
A few weeks before the
Positive Hack Days forum, the traditional Competitive Intelligence competition was held. This year, we relied on the
security audit and cyber threats of ICO , during which we had to analyze all external infrastructure, including a team of organizers, developers and consultants, to reduce risks. We created our competition based on real projects.
All assignments were centered around the fictional small crowdsale of Notsopositive, a typical ICO with a small number of employees. During the competition, participants learned a lot of hidden information about the founders and employees of the company, their relatives and friends. First of all, the participants were required to have a large number of online services and social networks in the arsenal, to know their specifics and to be able to use. In addition, it was necessary to operate the available information in order to find the necessary data about people and with their help obtain new ones.
Tasks were distributed in such a way that both veterans and newcomers would be boring and each would leave at least with one flag. Many tasks formed a peculiar sequence and formed into a whole plot. There were also tasks that were performed nonlinearly, so participants had to store information about each step taken.
To solve the first introductory task, where the rest started from, it was necessary to use Google:
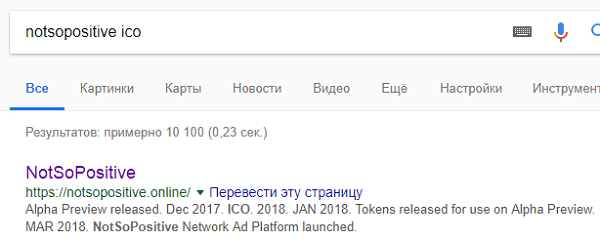

All tasks were built around eight Notsopositive employees from the Executive Team and the Development Team.
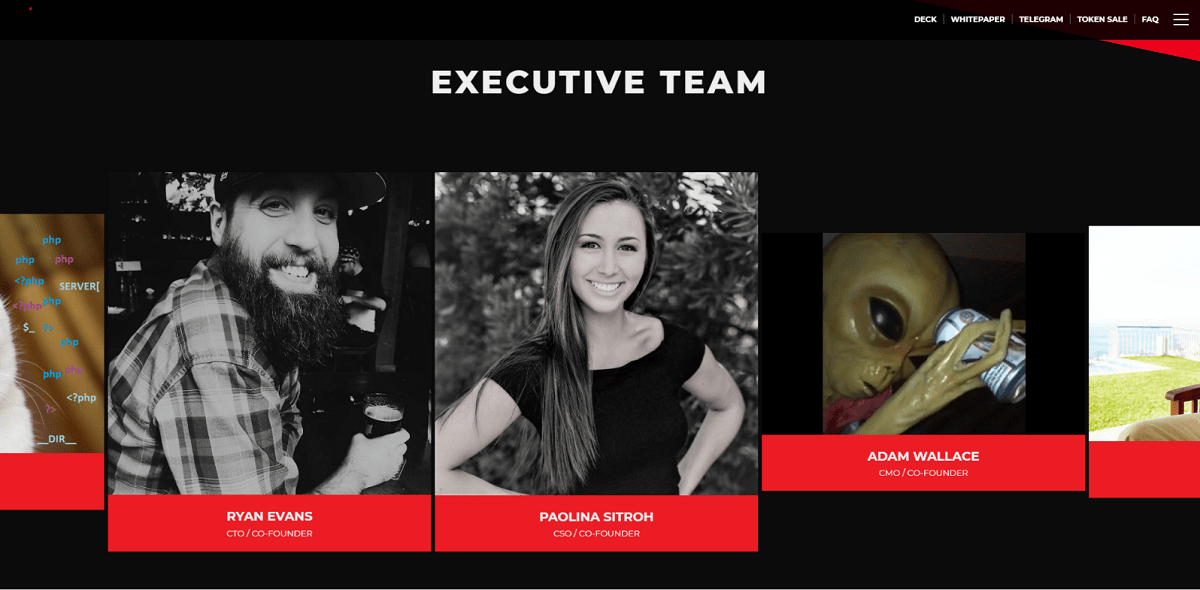

With a careful study of the site, the participants now and then ran across various “entry points” that led to the solution. More details on each task.
Adam Wallace, CMO
Questions in the Adam Wallace thread:
- Adam Wallace username?
- What does Adam's son have allergies to?
- What is Adam's house number?
- Where does Adam's son study?
- CMO's favorite bar name?
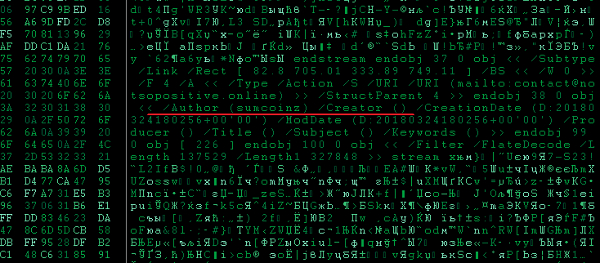
So, stumbling on the whitepaper site, you had to upload a PDF to any online service for reading META-data (for example,
PDFCandy ) or open it in Word, where you could find the nickname CMO, also known as Adam Wallace, sumcoinz.
Fans of doing everything with their hands could open the PDF in their favorite HEX-editor and get Adam's nickname on their own.
Further, in order to continue the chain, it was necessary to find an FTP server using
Knock Subdomain Scanner , also for this purpose one could use the
dnsmap ,
sublist3r ,
sublazerwlst utilities .

There was another way: find out the real IP address of the site notsopositive.online, hidden behind CloudFlare, and scan the entire subnet in search of the 21st port. The approach to solving this task is individual and depends on the experience and skills of each participant.
The obtained IP-address of the FTP-server and login was enough to attack brute force password. For this it was necessary to apply the legendary utility
THC-Hydra . It sounds easy, but participants needed to use the entire dictionary of the found nicknames of the ICO organizers. By the way, in the FTP logs we also saw attempts to attack root, admin, administrator users.
Having learned the login of Adam (sumcoinz), it was necessary to sort out the password according to the most famous
dictionary among CTF-players.
During the competition, some participants had problems connecting to FTP due to the limited number of clients, but the configuration error was later corrected. We changed the FTP server password to a simpler one in order to simplify and speed up the participants to complete the task.

