Modern capabilities to detect the enemy and high-precision armament force the military to high mobility and quick decision-making. To do this, you need to receive information from different sources in real-time mode and promptly share it with all units involved in the operation. One of the ways to solve this problem was the use of solutions based on the Internet of Things, called Internet of Battle Things (IoBT).

Captured by smart devices
Using the concept of the Internet of Things (Internet of Things, IoT) in the armies of many countries of the world has become a technological trend of the last decade, a kind of indicator of the modernity and innovativeness of their armed forces. At the same time today it is already difficult to surprise with flying or ground unmanned vehicles and robotic combat vehicles. As the emergence of new technologies, the range of tasks and capabilities of military "smart devices" is expanding rapidly.
It can be said that IoT began to penetrate into all possible aspects of military affairs, ranging from solving the most difficult tasks of high-precision detection and destruction of the enemy, and ending with monitoring the physical condition of a particular serviceman.
Today, potential areas of “military” use of IoT-technologies already include logistic support for troops, monitoring the current situation at the scene of a clash for various levels of military personnel (top commanders, unit commanders, a separate fighter), medical support (on the battlefield and in a normal situation) .

IoT devices are also widely used in various training and training programs for military personnel in the virtual battle mode.
The next decade will bring dramatic changes in the military sphere to the approaches to the conduct of hostilities and everything that goes with them, ranging from military logistics to directly striking the enemy. TVD will be densely crammed with various devices that perform a huge range of basic and auxiliary combat missions. These are devices, sensors, wearable devices, “smart” weapons, vehicles, robots. All of them will be interconnected with each other and the soldiers, and each, as far as their “intellectuality” is concerned, will act as sources of information that must be analyzed in order to come up with the right decision and issue a command to the operating units or equipment.
Note that the IoT militarization plan was raised quite high by the Pentagon when the agency began developing theories of “network-centric warfare” and “multi-domain battle”. They provide a completely new way of conducting military operations, in which all the participants (equipment, manpower, headquarters, etc.) are connected by a single information network.
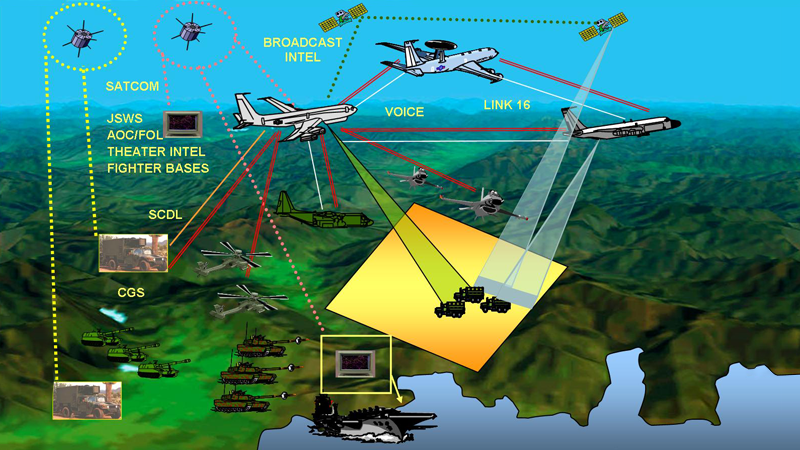
In this case, it is not about connecting various military networks in order to increase the efficiency of specific operations, but the creation of a global network that allows you to simultaneously work on all theaters, including in cyberspace. All technical devices in service should be connected to one common system, starting with the UAV sensor and ending with a wearable device in the soldier’s ammunition. Moreover, the emphasis is on unification not within a separate unit or type of troops, but across all armed forces. It is assumed that the integration into the global network will give commanders the ability to quickly make decisions on the conduct of offensive, defensive and other actions in the theater of operations.
American "IoBT-dream"
Today, the unconditional leadership in the application of IoBT and the development of new solutions with its use belongs to the American army. Thus, it is known about the successful trials of multi-purpose aircraft capable of receiving and transmitting large data streams from combat "smart" devices and other equipment working in their visibility zone. The ATAK (Android Tactical Assault Kit) mobile application is also actively used, which allows you to accumulate data in real-time mode and overlay them on the well-known Google Maps. In the combat zone, this solution is used for communication of the gunner to the target, the pilot of the aircraft or the UAV operator.

