
Hackers gained access to the main mail server of the international company Deloitte. The administrator account for this server was password protected only.
Independent Austrian researcher David Wind received a reward of $ 5,000 for detecting a vulnerability on the Google Intranet login page.
91% of Russian companies hide data leakage facts.
Such news almost every day can be found in the Internet news feeds. This is direct evidence that the company's internal services must be protected.
And the larger the company, the more employees there are and the more difficult the internal IT infrastructure is, the more urgent for it is the problem of information leakage. What information is interesting to attackers and how to protect it?
What information leakage could harm the company?
- information about customers and transactions;
- technical information on products and know-how;
- information about partners and special offers;
- personal data and accounting.
And if you understand that some information from the above list is available from any segment of your network only upon presentation of your login and password, then you should think about improving the level of data security and protecting them from unauthorized access.
Two-factor authentication via hardware cryptographic media (tokens or smart cards) has earned a reputation as very reliable and, at the same time, quite simple to use.
We write about the benefits of two-factor authentication in almost every article. You can read more about this in articles on how to protect your Windows domain account and email .
In this article, we will show you how to use two-factor authentication to access the internal portals of your organization.
For example, we will take the most suitable for corporate use model Rutoken - USB cryptographic token Rutoken EDS PKI .

Let's get down to setting it up.
Step 1 - Server Setup
The basis of any server is the operating system. In our case, this is Windows Server 2016. And along with it and other Windows operating systems, IIS (Internet Information Services) is being distributed.
IIS is a group of Internet servers, including a web server and an FTP server. IIS includes applications for creating and managing websites.
IIS is designed to build web services using user accounts provided by a domain or by Active Directory. This allows the use of existing user databases.
In the first article, we described in detail how to install and configure the Certification Authority on your server. Now we will not dwell on this in detail, but we will assume that everything is already set up. The HTTPS certificate for the web server must be written out correctly. It is better to check it immediately.
IIS version 10.0 is built into Windows Server 2016.
If IIS is installed, then it remains to be configured correctly.
At the stage of selecting role services, we checked the check box for Basic authentication .

Then, Basic Authentication was enabled in the IIS Manager .

And indicated the domain in which the web server is located.


Then they added a site binding.

And chose the SSL options.

This completes the server setup.
After performing these actions, only a user who has a token with a certificate and a token PIN can access the site.
Once again, we remind you that according to the first article , the user was previously issued a token with keys and a certificate issued on a template of the type User with a smart card .
Now go to setting up the user's computer. He should configure the browsers that he will use to connect to the protected websites.
Step 2 - Setting up a user's computer
For simplicity, let's assume that our user has Windows 10.
Also suppose that he has the Rutoken Drivers for Windows kit installed.
Installing a set of drivers is optional, since most likely token support will arrive via Windows Update.
But if this doesn’t happen, installing Rooken Drivers for Windows will solve all the problems.
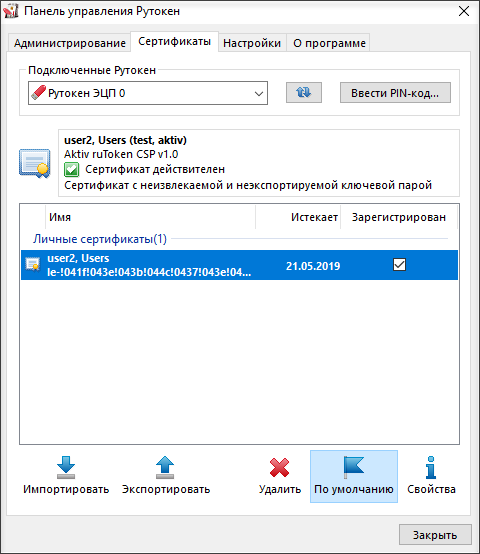
We connect the token to the user's computer and open the Rutoken Control Panel.
On the Certificates tab, check the box next to the required certificate if it is not worth it.
Thus, we checked that the token is working and contains the necessary certificate.
All browsers except Firefox are automatically configured.
There is nothing special to do with them.
Now open any browser and enter the address of the resource.
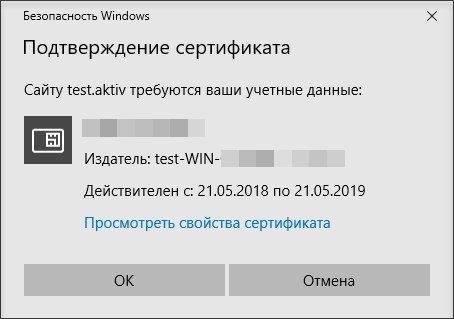
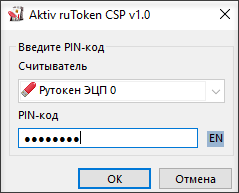
Before the site loads, we will have a window for choosing a certificate, and then a window for entering the token PIN code.