The attack usually takes only a few seconds. Next, it was necessary to go to FTP in any convenient way and find a file dump that is typical for a private server.
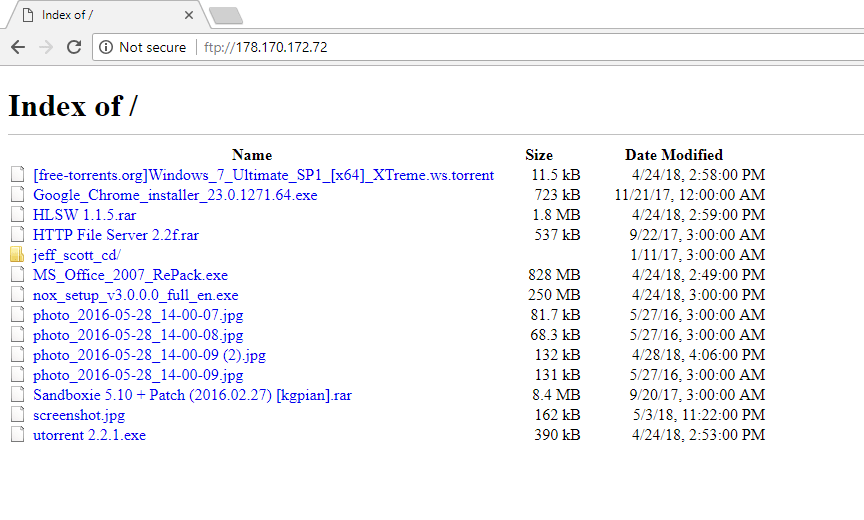
In addition to the software, there were curious photos that contained several flags at once.

Adam’s blunt handwriting indicates his son’s name, place of study, school address and home address! Another flag is the allergen of son Adam. On the same server, it was possible to find an interesting file called screenshot.jpg:
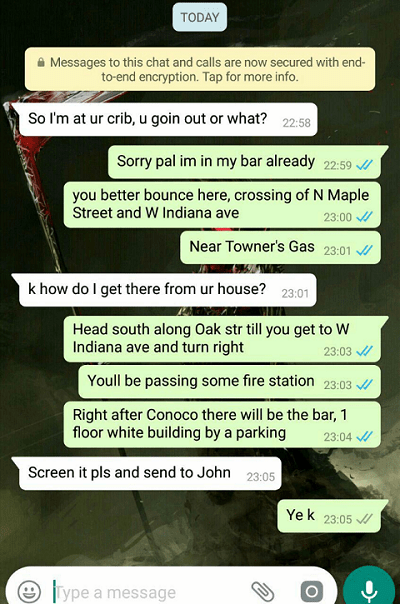
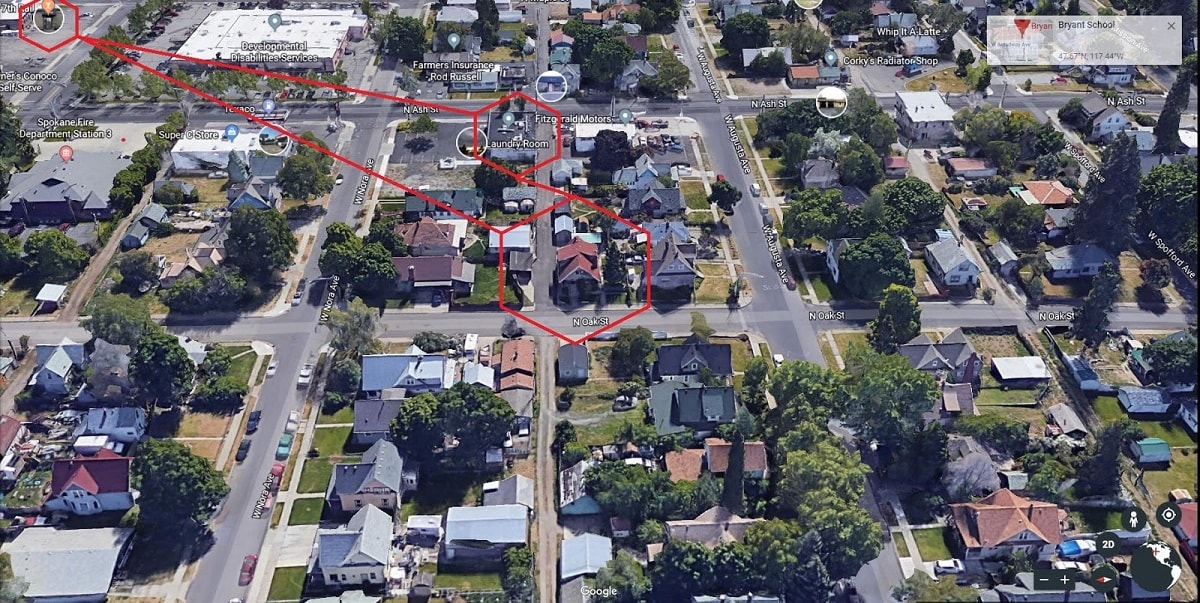
In the screenshot of the WhatsApp correspondence, presumably Adam and his friend. In the message, Adam's friend finds out about the location of the bar in which, at the time of their communication, Adam spends time. Using any service with Spokane city maps, the participant could “go through” the described route and stumble upon that very favorite CMO Notsopositive bar called “7th Rail”.
At the time of the completion of the competition, only 20 participants successfully completed all the tasks from the storyline of Adam Wallace and reached the described stage.
Ryan Evans, CTO
Questions to the branch Ryan Evans:
- Github username?
- Corporate email address?
- Ryan's wife email address?
- Ryan's wife username?
- Ryan's wife resort?
- Ryan's wife friend's surname?
- Ryan's wife place of work (company name)?
Ryan Evans - Technical Director of the ICO-project. Using utilities to search directories and files, such as
dirb or the
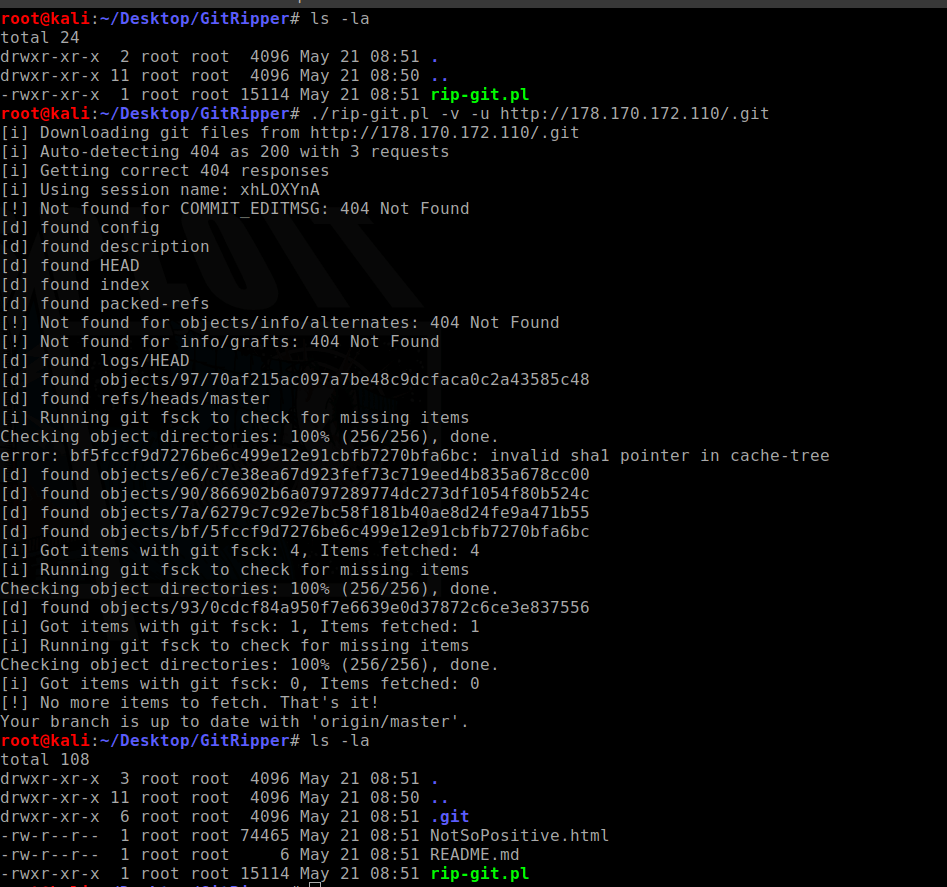
fuzz.txt dictionary, at the root of the notsopositive.online website, you could find the .git directory, from where you can get all the sources from the repository. Next - it was necessary to get the source using
this method, use
GitRipper , specifying the real IP address of the site as a target, and extract the configuration files of the Git version control system. You could get /.git/config using a regular browser.
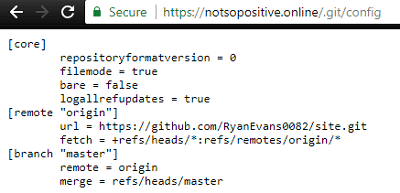
In the config file there was a link to Ryan's GitHub account (
github.com/ryanevans0082 ), where you could stumble upon his Jabber account:


There was no point in writing there, but searching with Google was a good idea. The first flag was handed over, then you had to find the Speaker Deck account and the only downloaded presentation Initial Coin Offering in Google’s issue.
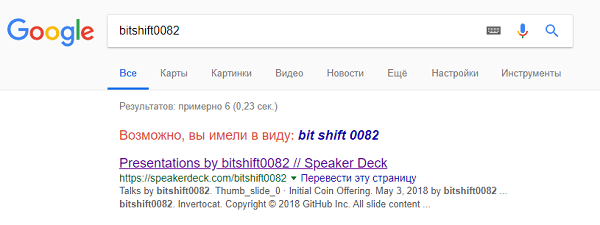
Participants awaited the award, crying out tears of tears from viewing the presentation - on the last slide, Ryan's corporate e-mail was published.

In this case it was useless to go through the password from the email, but it could be restored on a secret question:
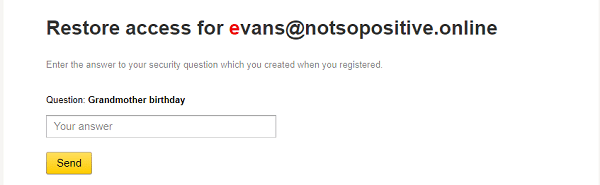
Grandmother's, yes :) The question is not the most reliable. On real projects, we often met with similar ones. The answer to these questions, as a rule, can be found on social networks - Odnoklassniki, VKontakte and Twitter. The next step is to search for accounts:
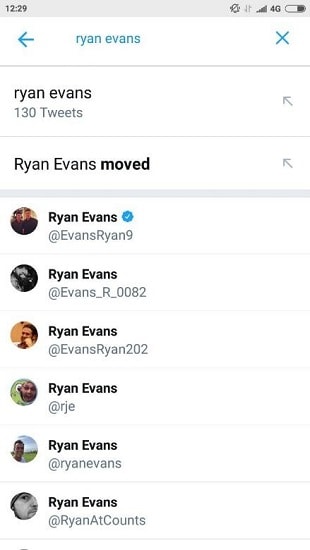
On Twitter, at the request of “Ryan Evans”, a familiar beard appeared. By the way, it was possible to find an account using Yandex.
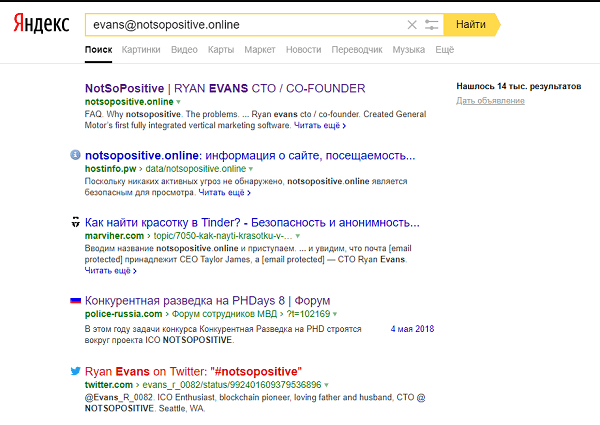
In the Twitter feed, there was a mention of the grandmother's birthday - April 20th.

