 Enigma encryption machine. Rumor has it that this is the first device where the NSA's backdoor has been deployed. This happened after WWII in collaboration with the manufacturing company Crypto AG. Since then, the introduction of such backdoors has become almost standard practice for American intelligence.
Enigma encryption machine. Rumor has it that this is the first device where the NSA's backdoor has been deployed. This happened after WWII in collaboration with the manufacturing company Crypto AG. Since then, the introduction of such backdoors has become almost standard practice for American intelligence.Many talk about the omnipotence of the American intelligence services: they say they make hardware bookmarks in the CPU (
Clipper chips ) and leave backdoors in encryption standards at the stage of creating these standards, as was the case with the Dual_EC_DRBG algorithm adopted by NIST as the RNG standard. Snowden documents showed that the NSA paid RSA for incorporating this RNG into its software.
But in reality, even their influence is not unlimited. According to the
WikiTribune source from the International Organization for Standardization (ISO), in April of this year, an entire discussion broke out between experts from the international group of security experts ISO and employees of the US National Security Agency (NSA), who presented new block ciphers for the Internet of Things.
The source said that the final vote on the NSA proposal was held in Wuhan, China, where the 26th meeting of the
ISO / IEC JTC 1 / SC 27 working groups on safety standards was held on April 16-20, 2018. Experts from several countries, including allies of the United States, voted negatively at the suggestion of the American delegation.
This decision of the experts is explained by the “refusal of the American delegation, which included representatives of the NSA, to provide a standard level of technical information to continue [review their application]”
The source said that the final vote was preceded by disputes over several weeks, but the
NSA did not provide the necessary technical details on the algorithms common to such processes. That is, the committee was ready to consider their codes on a par with any others, but the NSA simply declared “Believe us”, which the committee did not agree to. Probably, taking into account the entire previous history of the NSA.
We are talking about families of block ciphers Simon and Speck.
Block cipher is a type of symmetric cipher. Theoretically, the concept allows for a certain level of security to be achieved by combining simple substitution and permutation operations.
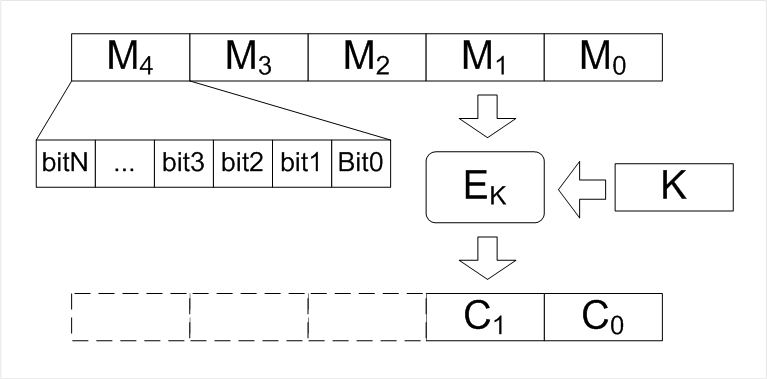 The general scheme of the block cipher
The general scheme of the block cipherThe main algorithms of modern block ciphers were developed by IBM in the work on the block cipher "Lucifer", released in 1970. In 1977, a DES (Data Encryption Standard) cipher was developed on its basis, adopted as the NIST standard in 1981. Finally, in 2002, the standard was announced as the Randall cipher (Rijndael), also known as the Advanced Encryption Standard (AES).
 The permutation-permutable network of the Randal block cipher (AES) adopted as a NIST standard in 2002
The permutation-permutable network of the Randal block cipher (AES) adopted as a NIST standard in 2002Created in 2013, Simon and Speck from the NSA are a family of lightweight block ciphers adapted for the Internet of Things, that is, for devices with very weak processors and a very small amount of memory. Simon is adapted for hardware implementation, and Speck - for software. Detailed information about the ciphers can be found in
the NSA official repository on Github.
The ISO standard for cryptography in IoT devices was adopted in 2012 and provides for the use of two lightweight block ciphers Present and Clefia. In 2014, the NSA offered to add Simon and Speck ciphers to the standard. Four years passed, but the NSA did not publish the security analysis and description of the algorithms adopted in such cases. The authors of the cipher prepared
such a document (this is the most detailed description of what was found). But the document obviously did not satisfy the ISO experts. The description probably does not include some important information about the details of the Simon and Speck permutation-permutation network.
ISO sets agreed standards for a wide range of products, services and measurements in virtually all industries, including technology, manufacturing, food, agriculture and health. In this case, the relevant committee considered the recommended encryption technology, which “improves the protection in the Internet of Things devices”. These include many devices, including various home appliances: smart speakers, refrigerators, lighting and heating systems, as well as wearable gadgets.
According to the source, the NSA insisted on adopting these standards as an ISO recommendation to get NIST approval, after which they will become the standard for all US government agencies and related companies.
This vote is another unsuccessful attempt by the NSA to promote these ciphers as ISO standards. Last time they were
rejected at the September meeting. During the current discussion in April, they again recalled the Dual_EC_DRBG story and quoted Snowden's documents. Some delegates expressed a general distrust of the NSA. For example, the Israeli delegate Orr Dunkelman said: “I do not trust the developers. There are quite a few people in the NSA who think their job is to undermine the standards. My job is to protect standards. ”
Given the established reputation, the NSA will find it difficult to establish its algorithms as standards.
We announce the action “More cyber defense to sports”!

GlobalSign joins the celebration of the most ambitious event of all athletes and football fans - WORLD FOOTBALL CHAMPIONSHIP 2018 and GIVEN 1 YEAR SSL PROTECTION! *Terms of action:* When you purchase any one
- year
DV-OV or
EV -level
SSL certificate , you get the second year as a gift.
• The promotion applies to all sites of sports.
• The promotion is valid only for new orders and does not apply to partners.
• To take advantage of the offer,
send a request on the website with the promotional code:
SL003HBFR .
The promotion will last until July 15, 2018.
You can get additional information on the promotion from
GlobalSign Russia managers by phone: +7 (499) 678 2210.
MORE PROTECTION with GlobalSign!