I found out that I’ll be performing here just 20 minutes ago from Twitter, and I thank Jason Scott and you, ladies and gentlemen, who will be at the Penn & Teller Theater today!
(Skyler means that he will talk about hacking methods that magicians like to show, Penn and Teller - blowing famous American illusionists) .
So, I'm Skyler Town, a professional hacker and physical security researcher, my personal site is at schuylertowne.com, Twitter page is @shoebox.
Today I will reveal to you secrets of magic that you do not know about. We'll talk about how to open a car with a popsicle stick, how to open a safe using a grinder, and how to open the handcuffs with a beer can. We will also talk about how to open an electronic safe using a 9V “Krona” type battery, how to open a tubular lock with a ballpoint pen, how to crack a combination lock on a suitcase using an anti-theft label on a DVD box.
That is, we will discuss such types of hacking as shimming, spiking, decoding, overlifting, vibrating hacking, and so on.
At first we will talk about cars. In cars, the so-called waffle lock with a toggle switch, wafer tumbler lock, is commonly used. It consists of "waffles" - thin plates with shaped holes located inside the lock cylinder. The springs prop up these plates so that one “waffle” is pushed into the upper part of the chamber, the next to the lower and so on. When the “correct” key is inserted into the slot of the lock, it assembles these “wafers” together in the middle part of the lock, pulling them out of the chambers, and thus creating the opportunity to turn the key.

In the next slides, I will remove these springs so that they do not interfere with seeing the plates rotate. I'll show you how the castle works in an animated video.
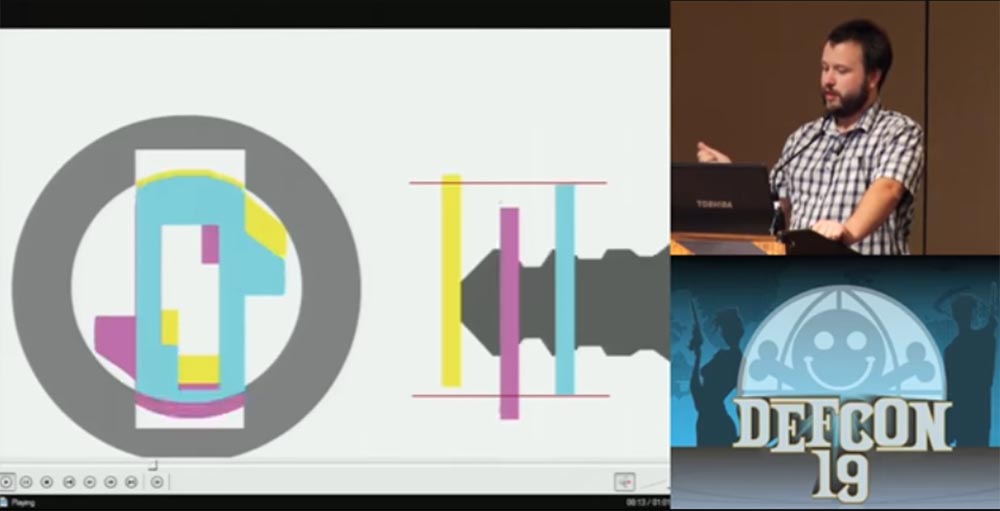
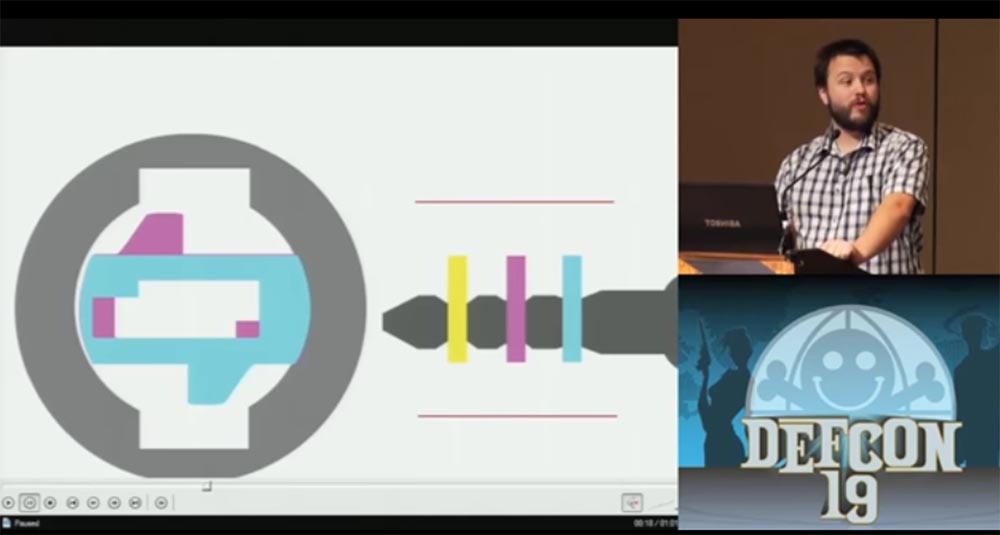
Such a lock can be opened with the power of hacking technology overlifting, this is its weak point. If, instead of the original key with a cut beard, a key blank is inserted, it will push each plate onto itself so that they are taken out of the chambers where they are usually hidden and locked in opposite chambers, but at the same time will tend to return to their native chambers under the action of springs .
