about addresses in the top-level domain zone
.org .
 - You do not know how to go to en.wikipedia.org?
- You do not know how to go to en.wikipedia.org?
- I don't know about anything in the .org zone, but 5.6.7.8 can helpThe next server is called a top-level domain name server (TLD). The TLD server is aware of all second-level domains that end in
.org .
However, he does not know anything about the subdomains of
wikipedia.org , so he also does not know the IP address
en.wikipedia.org .
The TLD name server will advise the resolver to ask this question to the Wikipedia name server.
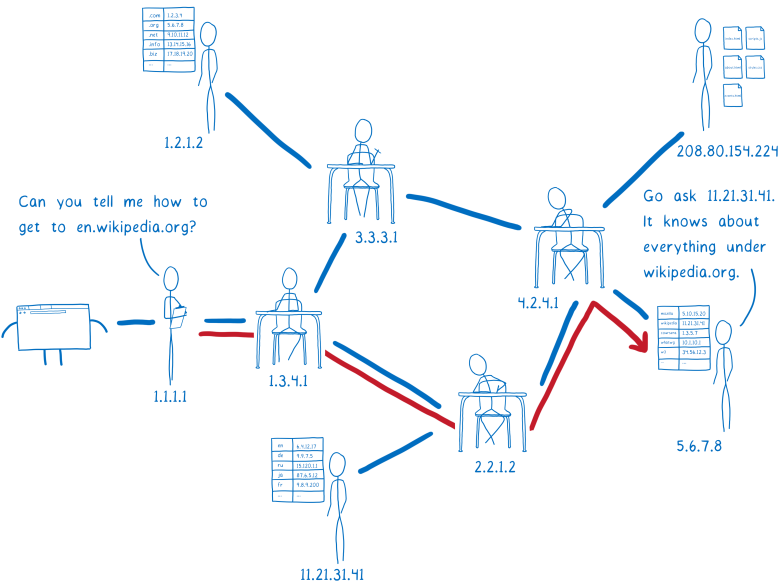 - You do not know how to go to en.wikipedia.org?
- You do not know how to go to en.wikipedia.org?
- Go and ask for 11.21.31.41, he knows about the sites in the domain wikipedia.orgResolver is almost finished. The Wikipedia name server is what is called an authoritative server. He knows about all subdomains
wikipedia.org . Thus, he also knows about
en.wikipedia.org and other subdomains, such as the German version of
de.wikipedia.org . The authoritative server tells the resolver what IP address you can get the HTML files for this site.
 - You do not know how to go to en.wikipedia.org?
- You do not know how to go to en.wikipedia.org?
- Oh yes, just go to 208.80.154.224Resolver will return the
en.wikipedia.org IP address to the operating system.
This process is called recursive resolution, because you have to go back and forth, asking essentially different servers the same question.
I said that we needed a resolver to help in the search. But how does the browser find this resolver? In general, he asks the operating system.
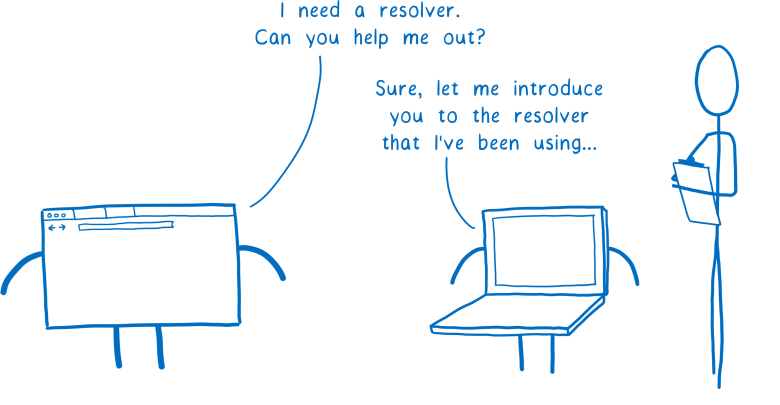 - I need a resolver. Can you help me?
- I need a resolver. Can you help me?
- Of course, let me introduce you to the resolver that I useHow does the operating system know which resolver to use? There are two possible ways.