The exact age of the grandmother could be calculated by the number written by the cream on the cake.
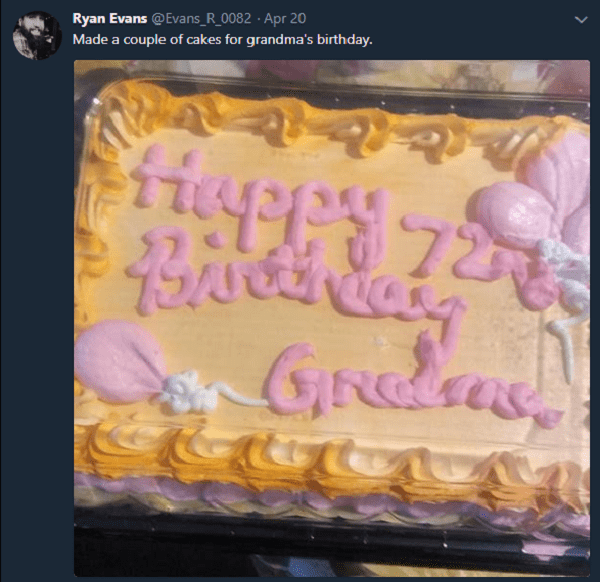
A little arithmetic and now we know the exact date of birth - April 20, 1946. Then a reasonable question arises - in what format could Ryan write the date? It was possible to find out by scrolling through Twitter: there was a post about a car, gray Kia Carens, purchased on October 1, 2014. The date is in the dd.mm.yyyy format. Perhaps Ryan wrote the answer to the secret question in the same format.

Not all OSINT lovers turned out to be motorists at the same time, so some participants had problems with determining the make and model of Adam's car. In cases where the search for pictures on Google or the driving experience does not help, Yandex can help. He accurately identified the make and model of Kia Carens.

Flag CTO's Car model is handed over. Next, it was necessary to substitute the grandmother's birth date in the correct format (04/20/1946) as an answer to the Yandex.Post secret question.
After you could put any new password (the next participant in any case changed it) and now we hit the mailbox of Ryan. In the sent messages there was a letter to his wife, in which the participant could find her email
evansmegan02282@yahoo.com .

From the address it was easy to calculate the name - Megan, and a search on social networks produced a VKontakte page:
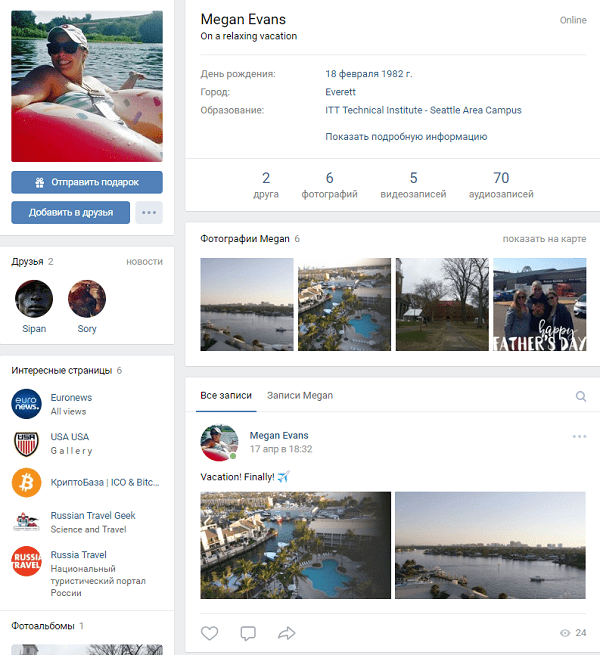
Find Megan VKontakte and it was possible through the password recovery form. To do this, you need to request a password recovery, specify the email and last name Evans:

On the page a huge amount of information:
- hometown,
- university,
- place of work (in subscriptions),
- resting place (GPS tags in EXIF photos),
- several photos to determine the appearance
- approximate interests.
- Several flags about Megan were delivered at once.
Keeping in mind everything new about Megan, the participant probably thought: “Why did Megan never reply to the photo with the cat in the correspondence via email?”. Indeed, something is unclean here.
Few guessed the way to continue the decision, but who guessed it came out in the top 10 participants.
So, install Tinder and emulate geolocation using applications like
Fake GPS - or install Tinder on Bluestacks, where a similar function is present out of the box.

The Megan (Miami, Florida) resting place was found based on the geotags on her photos from the VKontakte page. Using Fake GPS, it was necessary to “fly” to Miami, Florida, set the target audience for the Megan parameters (the age and exact location from the VKontakte profile are already known) and swipe the girls. After 5–10 beautiful ladies, “the one and only” Megan Evans showed up. Only her first and last name in Tinder turned out to be different, and to make sure exactly that it was her, the photos from VKontakte helped.
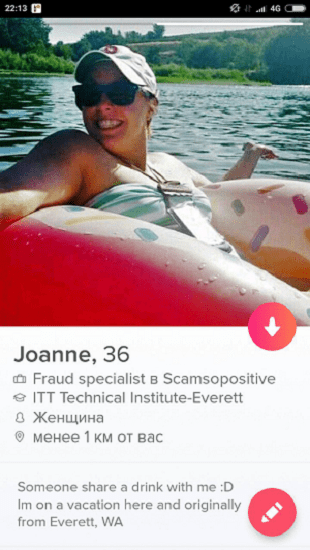
To make sure that this is not a mistake, but the Megan we need, it was necessary to verify the place of study and hometown automatically imported from Facebook when connecting to the account. Flag CTO's wife place of work passed.
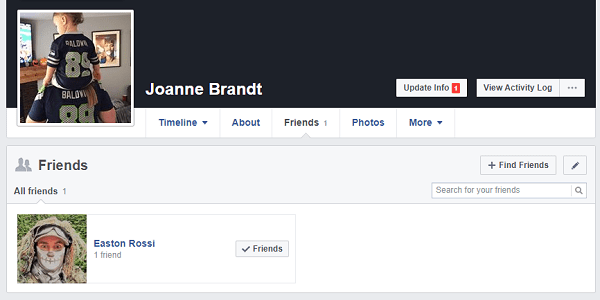
Then the search continued by the second, “shadow” personality of Megan. Feature Tinder - place of work is automatically substituted from the profile of Facebook. Therefore, it was immediately possible to go to Facebook to find the Scamsopositive page.