If Aktiv ruToken CSP is selected as the default encryption provider for the device, another window will open to enter the PIN code.
And only after its successful input in our browser will open our site.
For Firefox, you need to make additional settings.
In the browser settings, select Privacy and Protection . In the Certificates section, click Protection Device . The Device Management window opens.
Click Download , specify the name of the Rutoken EDS and the path C: \ windows \ system32 \ rtpkcs11ecp.dll.
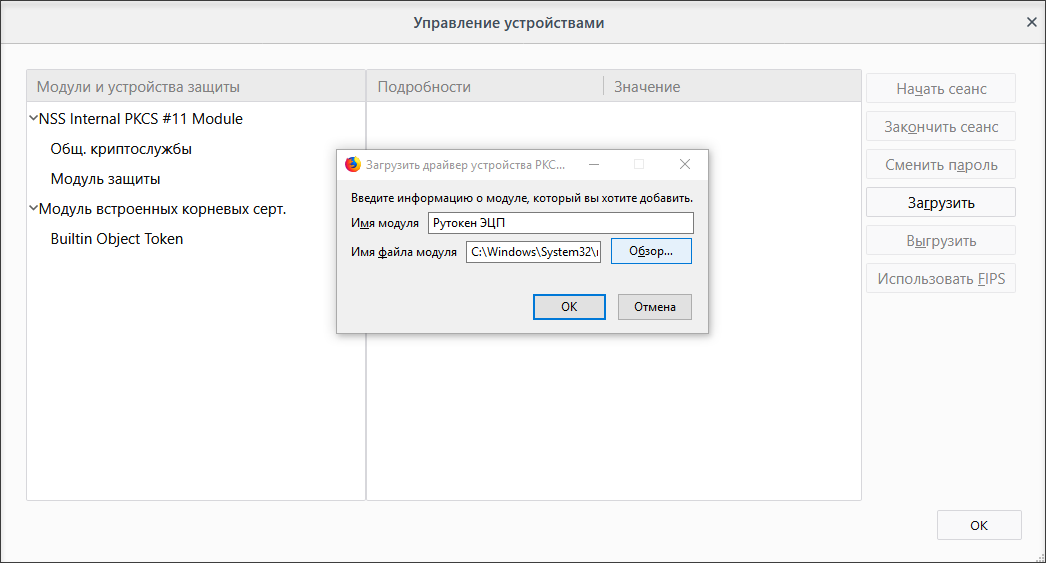
That's all, now Firefox knows how to handle the token and allows you to enter the site using it.
By the way, logging in tokens to websites also works on Macs in Safari, Chrome and Firefox.
All you need to do is install the Keychain Support module from the Rutoken website and see the certificate for the token.
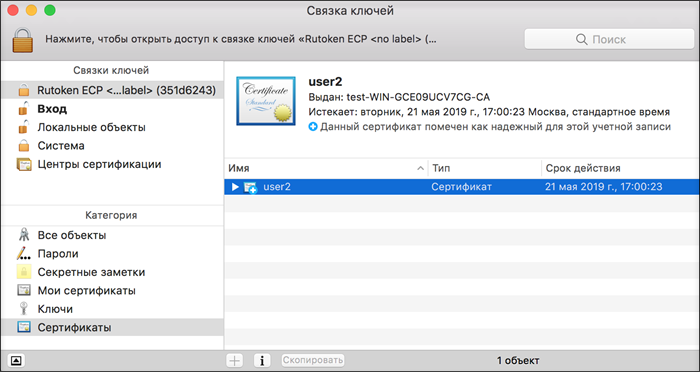
You do not need to configure Safari, Chrome, Yandex and other browsers, you just need to open the site in any of these browsers.
The Firefox browser is configured almost as well as in Windows (Settings - Advanced - Certificates - Protection Devices). Only the path to the library is slightly different / Library / Akitv Co / Rutoken ECP / lib / librtpkcs11ecp.dylib.
findings
We have shown you how to configure two-factor authentication on sites using cryptographic tokens. As always, we didn’t need any additional software for this, except for the Rutoken system libraries.
You can do this procedure with any of your internal resources, you can also flexibly customize groups of users who will have access to the site, however, like everywhere else in Windows Server.
Do you use another OS for the server?
If you want us to write about setting up other operating systems, write about it in the comments to the article.