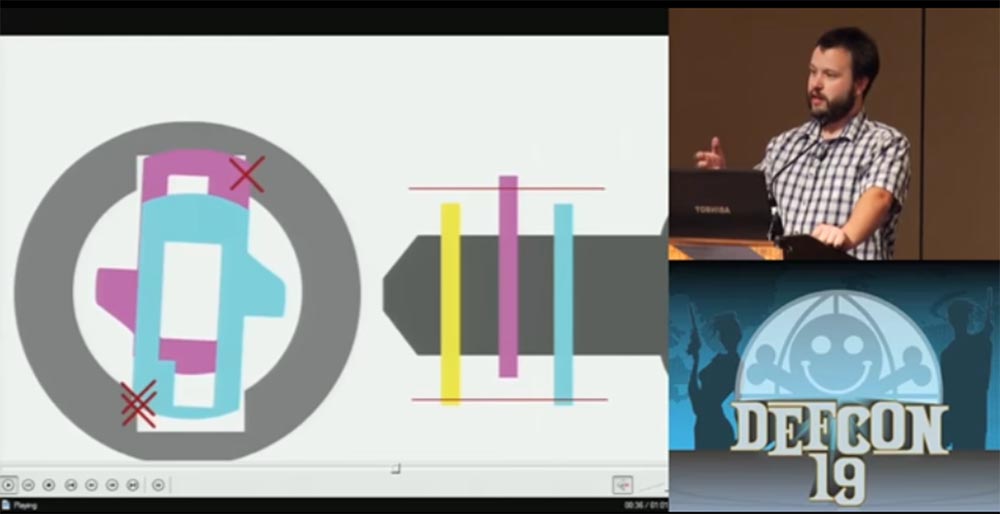
This pressure is maintained, and when you pull out the workpiece, the plates occupy a position in the center of the lock, as if you were using a real key.
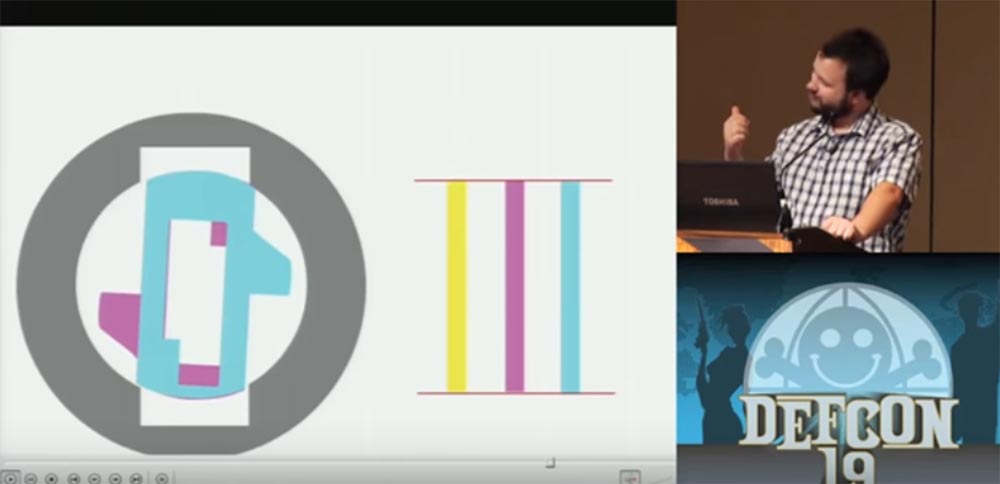
Now it is enough to enter into the lock only the very tip of the workpiece, so that he picks up the first plate, to which all the others are pressed, and turn it, after which the lock opens.