Using the “jealous student” intelligence method, also known as “breaking through likes”, you could find the Joanne Brandt page and pass the last name of the only friend on this page, Rossi, as the last flag.
The remaining tasks were of a lower level of complexity and were combined into small quests with relatively cheap flags. The solution might require special knowledge of the operation of some services. For example, the task of determining the mobile phone model of the front-end developer Alexey Nitshchikov assumed that the participant was aware of the possibility to indicate the model of a favorite gadget in the profile on the forum w3bsit3-dns.com.
So, first we had to find Alexei's front-end provider in social networks.
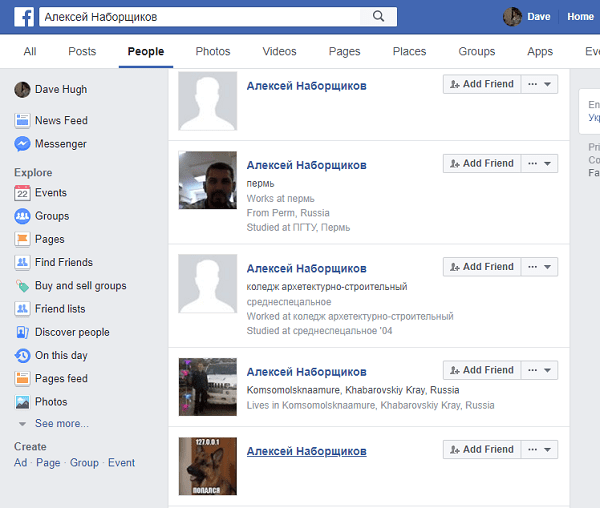
A request to Facebook issued several at once, but only one IT specialist. The subtle link between the description on the company's website and Facebook account was a themed avatar, which issued the professional orientation of our victim.

The unique address of the page (m0arc0de) gave us a frequently used nickname. Next was a search for w3bsit3-dns.com or xda-developers. By nick it was possible to find the very same frontend developer from Notsopositive. In the "About Me" field, Alexey wrote all the information we need about ourselves, which allows us to unambiguously determine that this is exactly who we need. Flag with a phone model handed over.

In the task of searching for an unknown hacker (Evil guy's username on Anonymous freelance service) it was assumed that the participant would be aware of the new portal for anonymous posting of various services and commercial offers called Yukon. After a little flipping through the “Work” section, you could find a curious ad with a direct reference to the site under study. In contacts for feedback was indicated and the mailing address in which was the nickname of the "evil" guy.
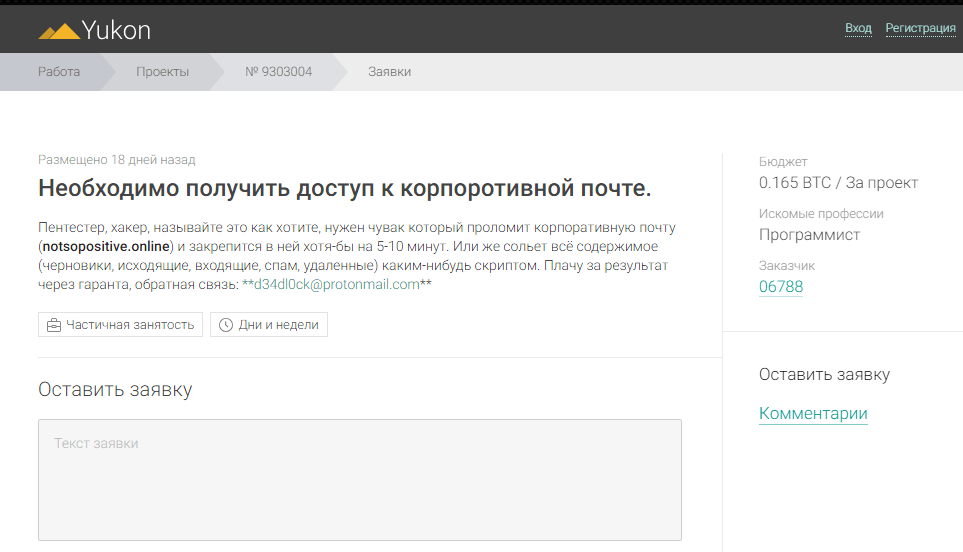
How to be to those who have not heard about Yukon? Here the simplest Google dorks come to the rescue, and the answer is often hidden in the question itself.
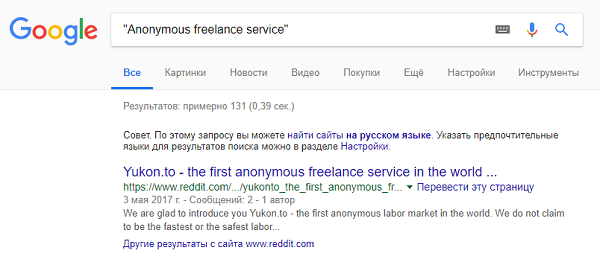
The very first result in the issue - we need the site. A search by nickname showed that d34dl0ck is a very common nickname, therefore there are a lot of people associated with this nickname. It was possible to identify the d34dl0ck we need by the exception method, checking each one.
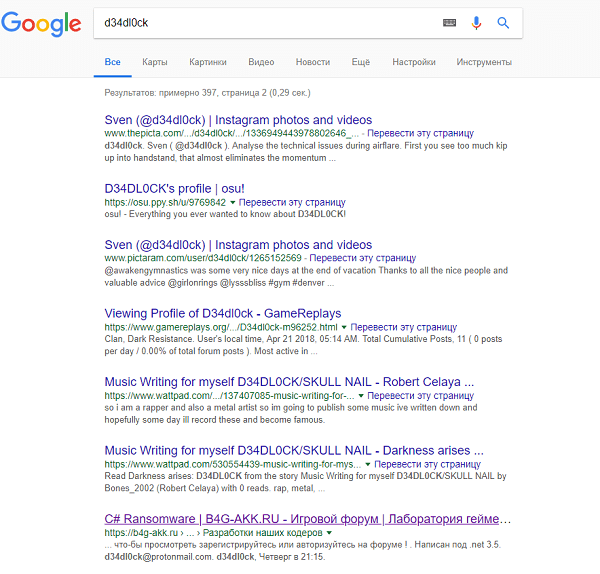
By narrowing the search to the email address, we got a uniquely suitable result.