However, the Pentagon plans to replace this and other similar systems with more modern military IT systems as part of a radical transformation, and also to eliminate a lot of different local networks that do not communicate with each other, creating one all-army instead.
And the US Navy even conducted exercises on disembarking robotic combat vehicles, with special emphasis on testing communication channels and the interaction of unmanned systems both on water and land, and in the air. Also, successful tests were conducted of a new type of armor, which, after entering it, could inform other equipment, the soldier and the command center involved in the operation, about the power and direction of the shelling.
A technical breakthrough is the use in combat conditions of the capabilities of smartphones and tablets. These devices can be enabled by the Nett Warrior system developed by the Americans. With its help, the unit commander has the opportunity to exchange information vertically and horizontally, which significantly increases awareness of the situation in the battle zone with the enemy. In addition, the presence of GPS allows you to mark the location of soldiers on the map, which is depicted in the eyepiece (display) attached to the helmet, as well as receive updated maps of the area and other information from the command center.

Of course, using Nett Warrior implies the provision of mobile 4G communications in the area where the operation takes place.
Given the opportunities that are opening up, the Pentagon and the command of the armed forces of the United States have repeatedly stated the need to accelerate the processes of creating and implementing new technologies in the military sphere. However, there are quite a few problems on this path, and many of them are related to the complexity of processing, analyzing huge arrays of heterogeneous information and the need for its metered distribution to users. Most likely, only AI-technologies will be able to cope with this task, and already tomorrow's level.
In the zone of special attention - vulnerabilities
The benefits of IoBT, attracting the attention of the military, side by side with a number of vulnerabilities that developers have to overcome. One of the factors of the point-of-view use of IoBT in military affairs is the need to create special devices with a high degree of protection, often based on “civilian” models, as can be seen from the example of smartphones and tablets. Today, combat operations are becoming increasingly difficult, including technically, but the requirements for security and the preservation of the lives of soldiers are also increasing. Therefore, any mobile or network application that ensures the operation of IoBT devices, as well as they themselves, should be maximally protected from outside interference.
Attempts by the US military to develop a global network also come up against the problems of vulnerability of IoBT networks, which, no less than military equipment or soldiers, can become the object of attack.

The vulnerability of individual elements of the system can be triggered by various methods available to the enemy or hackers: physical and network hacking, wiretapping, EW, directed energy, destruction of the WOK and IP, etc.
Therefore, the military faces a difficult task - to ensure that when adopting IoBT devices, there is no way for them or the network to manipulate, theft, disruption of data flow or physical destruction. It is not easy to do this now, given the attitude of many manufacturers of “smart” devices to ensuring their security, as well as the close interweaving of fixed, mobile and satellite networks, which contributes to the presence of a mass of entry points and unprotected places. So, the military departments will sooner or later have to work with suppliers and manufacturers of IoBT devices in order to force them to introduce more reliable safety standards.
Of course, the use of smart devices in the military sphere is already an irreversible process. However, unlike “civilian”, IoBT-devices are subject to more serious risks due to participation in the confrontation between the warring parties. Using their vulnerabilities, it is possible to inflict significant damage to the enemy, after all, “smart weapons”, such as, for example, modern tanks or missiles and many others already have access to the Internet.

Today, the security problems of IoBT, like IoT as a whole, are gradually being solved through the use of encryption technologies, including Blockchain. And as experts predict, in the near future, management of the “military” Internet of Things and automation of combat operations may be partially assigned to artificial intelligence.