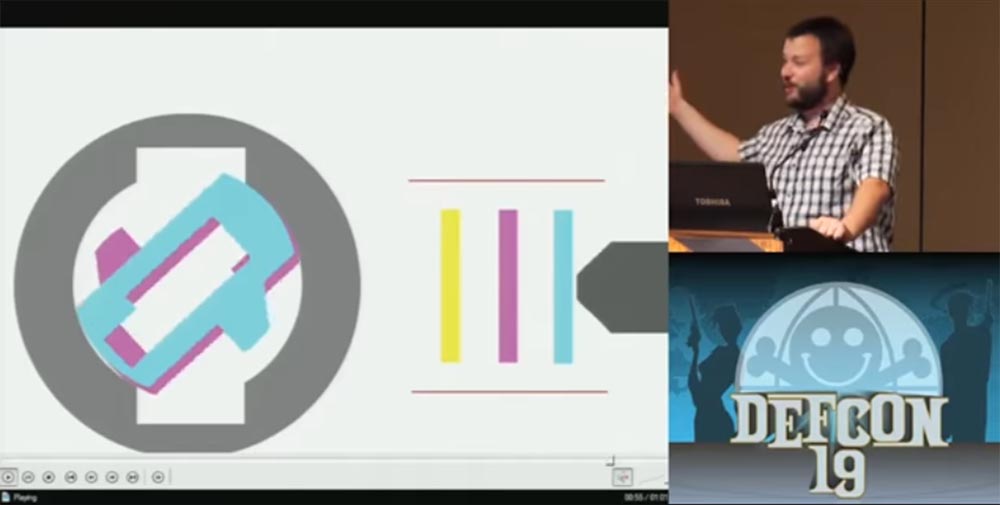
I thought about the fact that, besides the blank, I could replace the key to the door of my car, and decide to try the ice cream sticks, you know how they look. The first attempt took place in the winter. As you know, this stick is usually wet after ice cream, and this fact should have been taken into account. I opened the driver's door and drove, everything worked out. But then night came, and the moisture from the wand turned into ice in the lock, and after I tried to open the door again in the morning, the lock stopped working altogether. But in the spring I didn’t open the passenger door more than once.
The main thing for me was not the way of hacking itself, but its idea. That is, I could leave the house without any master keys, but I still had the opportunity to steal a car with the help of available tools. Later we will talk about the ethical side of the problem, but I assure you, I have never even used the master keys for the doors of my house, because it does not belong to me, I rent it. I am very strict about ethics. I often travel long distances. If I make a 24-hour trip and I want to drink Coca-Cola, and everything is closed, I could “let” myself into the store, take a bottle and leave money on the counter, but this is a recipe for action that leads to disaster.
My next idea was to crack the lock for Cryptonite bikes with the usual BIC ballpoint pen. The Cryptonite 4 castle was created in 1976 by Michael and Peter Zeinami to replace traditional chain locks for bicycles. Due to its revolutionary concept, this U-shaped lock is an exhibit of the Museum of Modern Art.


Now I will show you how I do it.
Skyler spins the fountain pen, pulls out the writing part with the ball rod, takes the case with the hollow upper part in one hand and inserts this part of the handle into the lock hole. He explains that the lock's core turns in one direction, but the handle must be scrolled back and forth to release the lock. Then Skyler starts to scroll it in the hole in different directions, slightly pressing on the lock, and after 10-25 seconds the lock bracket is disconnected.
Why did I manage to do this? "Kryptonite" is a tubular lock, which consists of spring-loaded studs in a cylindrical body. One part of the body is fixed, the second rotates. I apologize for these slides, so I’m still not a graphic designer.

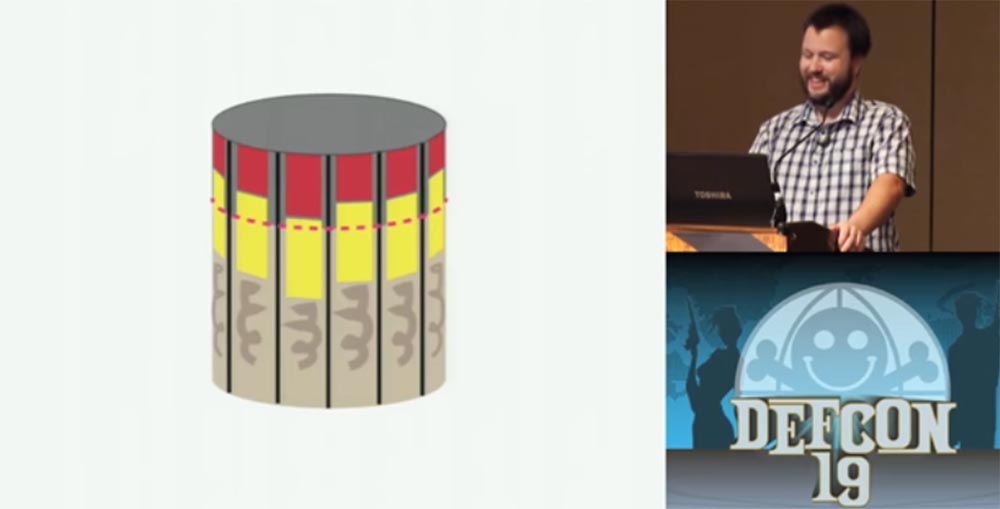
At the end of the key, which is a hollow cylinder, there are cutouts that correspond to the height of the studs inside the lock. Each stud has a unique height, which, in turn, must match the depth of the corresponding key cut. The inserted key presses each pin so that it releases the rotating part of the lock case and it turns freely with the key. When you insert something soft into the key hole, the studs counteract its pressing differently depending on its length. But since the plastic is much softer than the metal of the key, they are finally installed in one position and fall below the rotating part of the body, which allows it to turn and open the lock.
When I studied the Kryptonite locks, I learned that there are two types of tubular locks. One type is called ACE II - it uses springs from different metal, so you can not squeeze the studs at the same time with one tool so that they occupy the same height position - some studs will sink inward, while others will stick out. However, there are tools for hacking and such locks, but they are not perfect.