A message on the forum found that our customer of shadow services has the skills to develop malware.
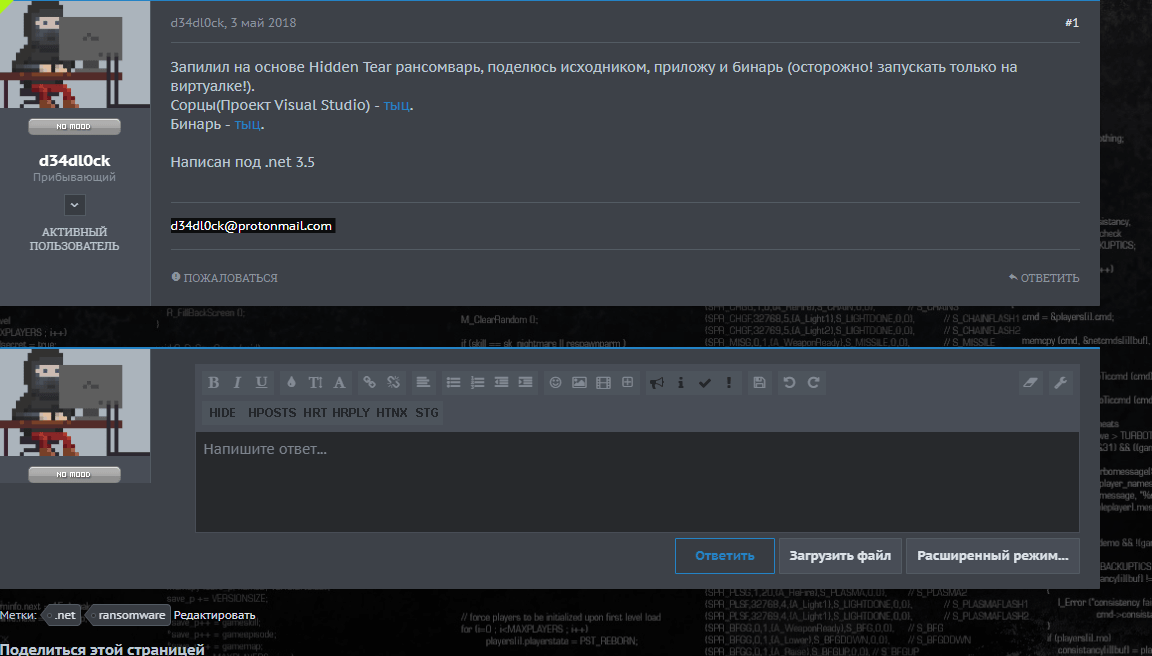

What kind of malware did he write? The archive with the promised source codes was the executable file. The target .NET 3.5 framework points to the most likely development language - C #. A web search for “Hidden Tear” also pointed to C #. But what exactly has changed in the code? Here the .NET Reflector decompiler will help. Observing all precautions when working with malicious code, you need to load the executable file into the decompiler. NET Reflector does an excellent job with decompiling an application. In the list of functions used on one form, GenEthAddress was found, its name most closely matches the question in the Evil guy's wallet number task.
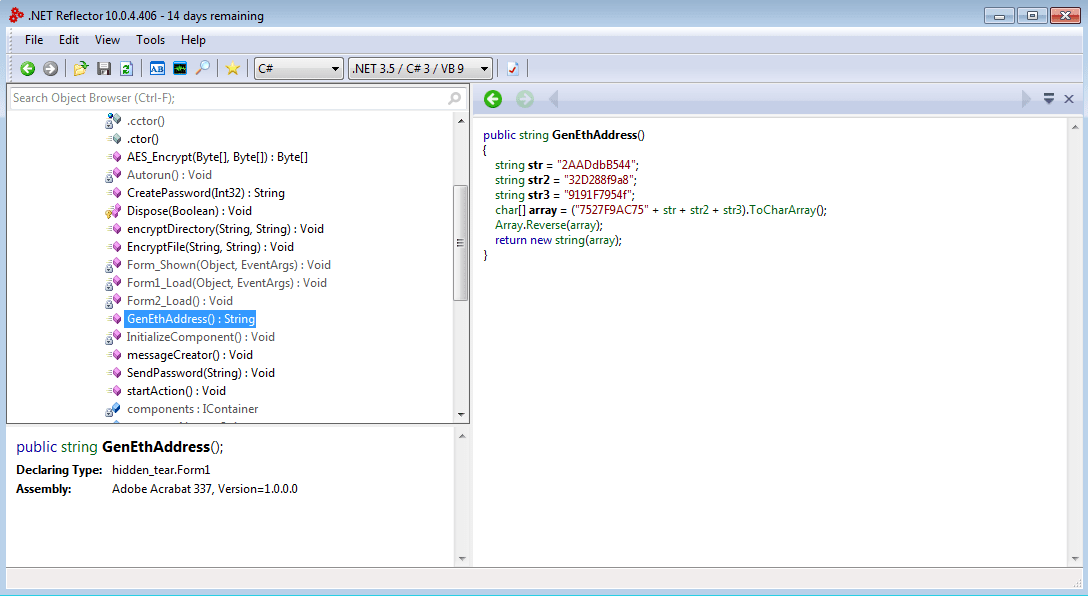
A quick glance at the decompiled code made it possible to understand the algorithm of the “assembly” of a four-line wallet address. Strings of equal length are concatenated into one big one, then it is converted into an array of characters. The resulting array is reversed. The GenEthAddress function is called from the messageCreator function, and the final version of the wallet number is created in it. Before the beginning of the array is substituted '0x'.

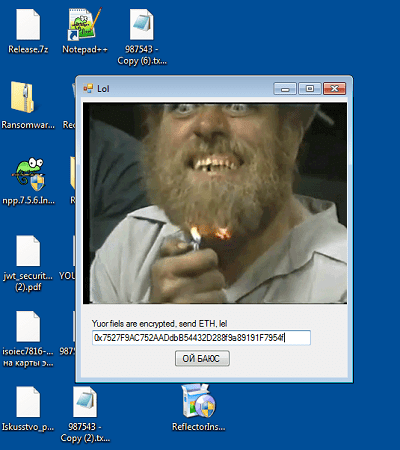
A simpler solution method with the attendant suffering of a virtual machine is to launch the executable file of a virus. The file encryption message displays the ETH wallet address.
The IP address of the notsopositive.online web server, hidden behind CloudFlare, was also possible in several ways. Each task was decided according to the route planned by the organizers, however, participants often found alternative ways.
At the top of the ICO website, you could find a link to a subscription page for company news, and one of the ways to find out the IP address for CloudFlare is to send an email from the server to your email and see the headers. However,
there are others .