You
can configure the computer to use a specific resolver that you trust. But very few people do it.
Instead, most simply use the default settings. And by default the OS will use any resolver which network will say. When the computer connects to the network and obtains its IP address, the network recommends a specific resolver.
 - Can I get an IP address?
- Can I get an IP address?
- No problem! And if you need a resolver, I recommend this one.This means that the resolver used may change several times a day. If you go to a cafe to work during the day, you probably use a different resolver than in the morning. And this happens even if you set up your own resolver, because there is no security in the DNS protocol.
How can I exploit DNS?
So how does this system endanger users?
Usually the resolver tells each DNS server which domain you are looking for. This request sometimes includes your full IP address. And if not the full address, then increasingly, the request includes most of your IP address, which can be easily combined with other information to establish your identity.
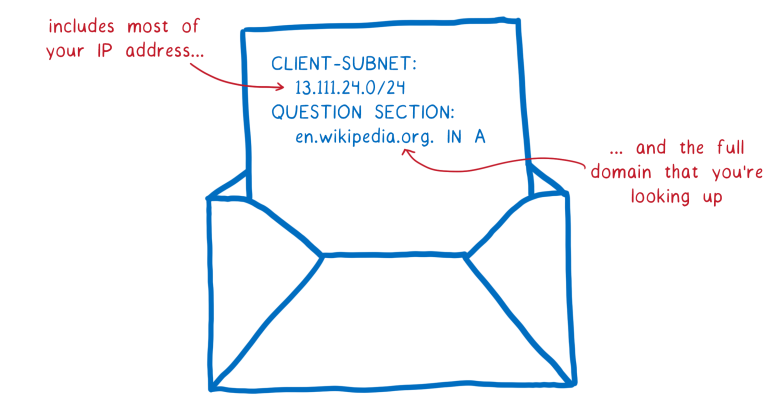 Contains most of your IP address ...
Contains most of your IP address ...
... and the full domain you are looking forThis means that every server you ask for help with resolving domain names sees which site you are looking for. Moreover, anyone on the way to these servers also sees your requests.
There are several ways in which such a system compromises user data. The two main ones are tracking (tracking) and spoofing (spoofing).
Tracking
As I said above, in full or partial information about an IP address, it is easy to determine the identity of someone who requests access to a specific site. This means that the DNS server and any user on the way to this DNS server (router on the way) can create a user profile. They can make a list of all the sites you have viewed.
And this is valuable data. Many people and companies are willing to pay a lot to see your browsing history.
 How much are you willing to pay for information about what John Doe was looking at?
How much are you willing to pay for information about what John Doe was looking at?Even if we didn’t have to worry about potentially vile DNS servers or routers along the way, there is still the risk that your data will be collected and sold. Because the resolver itself — which the network gave you — may not be reliable.
Even if you trust the recommended resolver from the network, you probably use it only at home. As I already mentioned, each time in a cafe, hotel or in any other network, you will probably be given a different resolver. And who knows what its data collection policy is?
In addition to the fact that your data is collected and then sold without your knowledge or consent, the system is used in an even more dangerous way.
Spoofing
Using spoofing, someone on the path between you and the DNS server changes the answer. Instead of a real IP address, the scammer tells you the wrong IP address for the site. Thus, you can block access to the real site or send a non-fake version from scammers.
 Send it to 1.6.6.6 ... this is an absolutely correct address, and not a fake website at all, which I control
Send it to 1.6.6.6 ... this is an absolutely correct address, and not a fake website at all, which I controlAgain, here and the resolver itself can act vilely.
Suppose you are shopping in a Megastore. You want to compare prices and see if such a product is not sold cheaper at the competing online store big-box.com.
But if you use Megastore WiFi in their sales area, you probably use their resolver. He can intercept the request to big-box.com and tell you that the site is unavailable.
How to fix the situation with Trusted Recursive Resolver (TRR) and DNS over HTTPS (DoH)?
We at Mozilla firmly believe that we are responsible for protecting users and their data, and therefore we are working to eliminate these vulnerabilities.