In the late 1980s, a man proposed to place the ACE II system inside cheap Chinese tubular locks, which further worsened their reliability. Mark Tobias, an expert in the field of locks, noted that the same flaw was repeated in Kingsman locks. The Smithsonian Institution has 17 corporate records made from 1972 to 2001, until Cryptonite was acquired by the Ingersoll Rand tools and equipment company. I will study them, and if I can find the name of this person, I will probably publish it as a warning.
Now let's move on to opening handcuffs with the help of a beer can. I'm a little nervous, but just in case I brought here the key to the handcuffs in case something goes wrong with my can of Coors beer. Consider how the handcuff mechanism works.

Below is the mechanism of capture - locking plate, which fixes the teeth of the cuff of the handcuff. A spring is located above it, which pushes the bar down, so that the teeth will engage when the handcuffs click. A duplicated striker is located above. When turning the key presses the locking bar up, the teeth release, and the handcuff opens. The important thing is that this blue thing at the top prevents you from pushing the locking bar up until the key is used.
I was arrested several times; three times out of five I was handcuffed.

The next slide shows how the teeth of the striker plate engage with the teeth of the cuff brace.
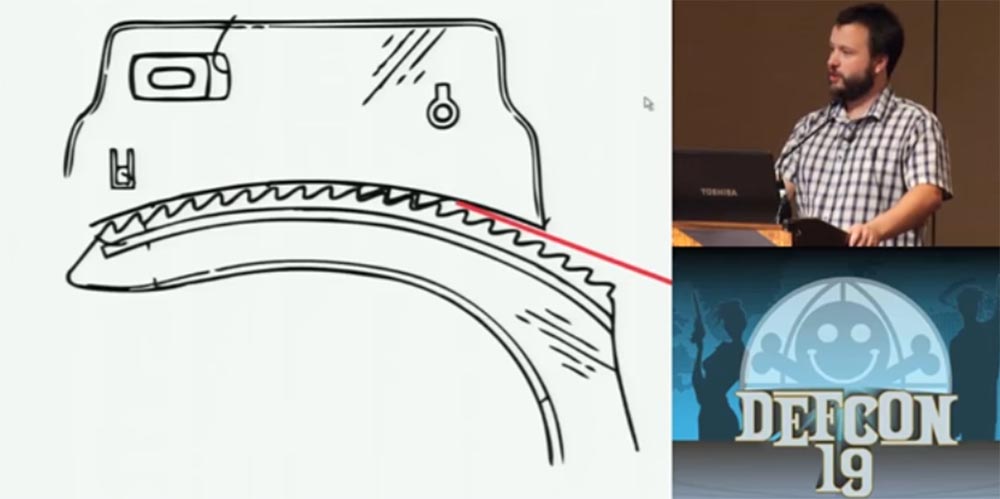
If you manage to insert a thin metal plate between the teeth of both parts, it will block the teeth and prevent them from engaging.

Now I will show you how it works. I have with me a convex strip cut from the wall of a Coors beer can, which sells for $ 14 for 6 pieces. I cut off a strip of small width with scissors and take handcuffs. As I said, I adhere to strict ethical rules, but I imagine a lot about how I would act in a variety of situations. So, if I was chained in handcuffs and there was some kind of a can lying on the ground, I would kick it, tear my teeth until I could tear off such a thin strip of metal from it in order to free myself from my captors.
Skyler locks the handcuffs, first on one hand, then on the other, takes the cut strip of metal and starts pushing it between the teeth of the handcuffs, saying that the maximum time it took him to open was 10 seconds. A few seconds passed, something clicked in the handcuffs, and Skyler says: “Badly gone!”. Apparently, the plate broke in the castle. After that, Skyler takes the key and in turn opens the handcuffs with the key. There is laughter in the hall.Well, this time it did not work out, but I assure you that with the banks of the diet drink Sunkist it works out, they act amazingly. Coors is probably made of too thin tin. If the spring is strong enough, then a thin tin, when pushing it between the teeth, is folded into a corrugated strip, which can make you even worse as it gets stuck in handcuffs.
A volunteer who wants to try this experiment on himself is suitable for the speaker. Skyler gives him handcuffs, and throws the key to the other guy in the room.