Go to the form, specify in it any name and your email address.

In the incoming letter you had to open the service headers and get the following:
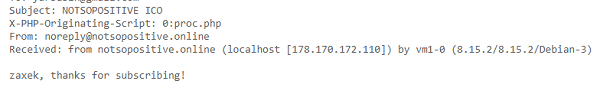
and 178.170.172.110 pass as a flag.
A member with the nickname @ AlexPavlov60 found an alternative way to find a hidden IP address using Shodan. If during the passage the participant already knew the IP address of the FTP server, it was advisable to check the entire subnet for the presence of other Notsopositive servers.
On request:
net: 178.170.172.0/24 product: »Apache httpd » Shodan returns several servers at once, including one with a familiar DNS.

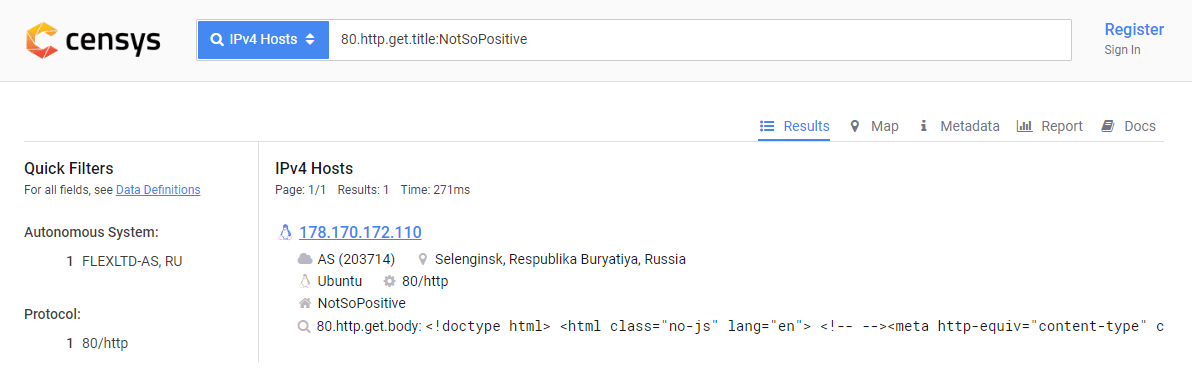
Another shadow search engine that can help us, Censys, was suggested by the participant @rdafhaisufyhiwufiwhfiuhsaifhsaif.
On request:
https://censys.io/ipv4?q=80.http.get.title%3ANotSoPositive, it also returns the desired address.
Of course, there are ready-made solutions for extracting the IP address hidden behind CloudFlare. A
Blablablashenka member
has used the
Hatcloud utility, which
finds a neighboring address from the subnet. It only remained to search the web servers there.
It turned out to be quite easy to find another domain to which this IP address points: it turned out that the PTR record shows all the services on which you can get information about IP, so the cost of the task did not correspond to the complexity. The answer is scamsopositive.com.
James Taylor, CEO
Questions in this thread:
- CEO's car model
- 'Find the CEO's nickname (we know that James Cottone name)
- Facebook: find the CEO's son
- The CEO is connected.
On the ICO page there was a mention of Telegram, however the link did not lead anywhere. It was a small hint for searching a channel or chat NOTSOPOSITIVE:
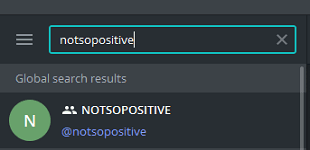
There you could find a CEO account with an avatar and his car.
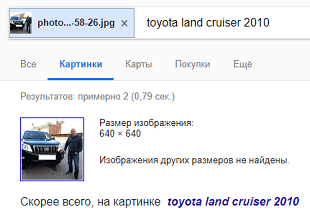
Using the search for pictures on Google it was easy to find the car of James in the photo - this is a Toyota Cruiser.
Next, it was necessary to find the nickname of the CEO, which was not in Telegram. However, it was known that one of his friends was named James Cottone. One of the solutions that we laid out is to use the password recovery service on Facebook, where you can enter a friend’s name to search for your account:

In fact, many services make it possible in this way to find out whether a specific email or phone number is tied to the service. After entering the name and surname of a friend, it was notified that the access code will be sent to the post office:
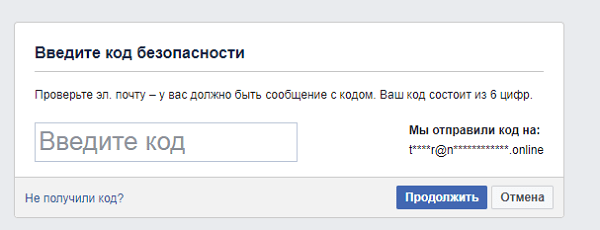
It is not difficult to guess that the mail is taylor@notsopositive.online. Also, one of the options proposed by the participant is to use the anymailfinder.com service, where the email addresses of some of the employees will immediately appear:

Then, knowing the mail, it was possible to go through the recovery process again and see what its avatar looks like:

And then find his page and nickname:
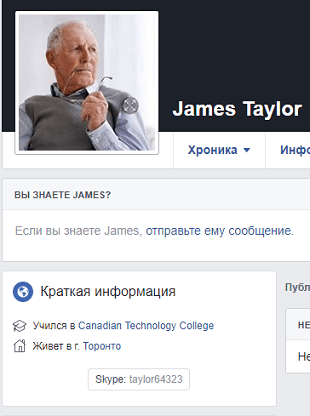
To find his son, it was necessary to take advantage of the Facebook feature: he has the ability to view which publications the user likes. All this can be seen on this
service . The likes put by James revealed the profiles of his wife and son.