We present two new functions to correct the situation: this is a trusted recursive resolver (TRR) and DNS over HTTPS (DoH). Because in fact there are three threats:
- You may end up using an unreliable resolver that keeps track of your requests or substitutes for responses from DNS servers.
- Routers along the way can track requests or intervene in the same way.
- DNS servers can track DNS requests.
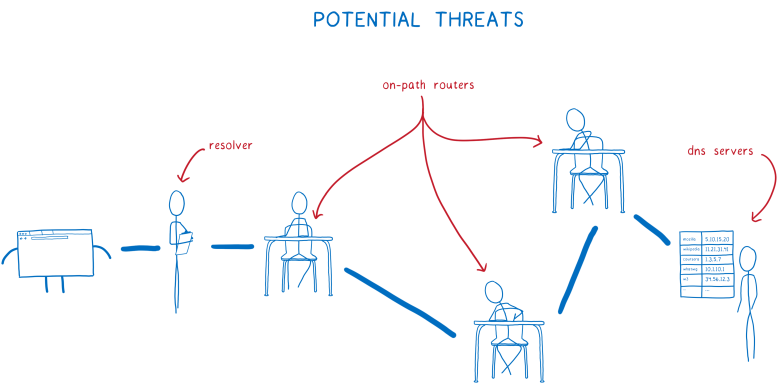
How to avoid it?
- Avoid unreliable resolvers with TRR.
- Protect against listening and spoofing using DNS over HTTPS.
- Transfer as little data as possible to protect users from de-anonymization.
Avoid unreliable resolvers with TRR
Networks may stop recommending unreliable resolvers that collect user data or fake DNS queries, because very few users are aware of the risks or how to protect themselves.
Even for users who are aware of the risks, it is difficult for an individual user to negotiate with his provider or another organization about the guarantees that his DNS queries will be treated responsibly.
However, we studied these risks ... and we have a certain impact. We have been looking for a company that will help us protect the DNS data of users. And they found one such:
Cloudflare .
Cloudflare provides a recursive resolving service with a privacy policy for users. They pledged to delete all personally identifiable data after 24 hours and never transfer this data to third parties. There will be regular checks that the data is indeed deleted, as promised.
Because of this, we have a trusted resolver to protect user privacy. This means that Firefox can ignore the network resolver and go directly to Cloudflare. Now you can not worry that the attackers are using a resolver for selling user data or DNS spoofing.
Why did we choose one resolver? Like us, Cloudflare is concerned with creating a private DNS service. Together with us they developed a good transparent DoH resolver. The company readily went to the additional protection of the service, so we are happy to cooperate with them.
But this does not mean that you should use Cloudflare. Users can configure Firefox to use any recursive resolver with DoH support. As new services become available, we plan to implement simple detection and switching between them.
Protect against listening and spoofing using DNS over HTTPS
But the resolver is not the only threat. Routers on the way can track and spoof DNS queries, because they also see the contents of DNS queries and responses. Fortunately, the Internet already has the technology to protect against listening from the routers on the way. This is the encryption I was talking about.
Using HTTPS to exchange DNS packets protects our users' DNS requests from espionage.
Transmit as little data as possible to protect users from deanonymization
In addition to the trusted resolver that works on the DoH protocol, we are working with Cloudflare on additional security measures.
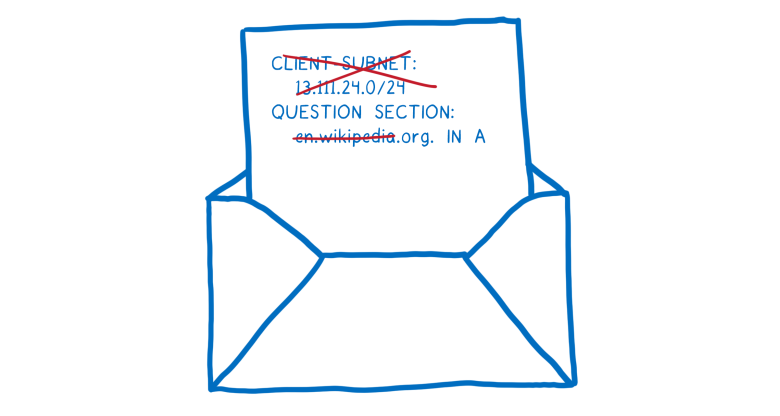
Usually the resolver sends the full domain name to each server: the root DNS, the name server of the top-level, second-level domains, etc. But the Cloudflare server will act differently. It will only send the part that is related to the specific DNS server. This is called
minimizing QNAME .
 - You do not know how to go to the .org server?
- You do not know how to go to the .org server?Often a resolver also includes the first 24 bits of your IP address in the request. This helps the DNS server find out where you are and select the nearest CDN. But DNS servers can use this information to bind disparate queries to each other.
Instead, Cloudflare will make a request from one of its own IP addresses, which is located next to the user. This provides geolocation without reference to a specific person. We are also learning how to implement even better, finer load balancing with respect to confidentiality.
All of this - removing unnecessary parts of the domain and IP addresses - means that the DNS server can collect much less data about you.
What is beyond the scope of TRR with DoH?
These protective measures reduce the number of people who can see the history of the pages you have visited. But they do not completely eliminate data leakage.
After performing a DNS lookup to obtain an IP address, you still need to connect to the web server at that address. For this you need to send a request. The request includes SNI (server name indication) indicating a specific site on the server. And this request is not encrypted.
That is, your ISP is still able to find out which sites you visit, because they are listed right there in SNI. The information is also open to routers that send the initial request from your browser to the web server.
But as soon as you connect to the web server, everything is encrypted. And the most important thing is that this encrypted connection can be used for any site on this server, and not just for the one you originally requested.
This is sometimes referred to as merging an HTTP / 2 connection (connection coalescing) or simply reusing a connection. When you open a connection to a compatible server, it will tell you which other sites are hosted on it. You can then visit these sites using an existing encrypted connection.
Why is this useful? Because you do not need to open a new connection to connect to these other sites. That is, you do not need to send another unencrypted initial request indicating SNI and disclosing which site you are going to. So you can visit any of the other sites on the same server without revealing them to your provider and routers on the way.
With the increasing popularity of CDN, more and more individual sites are served by one server. And since you can have several merged connections open, you simultaneously connect to several shared servers or CDNs, visiting all sites on different servers without data leakage. So this function works more effectively as a protective shield.
What is the status?
You can already enable DNS over HTTPS in Firefox now, and we
recommend doing this .
We want to enable DoH by default for all users, because everyone deserves privacy and security, regardless of whether he knows about DNS leaks or not.
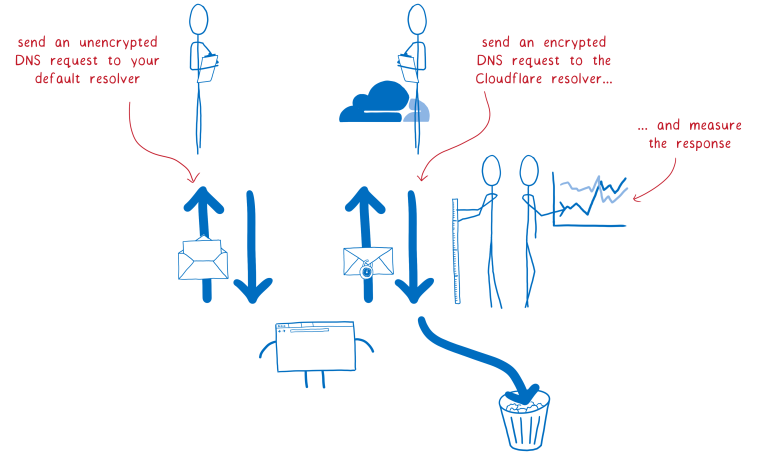
But this is a significant change, and you must first test it. Therefore, we are conducting research. Half of our
Firefox Nightly users are asking for help gathering performance data.
In testing, the default resolver is used, as now, but requests are also sent to the Cloudflare DoH resolver. Then we compare the result to verify that everything works as expected.
For research participants, the Cloudflare DNS response is not yet used. We just check that everything works, and then we throw out the answer Cloudflare.
Thanks to the support of the Nightly users who help test Firefox every day. We hope that you will help us too.