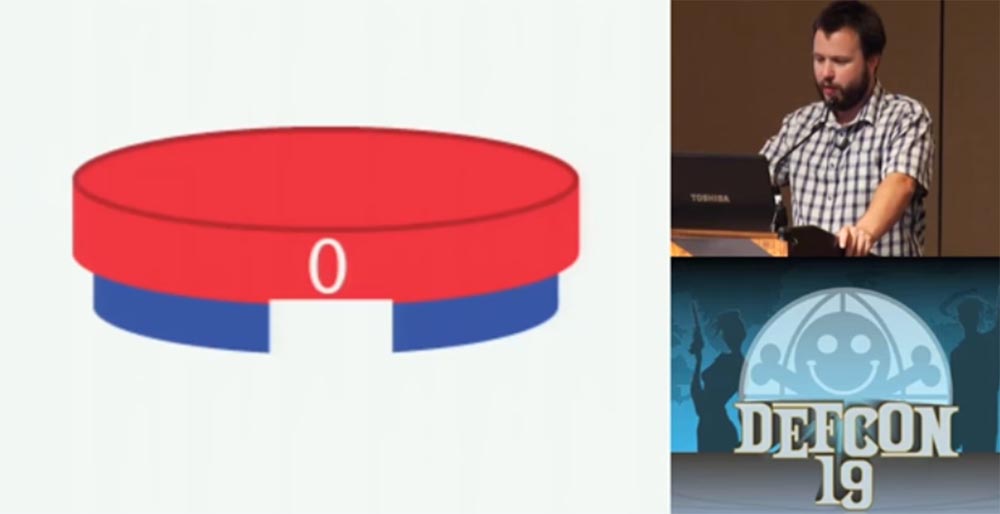
And now I will tell you about the technology of hacking code locks. These locks are commonly used for "diplomats" and luggage. They contain several wheels with numbers on the outer side of the rim. Each of these wheels (red) contains inside a wheel of smaller diameter (blue) with a rectangular cutout under the figure. This cutout interacts with the castle's prong. Usually there are 3 teeth in the lock, and if all 3 enter the slots of the wheels, they will release the bracket and the lock will open.
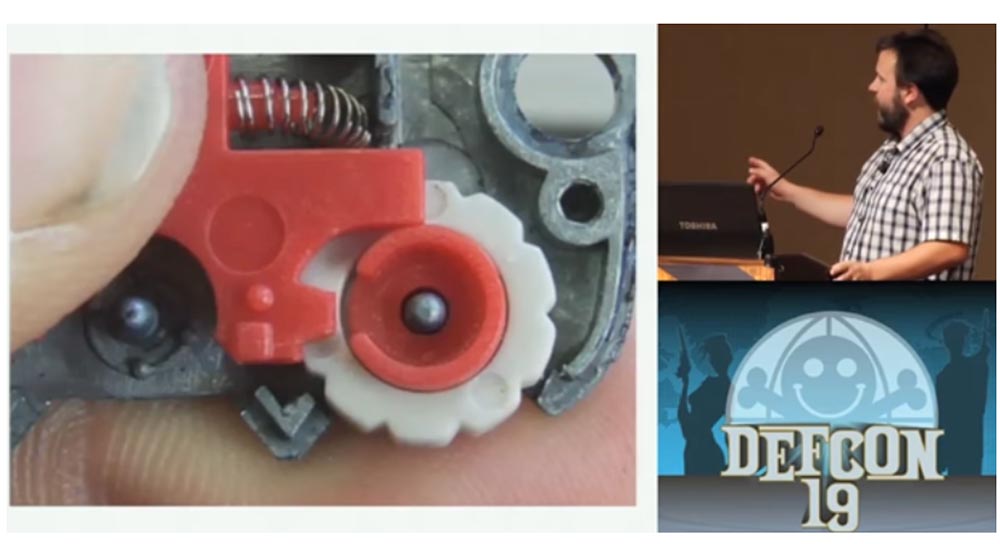

You need to take a small strip of metal, taken out of the anti-theft label, which is usually glued to the box with a DVD disc. This is a small rectangular piece of white or black plastic that serves to protect boxes with video games, movies and so on from being stolen.

These labels contain 2 strips of metal, very thin and perfectly suitable as wedges - master keys. This strip can be used for a variety of operations, for example for jamming parts of the lock. In the case of combination locks, such a thin wedge is inserted into the slot of the wheel and turns it. Now I will show you the animation, where you can see the whole process of hacking code, digital locks.
We insert a strip between the outer license wheel so that it rests on the rim of the inner wheel, and begin to rotate the license wheel.
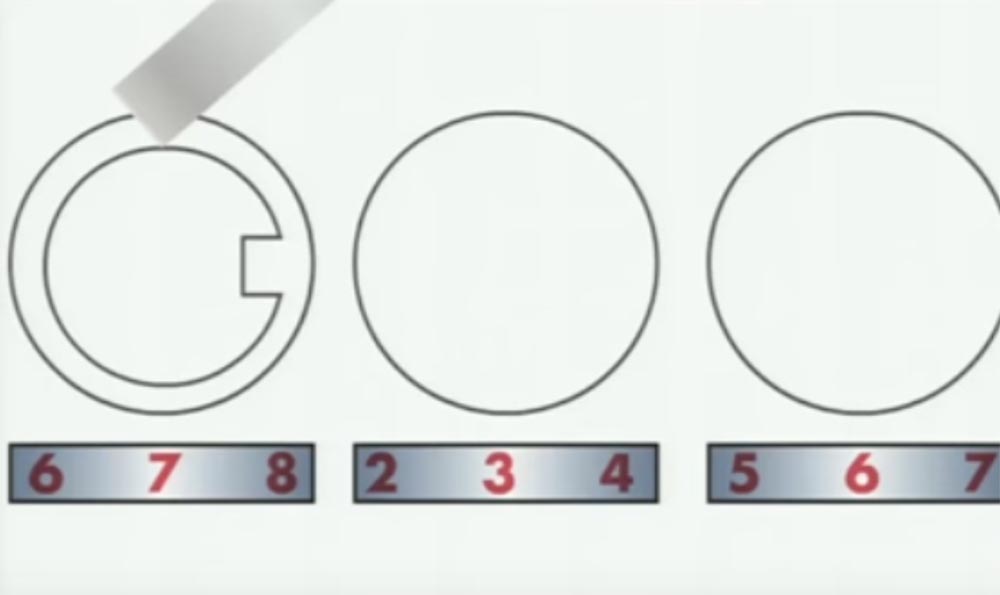
When the corresponding figure is established, the strip will fall into the slot of the inner wheel.

So, the first digit is 5. We continue further, swap our master key to the next wheel and begin to rotate it. The next correct figure is also 5.

The last figure is 1, and in this position, with the “551” combination, all the slots of all the wheels are in the same position. Now, if you rotate all the wheels at the same time, then they also all 3 will simultaneously engage the teeth.
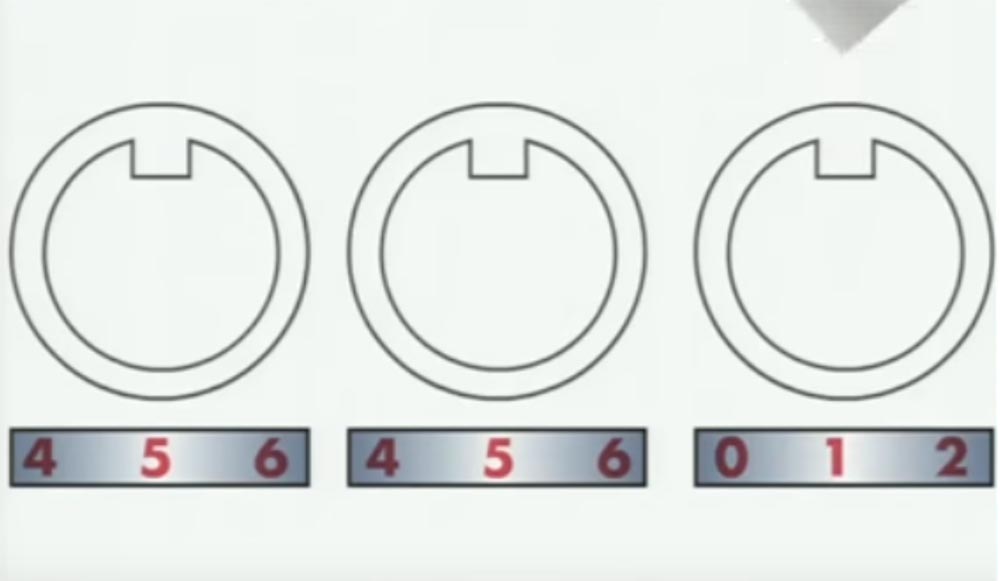
So, we turn all 3 wheels together, try to open them, turn all three again, try to open them and continue until a click is heard and the lock opens.
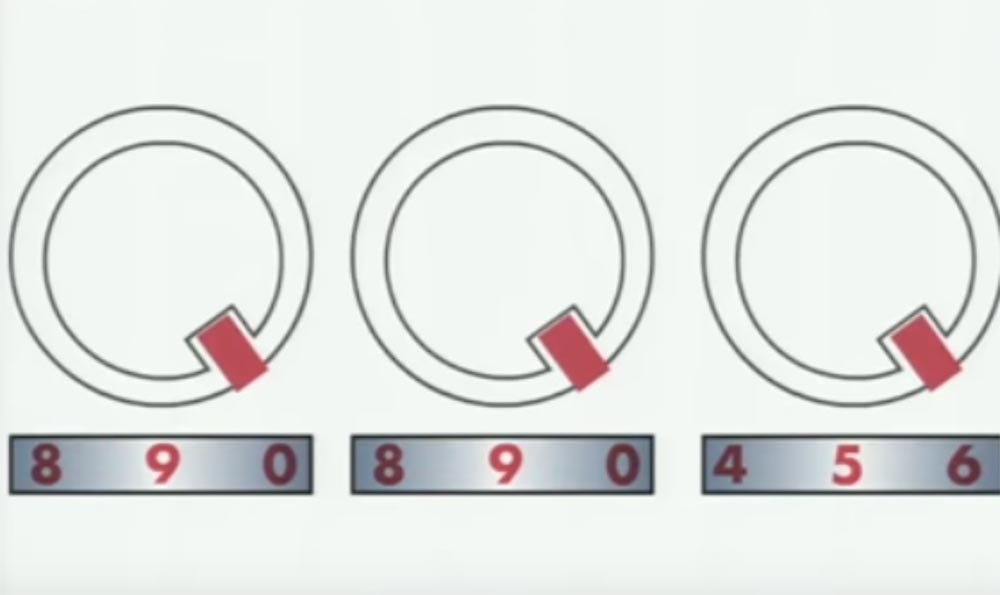
Thus, we broke the lock, the correct code of which was the combination "995".