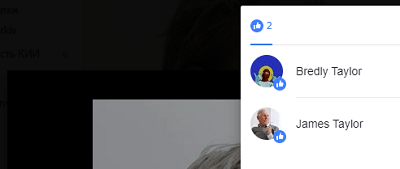
On the page of the son - his login on Tvich (br4yl0r), however it gave us nothing. In the search engines, too, almost nothing. In such cases, if profile pages are not indexed, it is useful to use utilities like namechk.com, which show the employment of nicknames and domain names on different web services. Thus, it was possible to find a profile in Steam, and from it in GitHub - STKLRZSQUAD. Here again it was necessary to know the specifics of the service and see what Bradley laid out on the gist. Next, find this bytecode:
0x606060405234801561001057600080fd5b5061013d806100206000396000f30060806040526004 3610610041576000357c010000000000000000000000000000000000000000000000000000000090046 3ffffffff16806338cc48311461009e575b737527f9ac752aaddbb54432d288f9a89191f7954f73fffff fffffffffffffffffffffffffffffffffff166108fc349081150290604051600060405180830381858888 f1935050505015801561009b573d6000803e3d6000fd5b50005b3480156100aa57600080fd5b506100b36 100f5565b604051808273ffffffffffffffffffffffffffffffffffffffff1673fffffffffffffffffffff fffffffffffffffffff16815260200191505060405180910390f35b6000737527f9ac752aaddbb54432d28 8f9a89191f7954f9050905600a165627a7a72305820a369acc2650e24d84edd29c97cee2db1f5caada8315 81fa2482a002b87404aba0029
and looking for the headers, we realized that this is a smart contract bytecode:
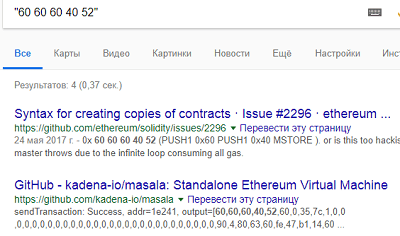
Then we had to use the utility to convert it to opcode, for example,
here . Inside find the already known wallet from another task:
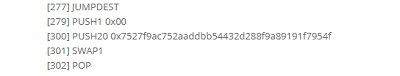
Has the CEO's son ordered an attack on his father's ICO?
Rajesh Bishop, System Administrator
Questions in this thread:
- Find out your system administrator's personal website.
- Try to find sysadmin's personal email
- What is sysadmin's favorite beer brand?
- Where sysadmin drank beer recently
As usual, it was necessary to start with typical intelligence in order to discover the domain mail.notsopositive.online, where using nmap to find a self-signed certificate that was valid for another domain:
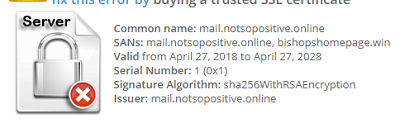
Then, by making an ANY query on the bishopshomepage.win DNS, you could find his email address:

Then - answer the question about your favorite beer from Rajesh. Many beer lovers are familiar with a social network such as Untappd (it can be found on the query “beer social network”). One option was, as always, to use other search engines:
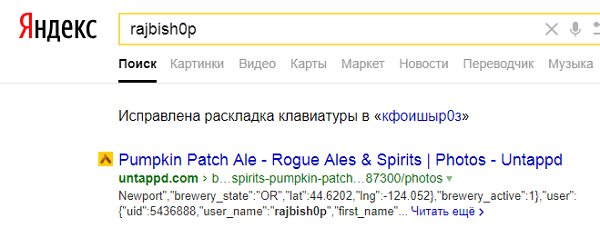
Further it is already easier: to find the profile of the sysadmin, in it the only photo with the hashtag.
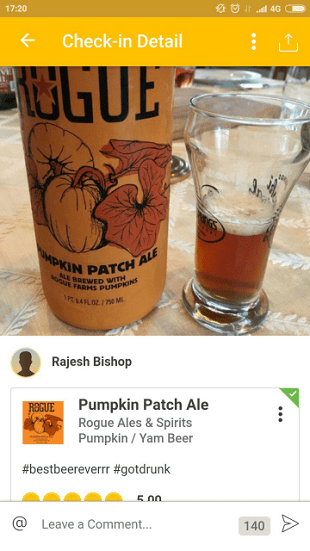
However, there are no hashtags in this social network, which should have given rise to the idea that you need to search for others: VKontakte, Facebook, Twitter and Instagram. In the last one and you could find a photo with a geotag:

Headquarters NOTSOPOSITIVE
The search for headquarters again demanded that the contestants make efforts and dig up all social networks. The answer was on LinkedIn:

Mark Fox, CSO
To understand where the contest starts with CSO, it was necessary to use fuzz.txt again and find in the root directory of the web file an .DS_Store file, which macOS reserves for itself. Having decrypted it using the online utility
https://labs.internetwache.org/ds_store/ or by viewing a binary file, you could find the following lines:
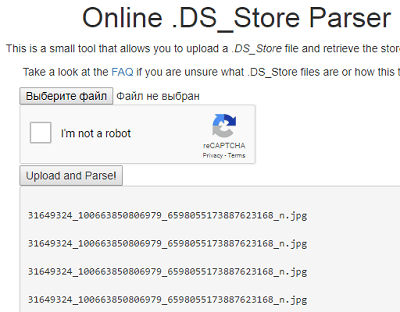
At the address and really lay a photo of a man. In addition, one of the features of Faceboock: earlier, when saving a file, the second numeric value was the photo ID. So you could find a profile:

In the profile and corporate address Brand:
mmmmmmmmfox@notsopositive.onlineResults
This year more than 500 people took part, and almost 300 people coped with at least one task.
Noyer_1k again became the
winner , whose efforts were rewarded with Apple Watch smart watches, invitations to the forum and souvenirs from the organizers. The second place,
Power Bank , an invite to the forum and souvenirs earned
Kaimi0 . Third place, the book Open Source Intelligence Techniques: Resources for Searching and Analyzing Online Information, invitation and souvenirs took
empty_jack . Final results table:
| # | Nickname | Points |
|---|
| one | Noyer_1k | 816 |
| 2 | Kaimi0 | 816 |
| 3 | empty_jack | 816 |
| four | Antxak | 786 |
| five | V88005553535 | 661 |
| 6 | jerh17 | 611 |
| 7 | shsilvs | 556 |
| eight | someotherusername | 526 |
| 9 | trace_rt | 491 |
| ten | shadowknight | 481 |
Congratulations to the winners!
Analysis of previous competitions: