
Hacking game consoles is a favorite occupation of hackers of various kinds (here this term is used without negative overtones). This is done mainly in order to allow manufacturers to upload images of games on manufacturers' consoles without having to buy the original. Console manufacturers, in most cases, block any other possibility to play, except for licensed disks or files downloaded from specialized directories.
Some consoles are easily cracked, others are more complicated. So far, the strongest of all is resisting the cracking of PS Vita with an updated firmware. Most of the other consoles have already been hacked. Now craftsmen got to the Nintendo Switch.
The other day an exploit was published on the network for Nvidia Tegra X1 systems, which currently cannot be blocked. The exploit is developed by gland specialist Kathryn Temkin and the ReSwitched team. The developers of the vulnerability called it Fusée Gelée, see the software code
at this link .
According to the authors of the project, this exploit is a real “holy grail” of exploits for game consoles. It uses some vulnerability in Tegra X1 platform USB recovery mode. Working with this problem, the developers have learned how to install a custom bootROM. Sending an argument with an incorrect “length” for launching an incorrectly specified USB procedure at a certain moment. Thus, the user can force the system to request 65535 bytes. A buffer overflow occurs in the bootROM, which allows you to copy the data needed for hacking into a protected part of the memory.
The most difficult part in all this is to make the system go into USB recovery mode. In order not to open the console, you can simply short a certain pin on the right connector Joy-Con. The team has released a special device that allows you to do this without any problems. Actually, it is not even a device.

You can do on their own, using just a piece of wire stuck in the right places console. In this case, the system also goes into the desired mode.

The most interesting thing about this exploit is that it cannot be blocked by downloading from the Internet and installing a software patch. The fact is that the bootROM cannot be modified after the Tegra chip leaves the factory. This is a great option if the bootROM is well protected. In this case, manufacturers are unlikely to be able to do if the user modifies the software in any way.
The manufacturer will be able to do something with those consoles and chips that have not yet been released. But remember that the Nintendo Switch has already sold millions of copies around the world. More specifically, 14.8 million systems that are vulnerable to hacking have already been sold.
But Nintendo is still able to "annoy" the owners of the hacked consoles. The fact is that you can determine the "original" or modification without any problems. And in this case, the company can block the possibility for hacked systems to log on to their servers. Then Nintendo can even block the network functions of the console. In principle, the company had previously done something similar with Nintendo 3DS, after learning how to hack them.
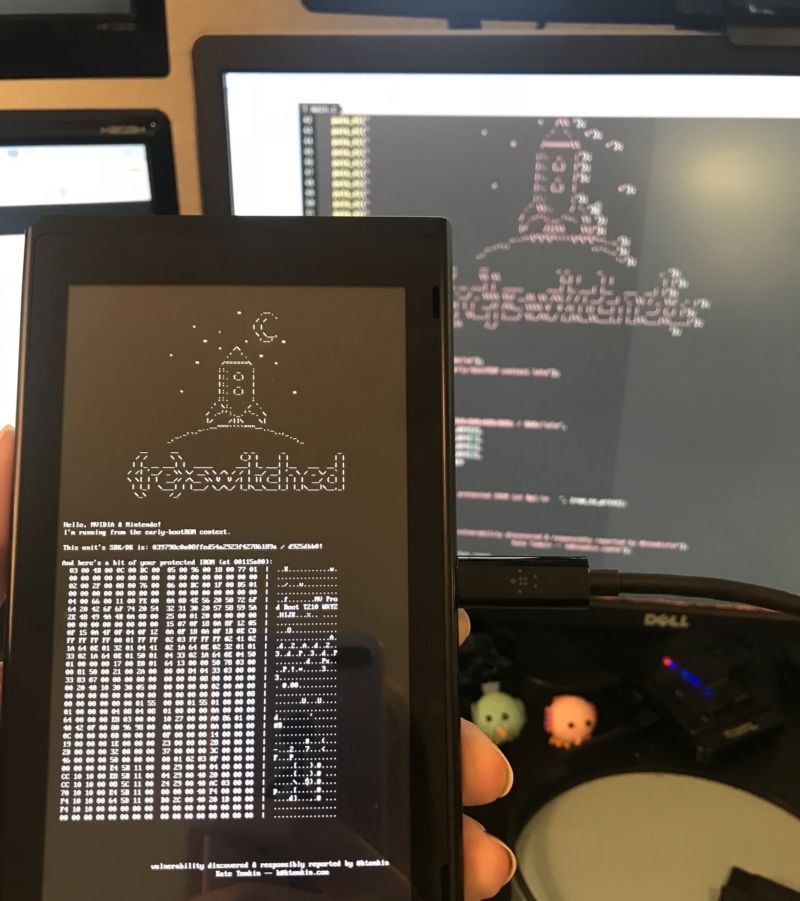
Now the exploit itself works, but this is only proof of concept. The developers have proven that all consoles are vulnerable, but have not gone further. A large amount of technical information about the exploit will be published on June 15th. In the summer, users will receive information about the practical use of the console. Work continues on the Atmosphere custom loader.
Interestingly, the authors of the exploit earlier warned Nvidia and other manufacturers of "iron". At the moment, only part of the data is published because “the exploit can be used to the detriment of the users themselves”. In order to show the reality of the development, a screenshot with the Dolphin emulator, which is running on the Nintendo Switch and playing the Legend of Zelda: Wind Waker, was published.
By the way, there is evidence that the developers of the named team are not the first to propose the idea of an exploit. There were (and probably will be)
other teams that offer about the same thing.