And now for the grinding machine. It can be used to open safes. Now I will quickly explain how the safes work.

The main part of the safe lock are discs, or wheels with slots, similar to the wheels of a digital lock.
 Skyler's name is from the hall - the guy managed to get rid of handcuffs!
Skyler's name is from the hall - the guy managed to get rid of handcuffs!- opened? Wonderful! - Skyler applauds a volunteer, and he is supported by the whole hall. - He managed to do this by using a double strip of metal, since the single was too thin.
We continue. Between each wheel there is a protrusion, which we call the "front sight". Each "front sight" hooks the next wheel so that they are tied together. When you rotate the lock knob several times, you lift each wheel of the lock with one wheel, which is directly connected to the dial of the code dial. So as soon as you lift the last wheel, you will take it back. Then you quickly turn the wheel with the second code number twice and move it backwards. The same should be done with the third wheel, that is, to bring them out of engagement with each other.

It is important in such a lock that each wheel can rotate independently of the other. Here is what these wheels look like - a red rectangle indicates the locking bar.

When all the wheels are positioned in the right direction, the striker plate falls into the slot and the safe opens - this is very simple.
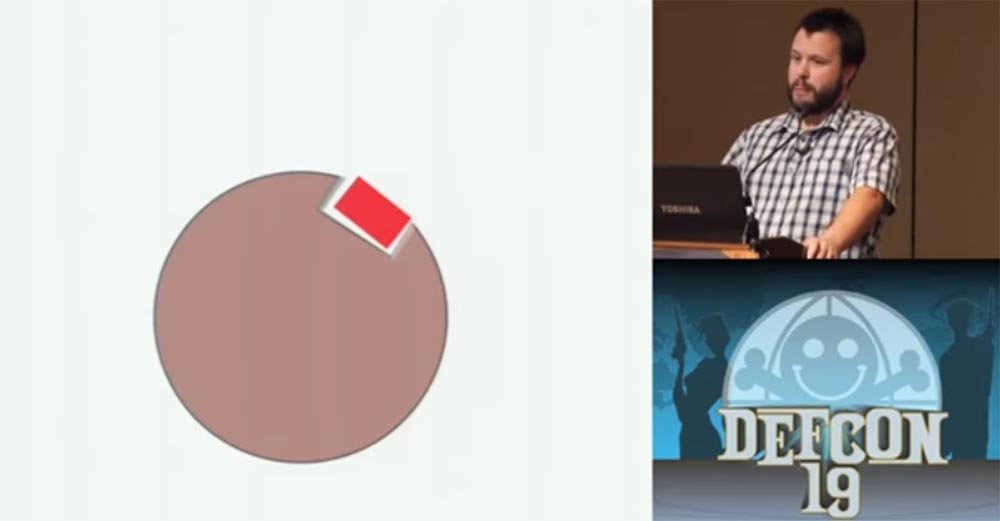
In the usual, not “super-safe” safe, the locking plate of the closed lock is located in this position.
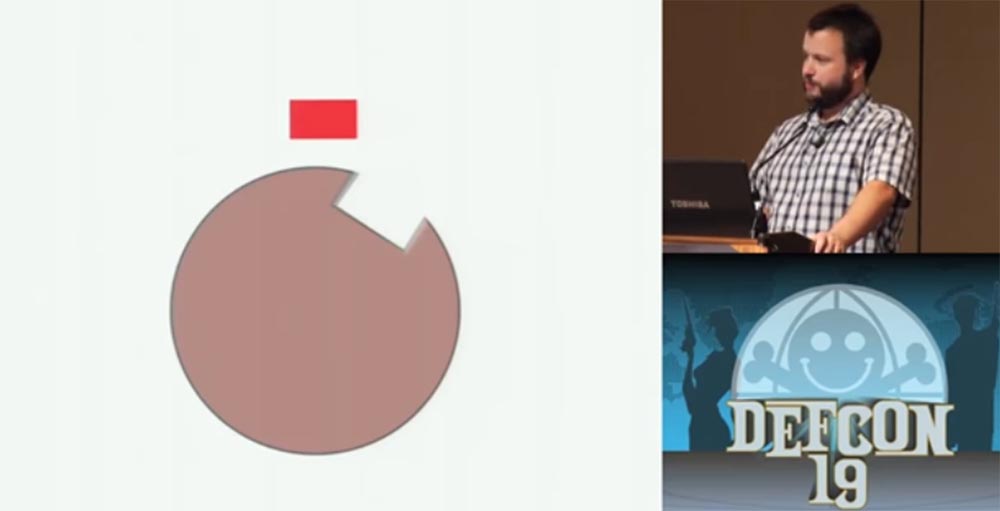
If a vibration impact is applied to the dial of the lock, then under its influence the wheels will tend to occupy a position so that the hard part of the disk turns down and the light part, that is, the part with the slot, is at the top. Thus, all the wheels will gradually occupy the position of the slot up, after which the locking bar will fall there and the safe will open.
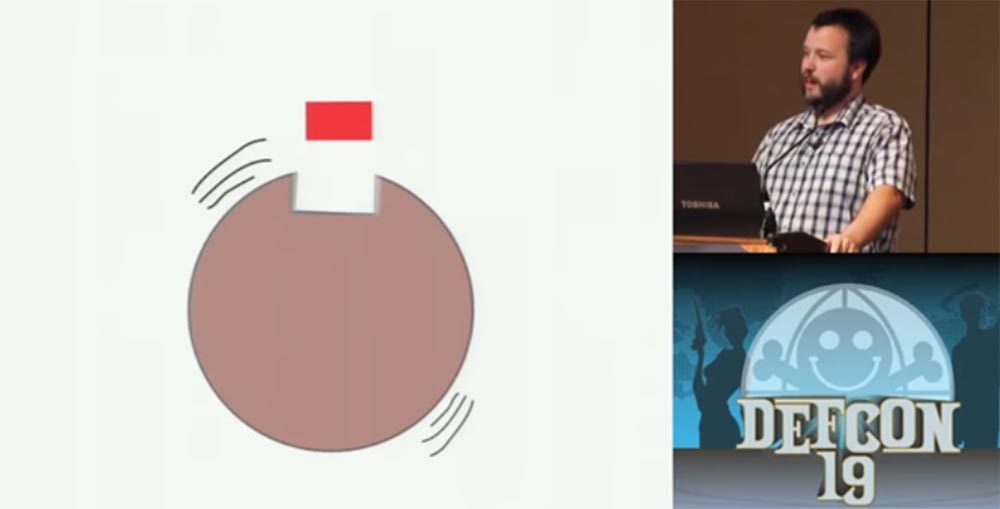
To test the vibration method of hacking, I chose a small fire-resistant "sapphire" safe weighing 30 kg. I took it apart to learn how the lock works. On the slide, you can see that the striker is not located on top, but a little to the side. Therefore, I turned the safe up so that it was on top and after the wheels from the vibration slit up, sank into this common groove.
When I tell people about hacking methods using traditional tools, I say that often we already know enough information about the castle we are going to “get down to”. We know the key information, the depth of the key bar cutouts, we know that this is a system with a master key, and so on, and we store all this information in memory. If we approach the castle, then we can say: “Oh, this is Schlage Primus, a door lock with spring-loaded studs produced by the company“ Shlag ”!”. You know what its vulnerability is and what kind of tool you need to use.
You can find the schemes of this lock, the patents used, you can even buy it to figure out how it works. You can see at what angle the locking plate is located, and if it is an external safe that is not bolted to anything, you can turn it to the desired angle.
There is an interesting story about a warship and castles, in fact, two stories. The essence of the first was that safes opened on all decks of a ship by themselves, there was even a theory about the ghost that does it, but the reason was that under the influence of shipboard vibration and water turbulence, the safes opened spontaneously. I do not know how true this is, because it turns out that it is good enough to shake the safe so that the locking bar falls into the slots and the lock opens.
And the second story tells about a fantastically beautiful young Russian lady who was invited to a warship so that she could take a little cruise. She turned to a young naval officer, they say, it’s so wonderful here, but I’m a little worried about my jewelry, they belonged to my grandmother, can I give them to you so that you can hide them in a safe place. The officer took her necklace and hid it in his safe. Later she came to this safe with a sheet of paper, then came back again, opened the safe and took everything from there, because in fact this sheet of paper was an X-ray film, and its necklace was radioactive. In general, as she received the imprint of the lock on the film and was able to open the safe.
There are a few interesting things that I want to show you and show how they work. I have no slides on this topic, so I will show you everything "live".
You see in my hands the usual car "janitor".

Inside this “janitor” are two fantastically strong, resilient and flexible steel plates that can be used to make master keys. If you are patient enough, you can grind them by hand, if patience is not enough, you can use the grinding wheel for $ 10 and quickly make your tool for hacking. Before you leave here and start making your master keys from the “janitor”, I want to tell you how to disassemble it. It's simple - first pick up the gum on the edge of the wiper for the middle and tear it down towards the other end, and you get two beautiful strips of spring steel. If you try to pull out these plates without removing the rubber from them, they will turn into a stretched bow and can harm you, so be careful.
Next, I'll show you the master lock 175, this is a coded digital lock. I'm going to open it very quickly, and then tell you how to do it.
Skyler inserts a lock pick into the lock, and it opens in just a second.Yes, exactly as I showed! So, we are experienced burglars, so we can approach the process of hacking in various ways. «» , , , - .
, . , , . – , . «» , , .
, , . , , . , , , - . , , , .
, – «», . , — , , .
, , , «» 9. – , , , . , , , , . «», , .
, , , . , - , , , .
, , . , , , . , – .
. - « ». . «», . , , , . , , , , , , .
– , .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends,
30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? 2 Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 $249 ! Read about
How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?